Hello
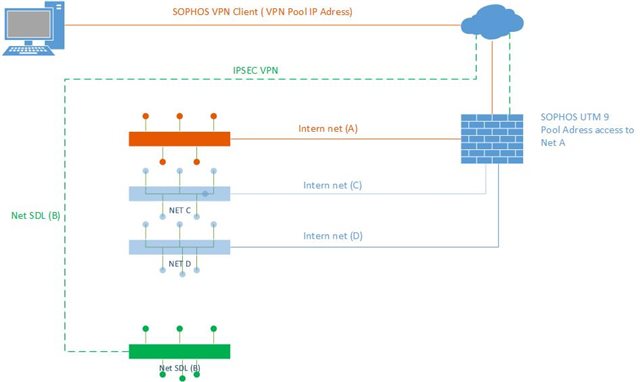
I run a UTM 9 and everything works quite well. But I have a question about a remote access configuration to two different networks over the same remote access connection.
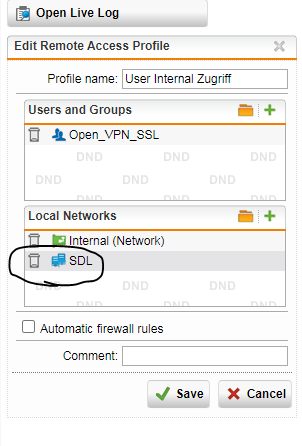
Right now, I have a remote connection to the internal network (A) let’s say 192.168.23.0/24. This is accessible via the Sophos VPN Client and I can connect to the terminal server.
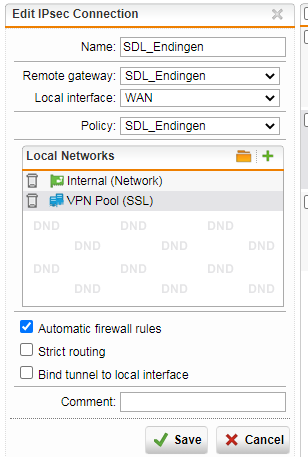
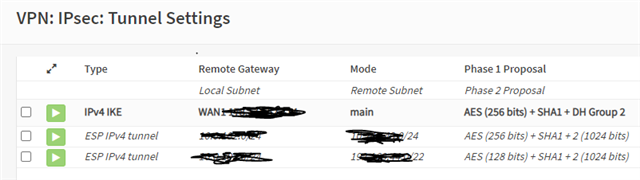
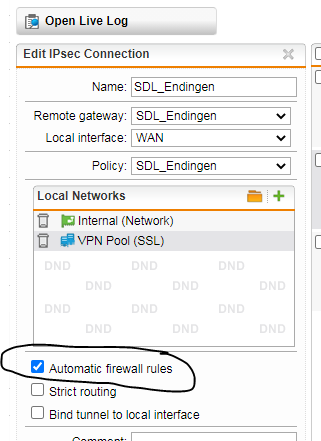
I also have a IPSEC connection to an external network (B) let’s say 10.10.100.0/24. The PC’s and Servers in B are member of the domain network of A and I can ping and RDP them from A.
My goal is to be able to have a remote connection to B as well and can RDP to a server in A and in B.
Sorry German speaker
Can somebody help?
This thread was automatically locked due to age.