Moin,
Ich will zwei Standorte verbinden. Auf der einen Seite ist ein Subnetz die sich über eine PFSense auf die andere Seite über eine Sophos XG mit zwei Subnetzen verbinden soll. Phase 1 ist kein Problem, aber es wird nur ein Subnetz verbunden.
Wenn ich auf der Sophos anstatt der beiden IP Host Objekte "ANY" eintrage, funktioniert es. Aber das kann nicht das ergebnis sein.
Wer kann mir helfen?
VG
Karsten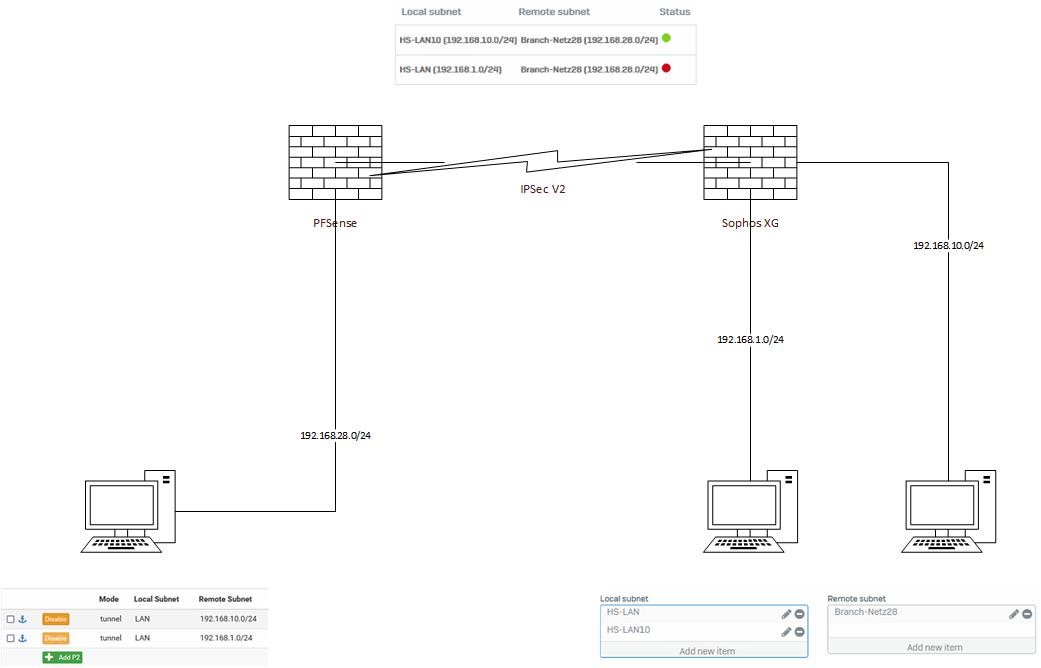
Added TAGs
[edited by: Erick Jan at 1:34 PM (GMT -7) on 24 Sep 2024]


