Hello guys,
Trying to get a IPSec tunnel between our HO UTM and a USG we got for testing. Currently have it on my home network, seeing if I can get a IPSec tunnel going.
In logs, I keep getting: "MyWANIP":500: ignoring informational payload, type NO_PROPOSAL_CHOSEN
As far as I can tell, everything seems to be okay. Here's what I have configured on the UTM:
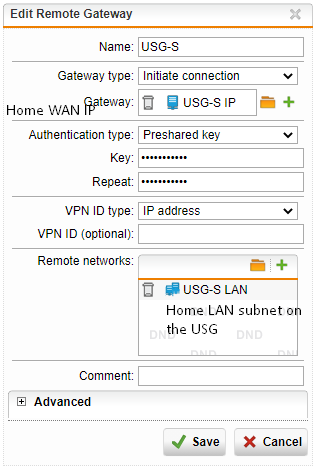
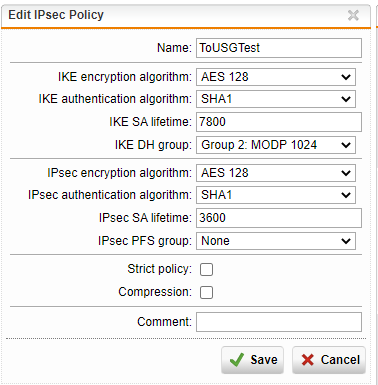
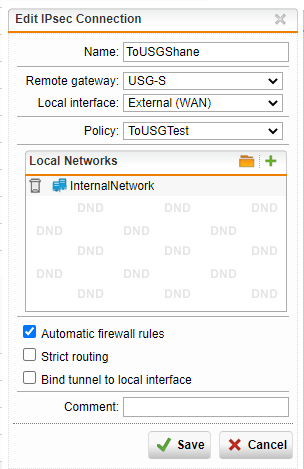
On the USG side, here is what is configured:
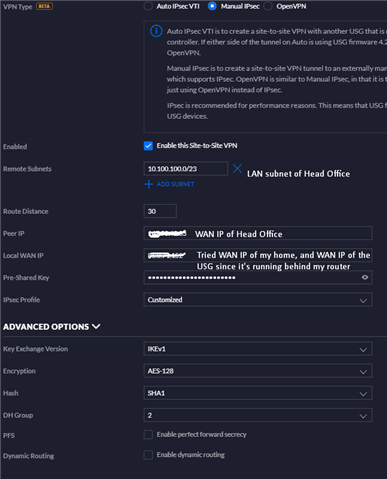
I think I might need a fresh set of eyes on this, I can't figure out the issue. I was initially thinking it might have been ports 4500 and 500 being blocked, but can't see any entries on the firewall log pointing to that. We also have L2TP over IPSec enabled, with users remoting in. The above message is what shows up on the IPSec VPN log for the UTM that relates to my home WAN IP.
Thank you
This thread was automatically locked due to age.


