Hi, I've setup Remote Access for 2 user
My lan is 192.168.1.0/24
Everything is OK if the user network is different than mine
How to make it work if user network is the same as mine?
I searched everywhere but I did'nt found any documented solution to make it work
The only example I found is about to connect two UTM with the same network range (https://support.sophos.com/support/s/article/KB-000034290?language=en_US), but I don't know if it can be applied to my case....i tried, but no success. Can anyone help me please?
I created:
2 New Network definition:
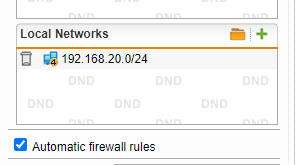
FakeNetwork : 192.168.20.0/24
MyNetwork: 192.168.1.0/24
2 NAT 1:1
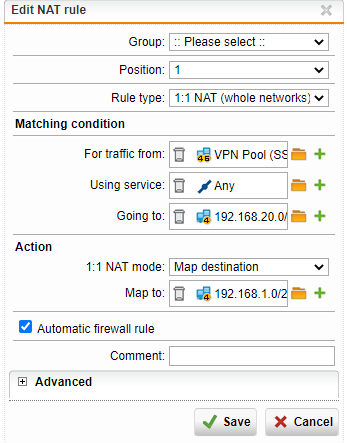
1:1 NAT MAP SOURCE:
Traffic selector: VPN Pool (SSL) -> any -> MyNetwork
Source translation: FakeNetwork
1:1 NAT MAP DESTINATION
Traffic selector: FakeNetwork -> any -> VPN Pool (SSL)
Destination translation: MyNetwork
Thank you for any help
Rudy
This thread was automatically locked due to age.