Hi,
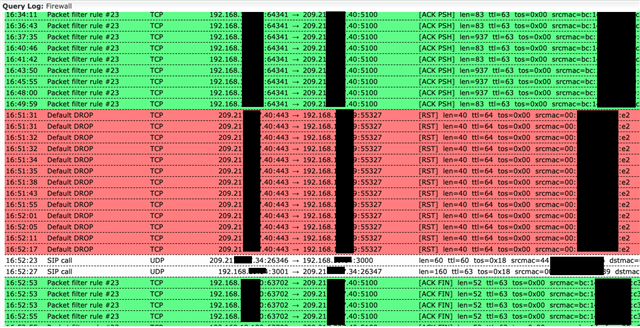
Our new voip desktop phone app (MaX UC / Mitel) has a chat feature that should include the ability to send over sms. It looks like it's getting blocked as below:


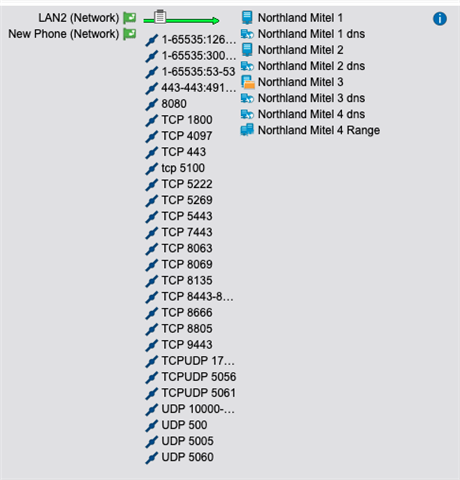
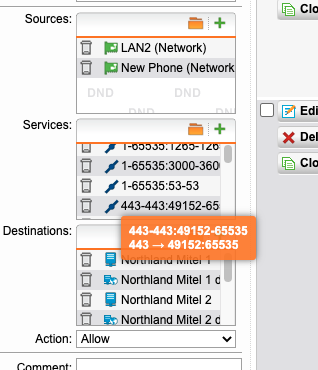
I have these (among others) allowed between my LAN and my provider's server (the address getting blocked above)
443-443:49152-65535
TCP 443
Separate rules, one allowing the from provider to my lan, the other from lan to provider.
I read the section in "rulz" and still can't pin down what could be blocking this. Rule #2 lists the order in which the packet is handled, but..
- the connection tracker (conntrack) first - WHAT IS "CONNECTION TRACKER?"
- then Country Blocking - COUNTRY BLOCKING OFF AT MOMENT
- then the 'ICMP' tab in 'Firewall': Traceroute and Ping are regulated on the 'ICMP' tab. The "All" service only includes TCP and UDP - none of the other IP protocols are included. THIS WOULDN'T AFFECT THIS I DON'T THINK.
- then Intrusion Prevention (see the images below to see that IPS actually can happen in several places but happens only once!) - I VERIFIED THE ADDRESS IS LISTED IN EXCEPTIONS FOR BOTH IN AND OUTBOUND
- then DNATs* - NOT RELEVENT I DON'T THINK.
- then VPNs - SAME. EXCEPT I DID TURN OFF SSL VPN SINCE IT'S USING 443
- then Proxies (except the SMTP Proxy in Transparent mode which captures traffic after it has been forwarded by a DNAT) - NOT SURE ABOUT THIS, EXCEPT WE DO HOST OUR OWN WEBSITE BUT IT ONLY FORWARDS SPECIFIC REQUESTS GOING TO OUR "WEB ADDRESS" ADDITIONAL IP address ON OUR WAN INTERFACE
- then manual Routes and manual Firewall rules, which are considered only if the automatic Routes and rules coming before hadn't already handled the traffic - THIS IS WHAT I HAVE THE RULE LISTED IN, iSN'T IT?
- and, finally, Application Control.
I'm stuck and lost.
Thanks,
Jeff
This thread was automatically locked due to age.