Hello UTM Gurus,
I have been crawling the forum and looking at all the game server hosting threads that I can find but have not found an answer.
I recently spun up a dedicated Ubuntu server inside my network to host a server for myself and my friends. I was able to successfully configure a DNAT rule to allow connection to the server from the internet and my friend is able to connect to my server and play.
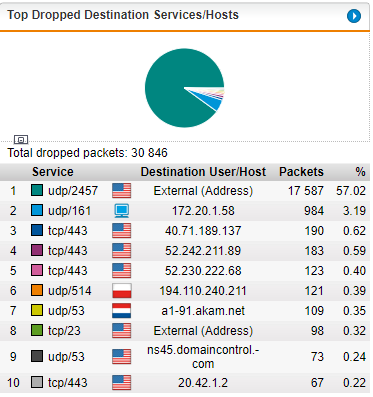
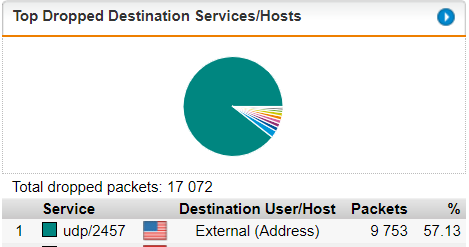
However, I am now getting A LOT of "Default DROP" hits in my Firewall Live Log from external IPv4 to external WAN IP on one of the ports used for the game/DNAT.
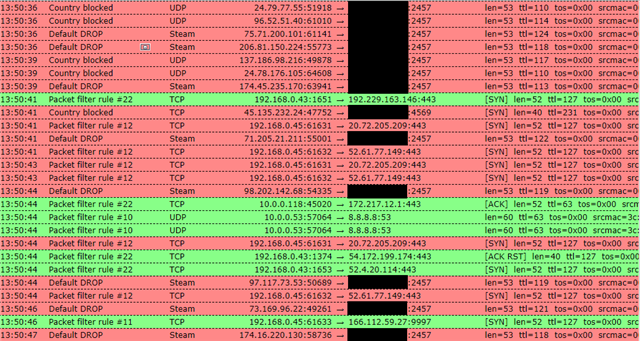
Live Log:
08:58:03 Default DROP Steam 76.84.56.154 : 58706 → MyWANIP : 2457 len=53 ttl=114 tos=0x00 srcmac=00:01:5c:b3:a6:46 dstmac=MyWANMAC
Corresponding Firewall Log:
08:58:03 sutm ulogd[19577]: id="2001" severity="info" sys="SecureNet" sub="packetfilter" name="Packet dropped" action="drop" fwrule="60001" initf="eth2" mark="0x32bf" app="703" srcmac="00:01:5c:b3:a6:46" dstmac="MyWANMAC" srcip="76.84.56.154" dstip="MyWANIP" proto="17" length="53" tos="0x00" prec="0x20" ttl="114" srcport="58706" dstport="2457"
DNAT Rule:
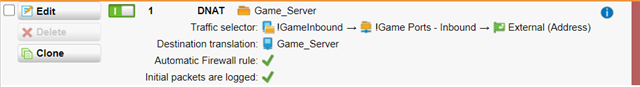
!GameInbound = NetworkGroup with allowed Networks. (my brother's public IP and my "Internal (Network)" to allow connection from my workstation)
!Game Ports - Inbound = Service group with UDP 1:65535 → 2456:2458 (ports used by game)
Am I doing something wrong here? Is this just the nature of hosting a server? It looks like the boundary is being protected but it sure is a lot of noise in the logs for "Steam" on that DNAT port 2457.
Where does the "Steam" label come from in the Live Log?
Thanks in advance!
This thread was automatically locked due to age.