Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
______________________________________________________________________________________________________________________________________
Table of Contents
Overview:
This Recommended Read shares XML import file to import increasing Zoom Networks into Sophos Firewall
Zoom Network XML File
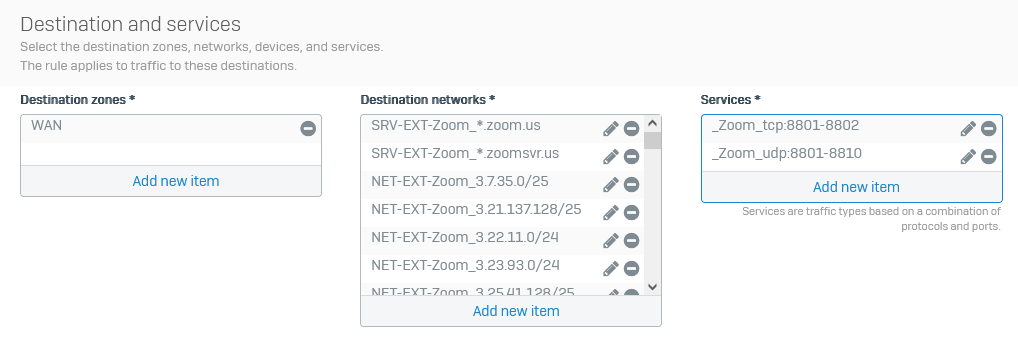
The zoom network list has increased to over 300 networks.
Attached is the XML file containing all the networks listed on the Zoom site as of 2023 Jan 23. Created as described here. Still a lot of work, though.
You can remove the .zip extension and import it into XG as Entities.tar.
/cfs-file/__key/communityserver-discussions-components-files/258/Zoom_5F00_20230123.tar.zip
______________________________________________________________________________________________________________________________________
Added horizontal lines, edit format, and minor changes on grammar. added table of contents and overview
[edited by: Raphael Alganes at 1:24 PM (GMT -8) on 4 Dec 2023]