Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
Hi all,
As there are some posts/questions/queries about this topic, I want to spend some time explaining the inner working of the Sophos Firewall.
AD Users creation process:
The first step to integrating a Microsoft AD is to add an AD server to Sophos Firewall. In this process, you’ll add all the needed information for Sophos Firewall to query your own AD.
It will also add the option to import an AD group and/or an AD organization unit (OU).
The Firewall cannot fetch/import users from the AD.
Instead, Sophos Firewall creates the User by a successful authentication method. For example, You integrate an AD server, import your groups, and see no user in Sophos Firewall Webadmin - Authentication - Users. If you authenticate a user via any facility (For example User Portal), it’ll create the user automatically. The user will be added to the Sophos Firewall.
The primary group:
The Sophos Firewall uses a "primary group" to attach a user to a group. See: https://docs.sophos.com/nsg/sophos-firewall/19.5/Help/en-us/webhelp/onlinehelp/index.html?contextId=authentication-AD-users-groups
By the time of any authentication, Sophos Firewall will look up all groups, attached to the user and match them against all imported groups. The first match will be used to attach the user to this specific group.
This group will be shown in the Webadmin - Authentication - Users.
Every user has to be in a group. If none of the imported group's matches, the selected "default group" will be used. See Webadmin - Authentication - Groups.
Backend group membership: (Change in recent Firmware, see below)
Talking about the previous parts, there’s plenty of question about: Does Sophos Firewall only support one group? The answer is "No, but it depends".
Sophos Firewall will see and attach a user to all imported groups. But it will not be able to show the administrator the relationship. The groups are shown "empty" on the web admin. But what happens in the background, the attachment will be listed in the database.
There are modules, which can only work with the primary group. There are modules, which can work with all backend groups.
Supports all Backend groups: Firewall policies, TLS Policies, Web Filter policies, SSL Remote access VPN.
Supports only the primary group: Hotspot, WAF, IPsec Remote access
There are more modules, but those are the most frequently asked.
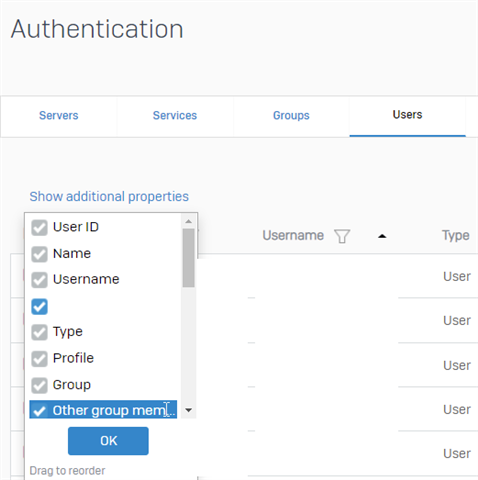
In V18.5 MR2+ and V19.0 EAP1+ the administrator can see all the backend membership groups.
Under Authentication - User - Add the additional properties:
Common setups:
Most administrators only need a backend membership of multiple groups for firewall and web filtering. Just a frequently build setup: All users are in the "AD domain user" group on the Sophos firewall - You import a group called "Domain Admin" and want to give those admins extra privileges (Can use SSH, can access all websites). That is possible to build with an Sophos Firewall. Simply place those (empty) groups in firewall policies on top and allow SSH.
Policy Tester:
The Sophos Firewall Policy Tester supports the backend membership relationships. So if you have an admin user and test them against this previously explained scenario, it’ll show your Firewall rule and web filter policy, only the admin is a member of.
Related Information:
Added horizontal line below Disclaimer, end of RR and Edited XG -> SF, Edited Table of Contents
[edited by: Raphael Alganes at 11:48 AM (GMT -8) on 24 Nov 2023]
