Hallo,
seit ich meine Vodafone Leitung auf 1GB Business mit fester IP umgestellt habe, klappt das nicht mehr. Ich war da nun schon Wochen bei, finde aber keine Lösung. Vielleicht kann jemand helfen:
1) Feste IP auf einem externen Interface
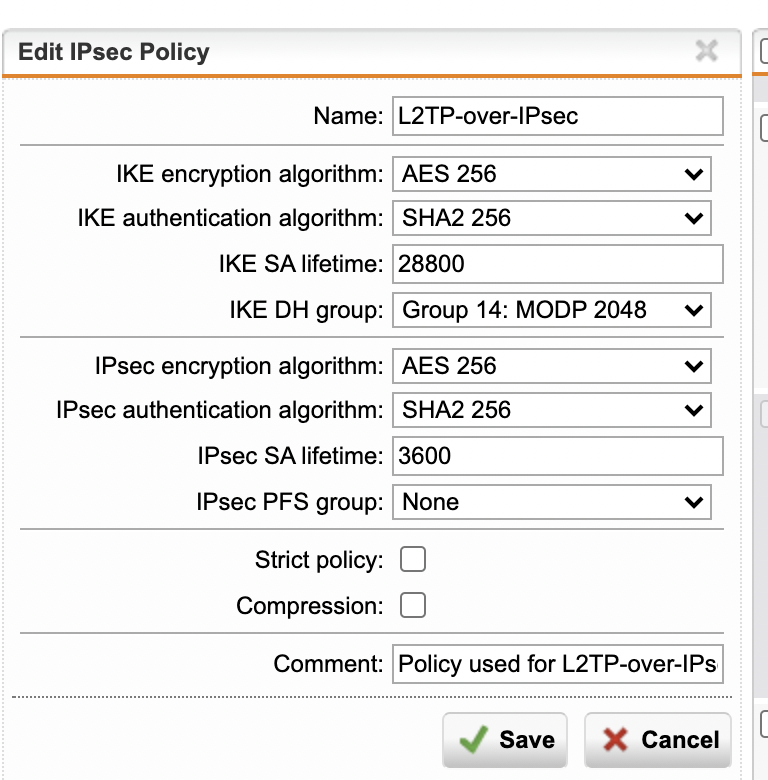
2) Policy für L2TP IPSEC angepasst
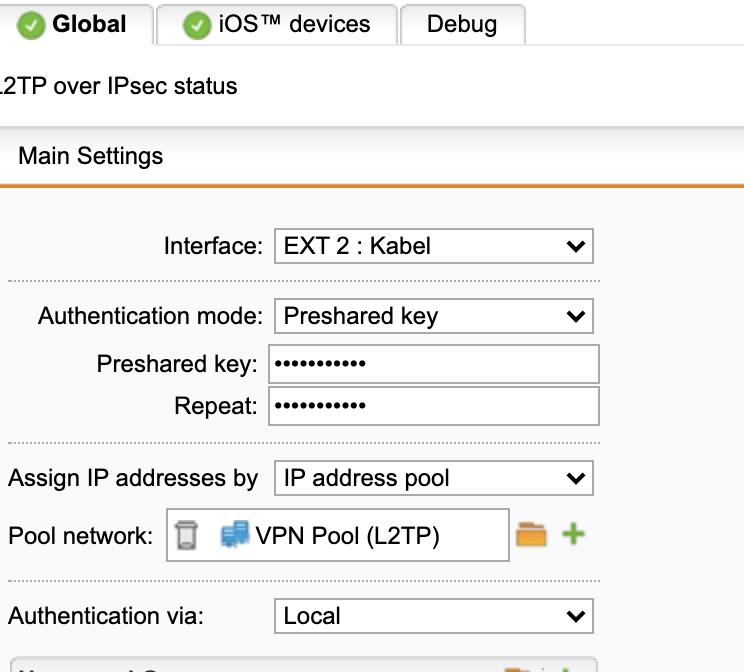
3) LT2p Settings auf der UTM sind ja eigentlich selbsterklärend.
4) Das Log sieht wie folgt aus:
Anmerkung:
NAT Traversal (NAT-T) isrt natürlich aktiv. Ich verseteh es nicht.
This thread was automatically locked due to age.

