Sorry but I have to unlock a user for Facebook inside our company network.
We have blocked facebook for all, which works fine.
Now just one marketing user need facebook for work and i want to whitelist this user so he can do his work on fb.
We do not use any AD-User Authentication and want it to stay this way. Anyway, users do authenticate over SSL-VPN with email and password, so i tried to unblock the VPN-User cause he should be clear authenticated to the network. (VPN connection works inside or outside the company without problems.)
Is there a way to whitelist a User simply with his IP or his VPN-User Account inside the network?
Under WEB Protection > Application Control > we have a Rule that blocks all facebook users. (works)
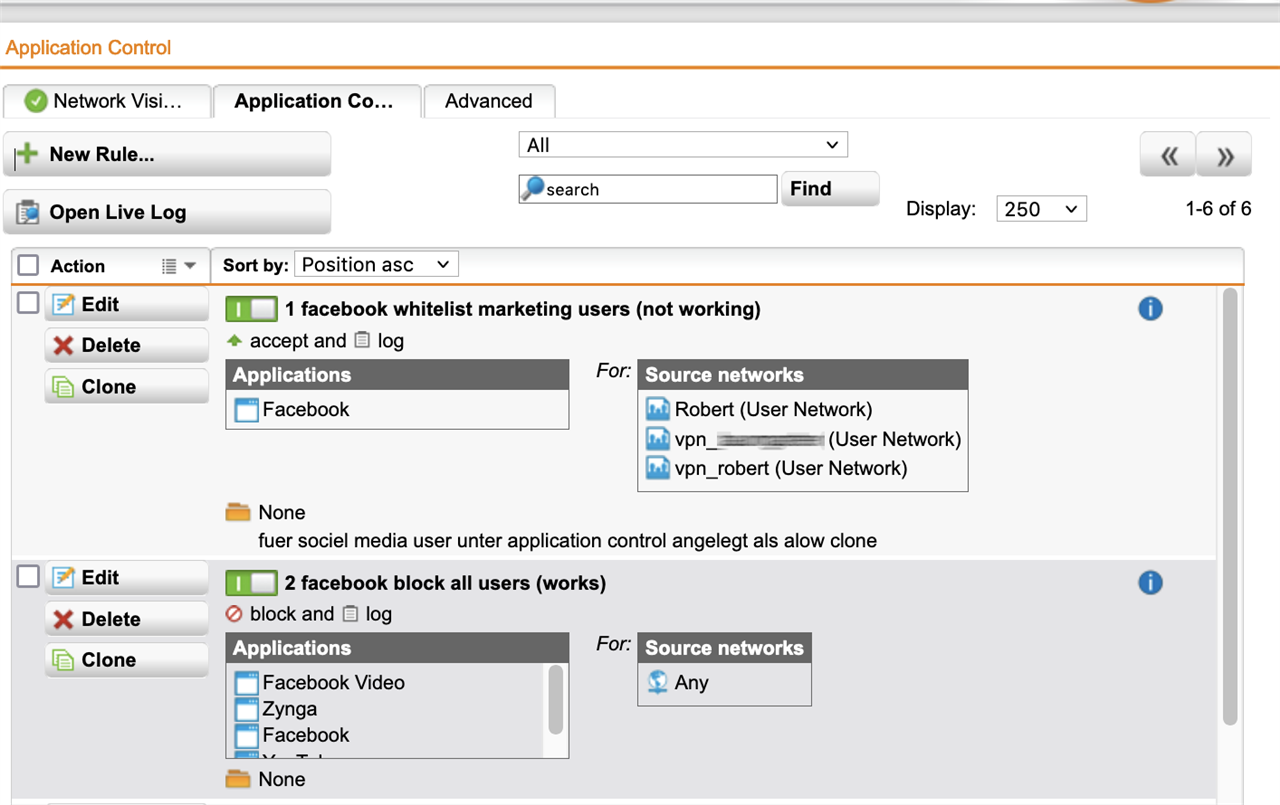
I tried to add at the same place a Rule with whitelist (allow) the specific VPN-User and a Testuser (Robert) and put them on top, but facebook is still blocked when the specific user is connected with VPN. (See Screenshot) Just when i deactivate the 2nd Rule (facebook block all users) facebook is loading again, but then for all users.
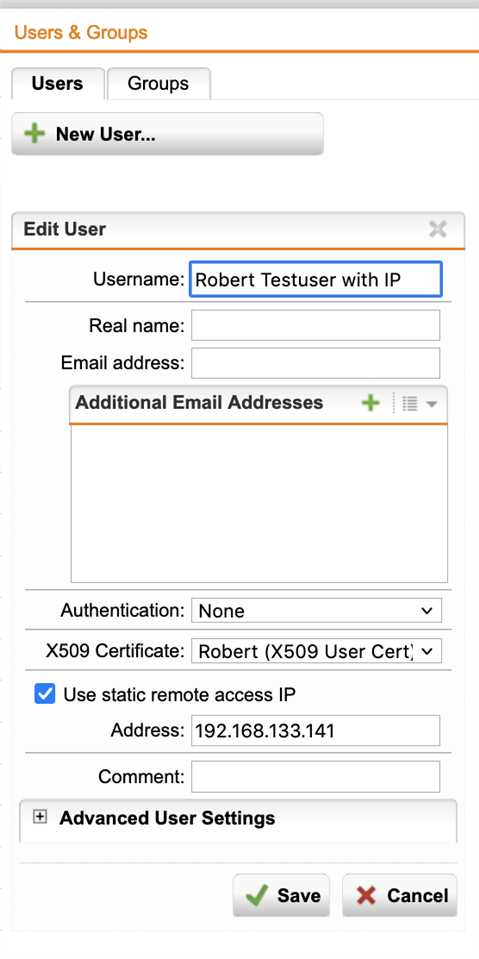
I also added for testing a new user and gave him his Laptop internal IP adress (Robert) but it did not work also for this user.
Why is the new "1 unblock marketing" rule not working inside Application Control or is there a better way to handle this?
This thread was automatically locked due to age.
