I just discovered a security flaw in UTM OTP. Here is the problem.
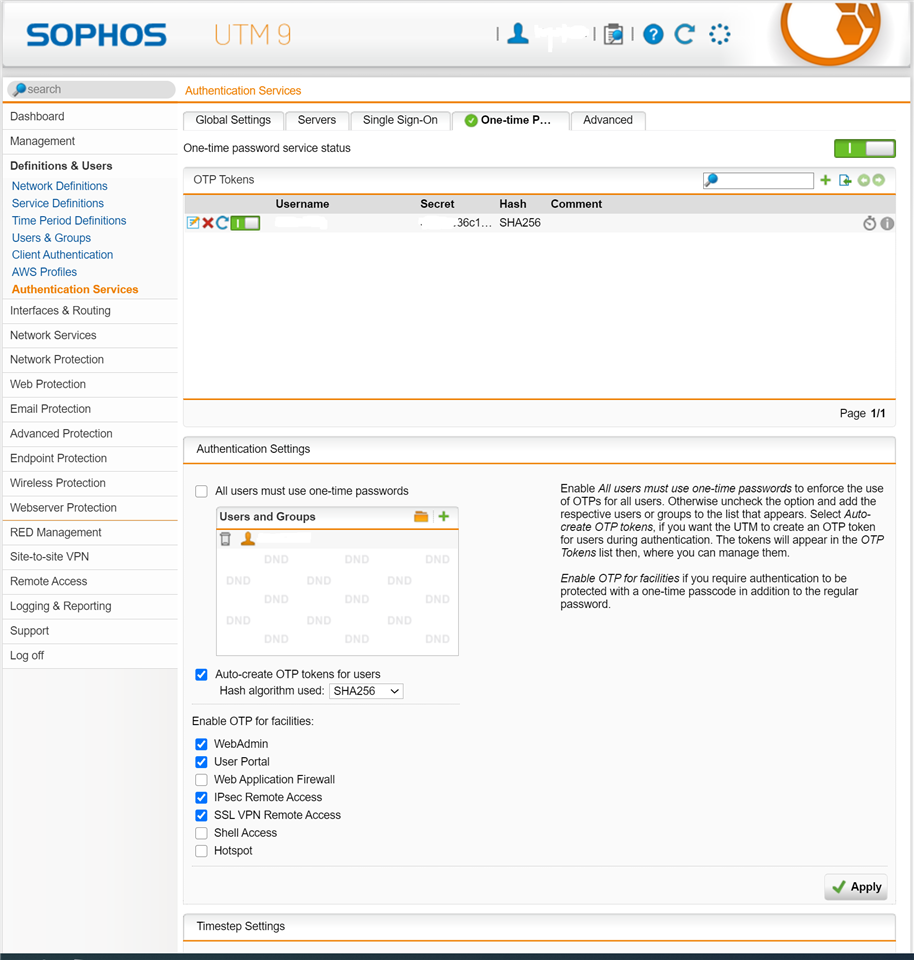
You enabled the OPT and enabled OPT for facility "User Portal" and "WebAdmin".
You sign in to the User Portal at the first time with password only, you get the QR code immediately. This is normal. You scan the QR code with the authenticator app.
You sign in to the User Portal again with your password following the 6 digit OPT code from the authenticator app. You got in the portal. This is also normal.
You sign in to the WebAdmin with the password only, no OPT code, your access is denied. This is normal, since the OPT code is generated. You need password & OPT to sign in.
You sign in to the WebAdmin with the password following the OPT code, you are granted access. This is normal. You can only sign in with password + OPT.
Here is the problem:
You sign in to the User Portal again with only password, no OPT code. You got in, and QR code is displayed on the screen again.
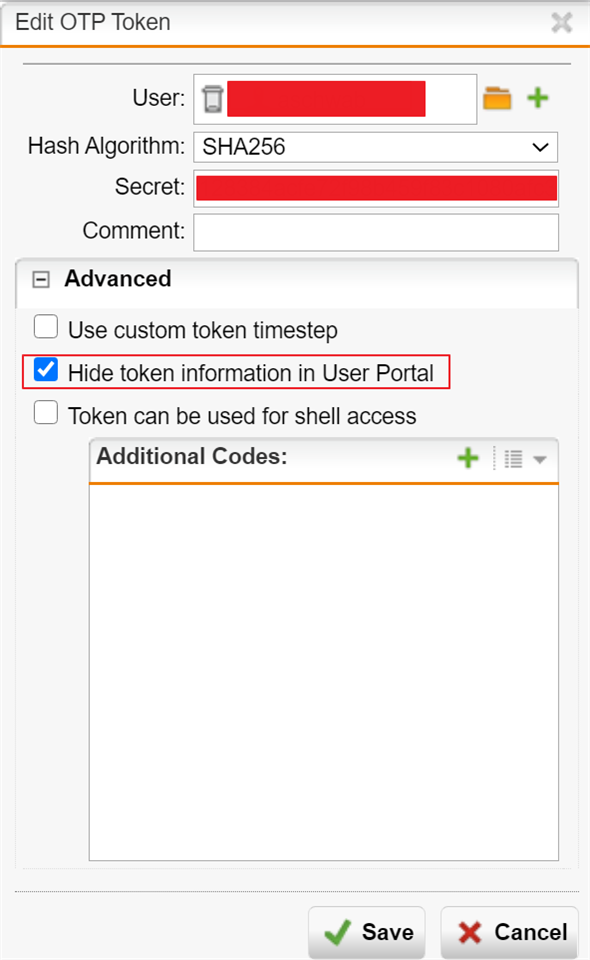
This is the security flaw. When an account has no OPT yet, the first time you sign in User portal, it displays the QR code is normal since you don't have the OPT code yet. Once the OPT code is generated and assigned to an account, if you sign in to the User Portal the second time without the OPT code, the system should deny the access instead of display the OPT code again. Otherwise, if the admin account password got compromised, the hacker can simply login to the user portal with only the password and obtain the OPT code. After that the hack can use the password and the OPT code to sign in the WebAdmin.
The software should only display the OPT code when the account has no OPT yet. Once the OPT code is generated at the first time the account login to user portal, it should require OPT to the user portal when the user try to login the second time. Otherwise, it will defeat the purpose of the OPT. Sophos needs to fix this flaw ASAP.
This thread was automatically locked due to age.