So, I've been using the home version of UTM for many, many years. All has been good, but now I'm hitting the IP limit (Thanks IoT!).
So I've installed XG alongside the original UTM VM with an interface on my main network, a private link from the XG WAN port to an input in the UTM, and a separate Port connected to a VLAN.
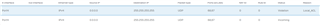
Pointing a PC to the XG as the router, works absolutely fine. Even on the VLAN interface, it works great. But... ONLY if it has a static IP. When I try to use the DHCP relay function on the XG, I get an error in the pCAP as shown below. This shows port 68,67 status viaolation, reason Local_ACL
I've added the DHCP relay to the VLAN port and pointed to the DHCP server. I also tried adding various Any<>Any rules in the firewall config and tried (without success) to add a DHCP application to the Device Access (can't seem to find a way to add DHCP to this).
As an aside, if I enable an XG DHCP server on this same VLAN port, I get an IP address, so all my VLAN tagging and network access outside the XG is fine.
With the UTM, it was so much simpler....and it worked fine...
Any idea what I am missing?
Thanks in advance.
This thread was automatically locked due to age.