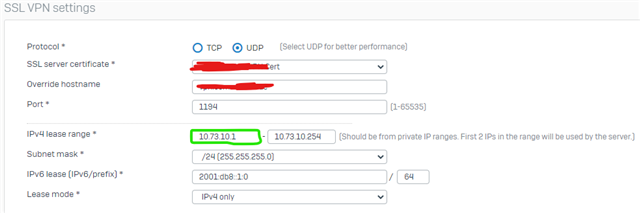
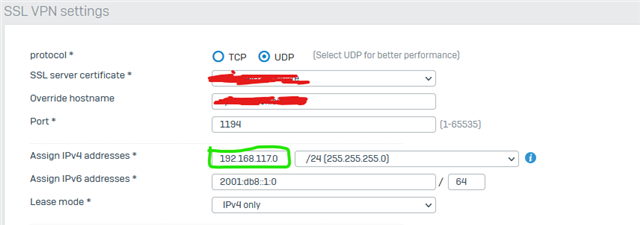
I updated via export/import all settings and now i saw, that the "Assign IPv4 addresses" is the value of "IPv4 lease range" start IP. So now i had 192.168.111.10/24 as network, what is wrong and hard to find, because configuration was running before ;-)
I dont know if it is relevant in an upgrade path other than export/import complete configuration.
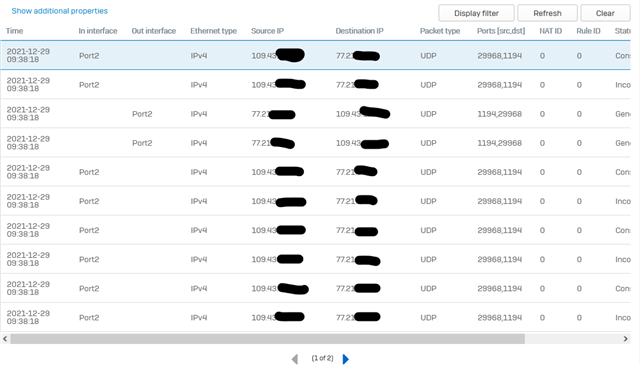
Despite that I found the error, I can no longer connect to the Sophos from the iphone with openVPN and the GUI logfiles show nothing.