Hi there,
we use an UTM450 running in a cluster and also SSL VPN for our clients. Normally around 30-50 users are connected but during corona lockdown we had several users more (up to 100-120). Since then the VPN-performance got hotrrible. Lots of ping losses, it was unusable for most users. We had a call with sophos and they recommended to lower the authentication algorythm and switch from tcp to udp because our settings are not best practise.
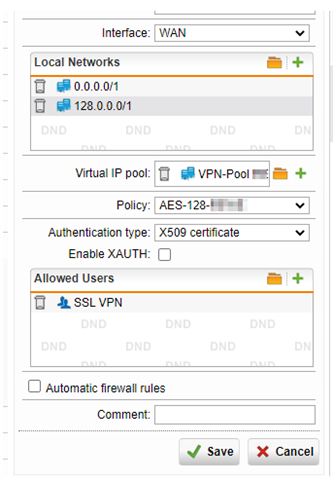
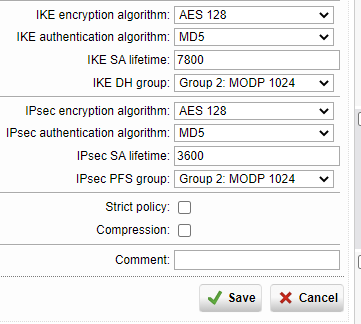
Current settings are:
TCP
Encryption algorythm AES 256-cbc
Authentication algorithm Sha 512
Key size 1024 bit
Out WAN nic has 500 Mbit. We only use one WAN-interface.
We didn't do this because this due to the fact that our users are no local admins we had to reinstall VPN profiles manually. We currently also use a different VPN only appliance for dial in then and kept only few users on the sophos.
Unfortunately the situation now is, that also the performance of IPSEC tunnels are degrading with lots of ping losses and the SSL client VPN istn't working well either with only 30-50 users.
We are now thinking again about switching the SSL VPN settings but I am not sure if this will really solve all problems.
Any other opininions are highly appreciated.
Thanks and regards
Marcel
This thread was automatically locked due to age.