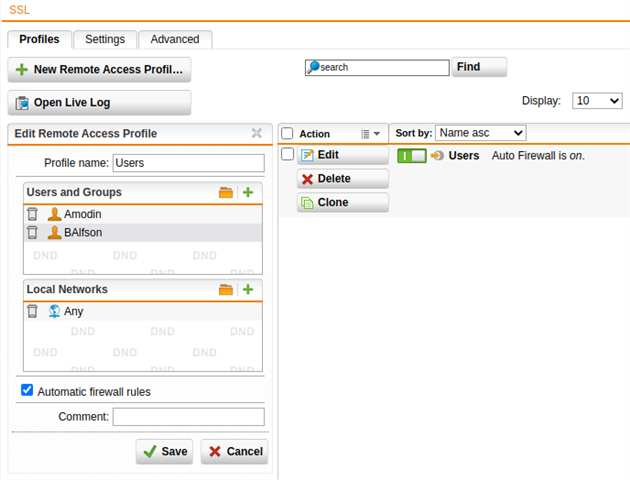
Setting up SSL VPN.
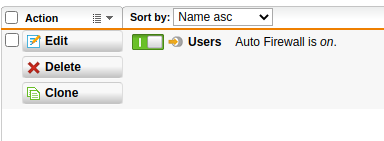
Getting the default drop on the SSL VPN port, but a profile is turned on.
2021:10:04-14:23:35 pdx ulogd[5227]: id="2001" severity="info" sys="SecureNet" sub="packetfilter" name="Packet dropped" action="drop" fwrule="60001" initf="eth4" srcmac="00:cc:fc:60:c4:22" dstmac="b8:cb:29:b8:28:99" srcip="208.79.209.138" dstip="xxx.xxx.xxx.xxx" proto="6" length="64" tos="0x00" prec="0x20" ttl="45" srcport="58673" dstport="8443" tcpflags="SYN"
It's like the automatic firewall rule is not kicked in; however, WAF opens a port as expected.
What am I missing?
-edit:
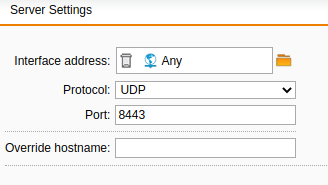
Thinking it "might" be my ISP, i moved WAF to 8443 and the port is open to the outside world.
But regardless of the port (443, 8443) SSL-VPN is not opening a port to the outside like it should.
Is there some other setting I've forgotten about to enable SSL-VPN?
This thread was automatically locked due to age.