Hi,
we have an existing Ipsec VPN from oure Sophos to an customer with an Juniper device. No we have moved to an new location and also have an new provider (Vodafone). I changed the WAN IP where possible, and contacted our customer because they also needed to change my WAN IP. Somehow it doesnt work anymore,
Our Logfile says: NO_PROPOSAL_CHOSEN. On the Juniper site we get theres no IKE ID send from the Sophos device.
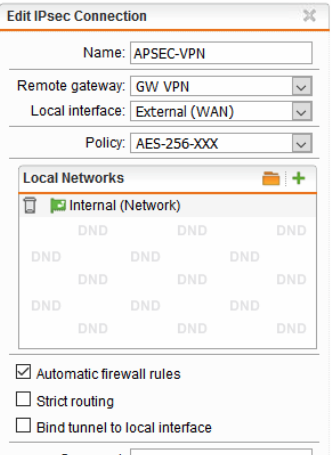
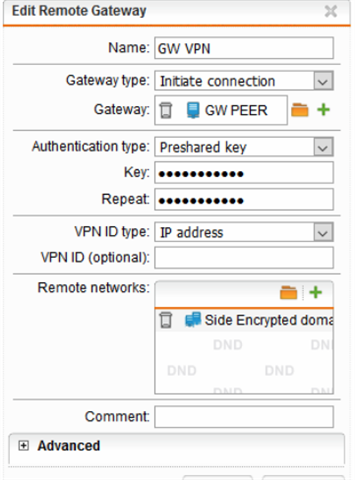
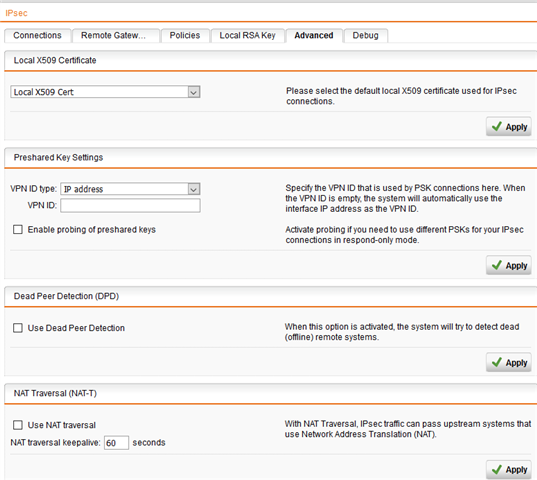
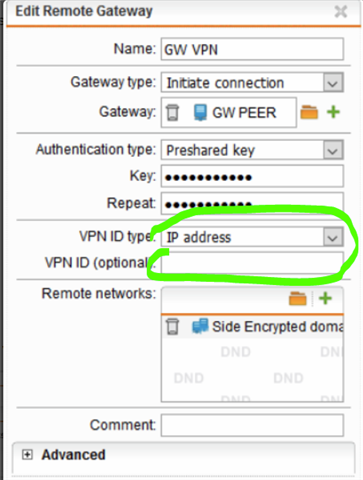
The policys are identical, i tried in the advanced to enable/ disable the DPD en also the NAT-T, no succes.
we have no idea what can be wrong.
See logfile below of the Sophos
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | *received whack message
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | from whack: got --esp=aes256-sha2_256;modp2048
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | esp proposal: AES_CBC_256/HMAC_SHA2_256, _128; pfsgroup=MODP_2048;
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | from whack: got --ike=aes256-sha2_256-modp2048
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ike proposal: AES_CBC_256/HMAC_SHA2_256/MODP_2048,
2021:02:19-15:54:36 bic_term_srv pluto[11501]: added connection description "S_REF_IpsSitDhlapsecvp_0"
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | 10.11.12.0/24===93.117.220.27[93.117.220.27]...165.72.209.21[165.72.209.21]===198.141.240.0/22
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ike_life: 86400s; ipsec_life: 3600s; rekey_margin: 540s; rekey_fuzz: 100%; keyingtries: 0; policy: PSK+ENCRYPT+TUNNEL+PFS
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | next event EVENT_REINIT_SECRET in 3600 seconds
2021:02:19-15:54:36 bic_term_srv pluto[11501]: |
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | *received whack message
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | creating state object #1 at 0x9d50ce8
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ICOOKIE: 85 44 6b 2b 6c 4e 68 af
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | RCOOKIE: 00 00 00 00 00 00 00 00
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | peer: a5 48 d1 15
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | state hash entry 27
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | inserting event EVENT_SO_DISCARD, timeout in 0 seconds for #1
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | Queuing pending Quick Mode with 165.72.209.21 "S_REF_IpsSitDhlapsecvp_0"
2021:02:19-15:54:36 bic_term_srv pluto[11501]: "S_REF_IpsSitDhlapsecvp_0" #1: initiating Main Mode
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | **emit ISAKMP Message:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | initiator cookie:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | 85 44 6b 2b 6c 4e 68 af
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | responder cookie:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | 00 00 00 00 00 00 00 00
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | next payload type: ISAKMP_NEXT_SA
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ISAKMP version: ISAKMP Version 1.0
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | exchange type: ISAKMP_XCHG_IDPROT
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | flags: none
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | message ID: 00 00 00 00
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ***emit ISAKMP Security Association Payload:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | next payload type: ISAKMP_NEXT_VID
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | DOI: ISAKMP_DOI_IPSEC
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ****emit IPsec DOI SIT:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | IPsec DOI SIT: SIT_IDENTITY_ONLY
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ike proposal: AES_CBC_256/HMAC_SHA2_256/MODP_2048,
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ****emit ISAKMP Proposal Payload:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | next payload type: ISAKMP_NEXT_NONE
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | proposal number: 0
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | protocol ID: PROTO_ISAKMP
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | SPI size: 0
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | number of transforms: 1
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | *****emit ISAKMP Transform Payload (ISAKMP):
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | next payload type: ISAKMP_NEXT_NONE
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | transform number: 0
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | transform ID: KEY_IKE
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ******emit ISAKMP Oakley attribute:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | af+type: OAKLEY_LIFE_TYPE
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | length/value: 1
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | [1 is OAKLEY_LIFE_SECONDS]
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ******emit ISAKMP Oakley attribute:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | af+type: OAKLEY_LIFE_DURATION (variable length)
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting 4 raw bytes of long attribute value into ISAKMP Oakley attribute
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | long attribute value
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | 00 01 51 80
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting length of ISAKMP Oakley attribute: 4
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ******emit ISAKMP Oakley attribute:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | af+type: OAKLEY_ENCRYPTION_ALGORITHM
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | length/value: 7
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | [7 is AES_CBC]
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ******emit ISAKMP Oakley attribute:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | af+type: OAKLEY_HASH_ALGORITHM
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | length/value: 4
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | [4 is HMAC_SHA2_256]
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ******emit ISAKMP Oakley attribute:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | af+type: OAKLEY_KEY_LENGTH
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | length/value: 256
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ******emit ISAKMP Oakley attribute:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | af+type: OAKLEY_AUTHENTICATION_METHOD
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | length/value: 1
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | [1 is pre-shared key]
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ******emit ISAKMP Oakley attribute:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | af+type: OAKLEY_GROUP_DESCRIPTION
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | length/value: 14
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | [14 is MODP_2048]
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting length of ISAKMP Transform Payload (ISAKMP): 40
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting length of ISAKMP Proposal Payload: 48
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting length of ISAKMP Security Association Payload: 60
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | out_vendorid(): sending [strongSwan]
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ***emit ISAKMP Vendor ID Payload:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | next payload type: ISAKMP_NEXT_VID
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting 16 raw bytes of V_ID into ISAKMP Vendor ID Payload
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | V_ID 88 2f e5 6d 6f d2 0d bc 22 51 61 3b 2e be 5b eb
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting length of ISAKMP Vendor ID Payload: 20
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | out_vendorid(): sending [Cisco-Unity]
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ***emit ISAKMP Vendor ID Payload:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | next payload type: ISAKMP_NEXT_VID
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting 16 raw bytes of V_ID into ISAKMP Vendor ID Payload
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | V_ID 12 f5 f2 8c 45 71 68 a9 70 2d 9f e2 74 cc 01 00
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting length of ISAKMP Vendor ID Payload: 20
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | out_vendorid(): sending [XAUTH]
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ***emit ISAKMP Vendor ID Payload:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | next payload type: ISAKMP_NEXT_VID
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting 8 raw bytes of V_ID into ISAKMP Vendor ID Payload
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | V_ID 09 00 26 89 df d6 b7 12
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting length of ISAKMP Vendor ID Payload: 12
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | out_vendorid(): sending [Dead Peer Detection]
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ***emit ISAKMP Vendor ID Payload:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | next payload type: ISAKMP_NEXT_NONE
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting 16 raw bytes of V_ID into ISAKMP Vendor ID Payload
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | V_ID af ca d7 13 68 a1 f1 c9 6b 86 96 fc 77 57 01 00
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting length of ISAKMP Vendor ID Payload: 20
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | emitting length of ISAKMP Message: 160
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | inserting event EVENT_RETRANSMIT, timeout in 10 seconds for #1
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | next event EVENT_RETRANSMIT in 10 seconds for #1
2021:02:19-15:54:36 bic_term_srv pluto[11501]: |
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | *received whack message
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | next event EVENT_RETRANSMIT in 10 seconds for #1
2021:02:19-15:54:36 bic_term_srv pluto[11501]: |
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | *received 102 bytes from 165.72.209.21:500 on eth1
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | **parse ISAKMP Message:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | initiator cookie:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | 85 44 6b 2b 6c 4e 68 af
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | responder cookie:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | 90 63 2e 18 f1 a7 58 9d
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | next payload type: ISAKMP_NEXT_N
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ISAKMP version: ISAKMP Version 1.0
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | exchange type: ISAKMP_XCHG_INFO
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | flags: none
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | message ID: c9 8c d7 4b
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | length: 102
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ICOOKIE: 85 44 6b 2b 6c 4e 68 af
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | RCOOKIE: 90 63 2e 18 f1 a7 58 9d
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | peer: a5 48 d1 15
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | state hash entry 11
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | state object not found
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | ***parse ISAKMP Notification Payload:
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | next payload type: ISAKMP_NEXT_NONE
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | length: 74
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | DOI: ISAKMP_DOI_IPSEC
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | protocol ID: 1
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | SPI size: 16
2021:02:19-15:54:36 bic_term_srv pluto[11501]: | Notify Message Type: NO_PROPOSAL_CHOSEN
2021:02:19-15:54:36 bic_term_srv pluto[11501]: packet from 165.72.209.21:500: ignoring informational payload, type NO_PROPOSAL_CHOSEN
Hope someone have any ideas.
regards, Dominique
This thread was automatically locked due to age.