*Synchronized Security in SFOS 17.5*
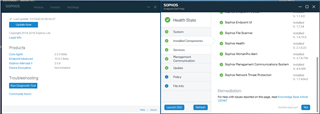
SFOS 17.5 adds two additional new Synchronized Security features to the release, Lateral Movement Prevention and Synchronized UserID, in order to make use of these new Synchronized Security features you will need to have the latest EAP release of Sophos Endpoint Protection (to be released November 12th), you can check the version based on the screenshots below, specifically Sophos Network Threat Protection has to be >v1.7. The Sophos Network Threat Protection version can be checked by clicking the ‘Run Diagnostic Tool’ button on the about screen.
For more information on joining the EAP Program for Endpoint Protection please visit https://community.sophos.com/products/intercept/early-access-preview/
Besides these two new features in Synchronized Security there are also enhancements to Synchronized Application Control that makes handling of discovered applications easier.
*Lateral Movement Prevention*
Lateral Movement Prevention allows an endpoint to be isolated on the same broadcast domain and hence prevent infections to spread laterally over the network between endpoints. XG Firewall is used as the distribution hub for all information necessary for the endpoint to perform this isolation from other infected endpoints. Configuration for this feature is available within Sophos Central.
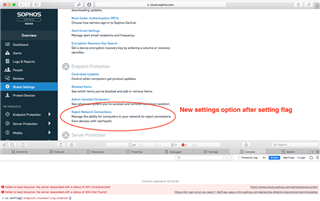
You will need to open the developer console in your browser after logging in to Sophos Central and enter the following command: sc.setFlag('endpoint.stonewalling.enabled')
After entering this command you should be able to see a new entry similar to the screenshot below, this will take you to the configuration for excluding specific endpoints from the stonewalling feature so that they are not being isolated.
*Synchronized UserID*
The new Synchronized UserID feature is an additional authentication method for users on XG Firewall. Synchronized UserID requires a configured ActiveDirectory Server for authentication (details can be found in the OnlineHelp) and the endpoint has to be part of this ActiveDirectory Domain as well as the user. Ones the user on the endpoint is authenticated to the ActiveDirectory, the endpoint will send the login information to XG Firewall that will also authenticate the user to the ActiveDirectory. The Synchronized UserID feature is only available for Windows endpoints and only in combination with ActiveDirectory.
*Synchronized Application Control*
SFOS 17.5 also enhances Synchronized Application Control to better handle discovered applications. We have added a separate filter for System Applications, which can now been seen in the special filter “System Applications”, these includes applications like the Windows and MacOS services that are being discovered.
Another added option to manage discovered applications is the additional ‘hide’ option that moves an application to the filter ‘Hidden Applications’. Hidden applications will no longer be displayed in the discovered applications list, but opposed to ‘delete’ these applications will not be added again after they are discovered again but will remain on the ‘Hidden Applications’ filter. This feature is intended for applications that the admin does not want to have displayed continuously on the application list, but are still present in the environment.
These additional features should make the handling of larger amounts of discovered applications easier.