My SEIM (AlienVault) is detecting Mirai inbound activity.
Eg:
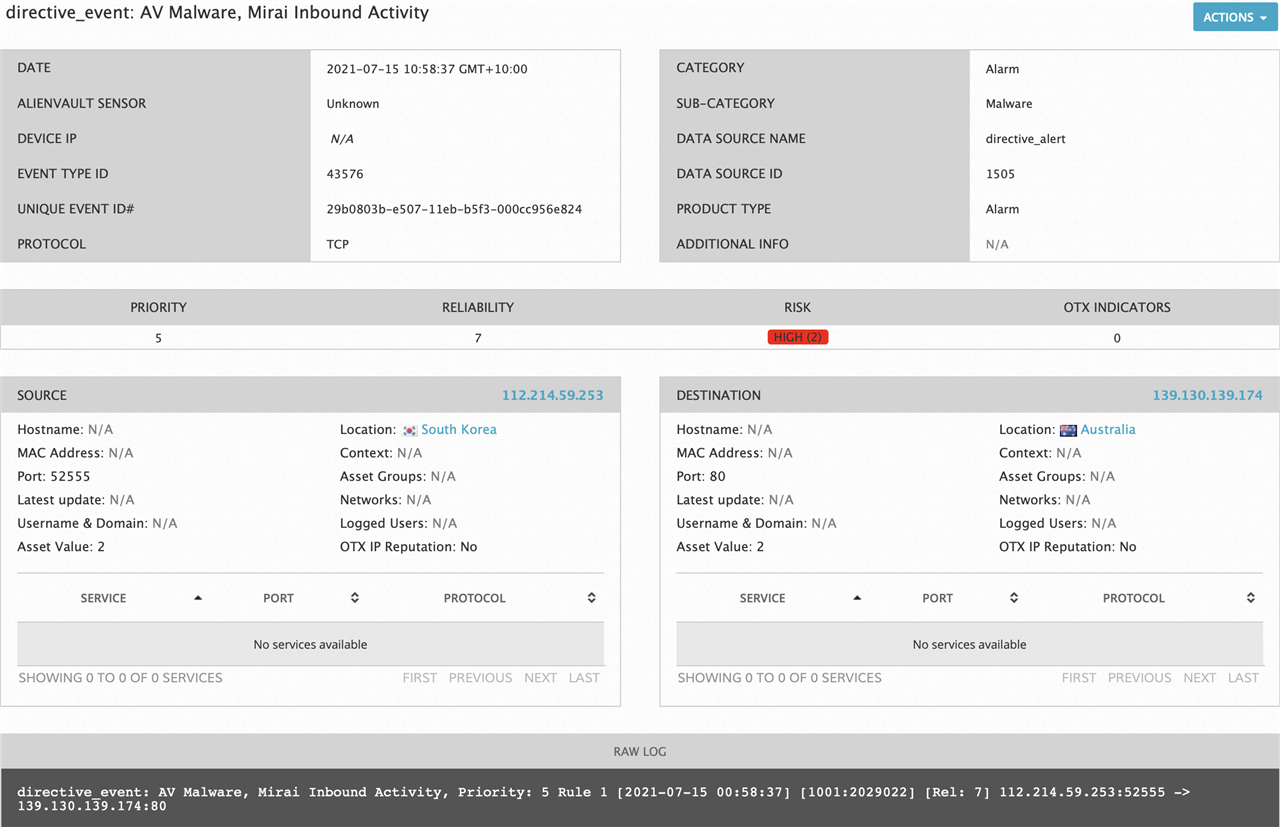
How can these be stopped at the UTM?
Eg can it get known botnet addresses from the Open Threat Exchange (OTX)?
Thanks, James.
This thread was automatically locked due to age.
James, I guess I'd ask why this traffic was allowed through the UTM in the first place instead of letting it be default dropped...
Cheers - Bob
I see that now, James. So it's the hidden, automatic rule created by the configuration daemon. If you don't want to use Amodin's suggestion, the only other solution is to create a blackhole DNAT for the offending IPs/subnets. You're right that there's no option to use OTX. Mirai attacks can come from 100,000 IPs, so I doubt that even OTX would be a solution. What do you have behind WAF that might be vulnerable to a mirai malware infection?
Cheers - Bob