Hi guys,
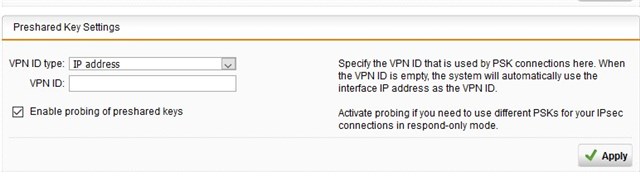
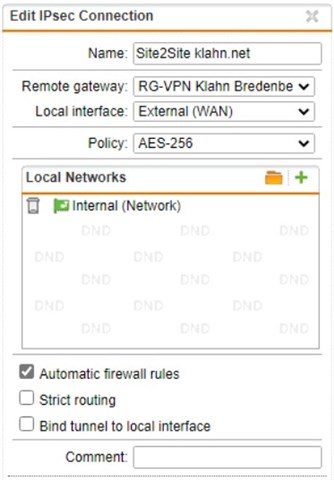
in our HQ there's a SG behind a FritzBox Router. In the FritzBox theres an Expose Host configured. At customer Site there's an SG behind a FritzBox. There's also an Expose Host configured.
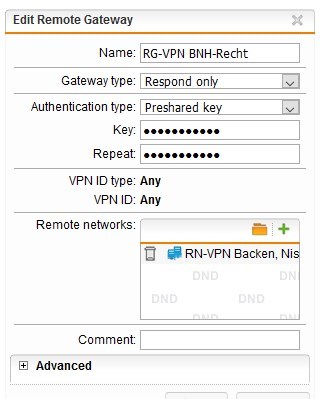
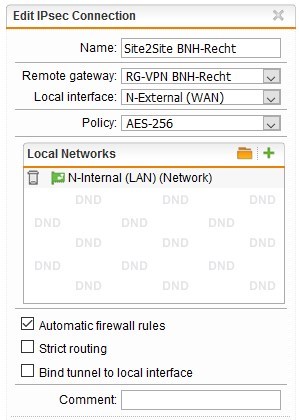
HQ SG (Respond only):
LAN: 172.17.10.0
WAN: 10.10.0.2
HQ FritzBox:
LAN: 10.10.0.1
WAN: 217.70.195.127
INTERNET
Customer FritzBox:
LAN: 192.168.2.1
WAN: 87.140.61.79
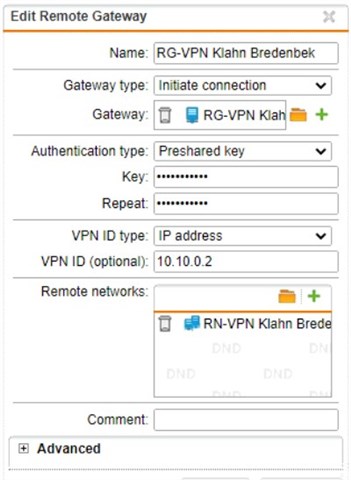
Customer SG (Initiate):
LAN: 192.168.10.0
WAN: 192.168.2.2
At another customer without FritzBox it's possible to get a tunnel. But with two FritzBoxes it won't work.
Do you have any ideas, how I will get this work?
Greets
Christoph
This thread was automatically locked due to age.