Hi all,
as i can't barely find any information on this:
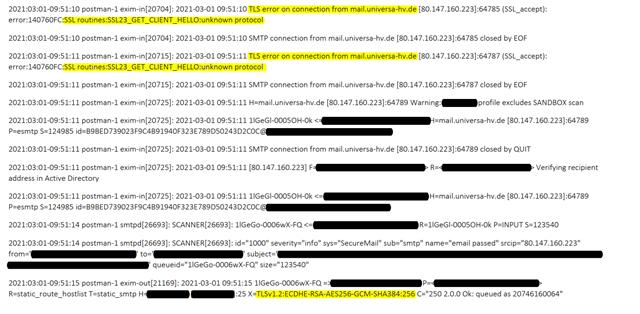
We have set TLS v1.2 as the minimum requirement for SMTP communications (Email Protection -> SMTP - Advanced - TLS Settings). After having a look at the logfiles, there are many connections that have been refused due to this setting (SSL routines:SSL23_GET_CLIENT_HELLO:unknown protocol), which is generally ok for security purposes. But there are also some client, that are obviously still using older protocols, so those Emails are also refused. We have assumed that anyone in this case would get an NDR but this does not seem to be the case (in our configuration?). We are aware that we can exclude those client domains but first of all you (and the client) have to know about it without digging in the logs. This is the case we have now: Client mail got lost without knowing about it on both sides.
So the question is: is this the standard behavior or is there a way to enforce NDR?
System: UTM 9.705-3 / Exchange 2019
Kind regards
Dennis
This thread was automatically locked due to age.