Hey guys, reaching out for some much-needed help. Have read similar posts but nothing makes sense to me in them.
I have purchased a certificate as well as created a local active directory certificate server. (All Witchcraft to me)
Have installed them on the sophos XG firewall under Certificates. All working well it appears.
I go to:
Configure -> Authentication -> Servers and set up my SSL/TLS connection to active directory.
Select Test Connection and all is good.
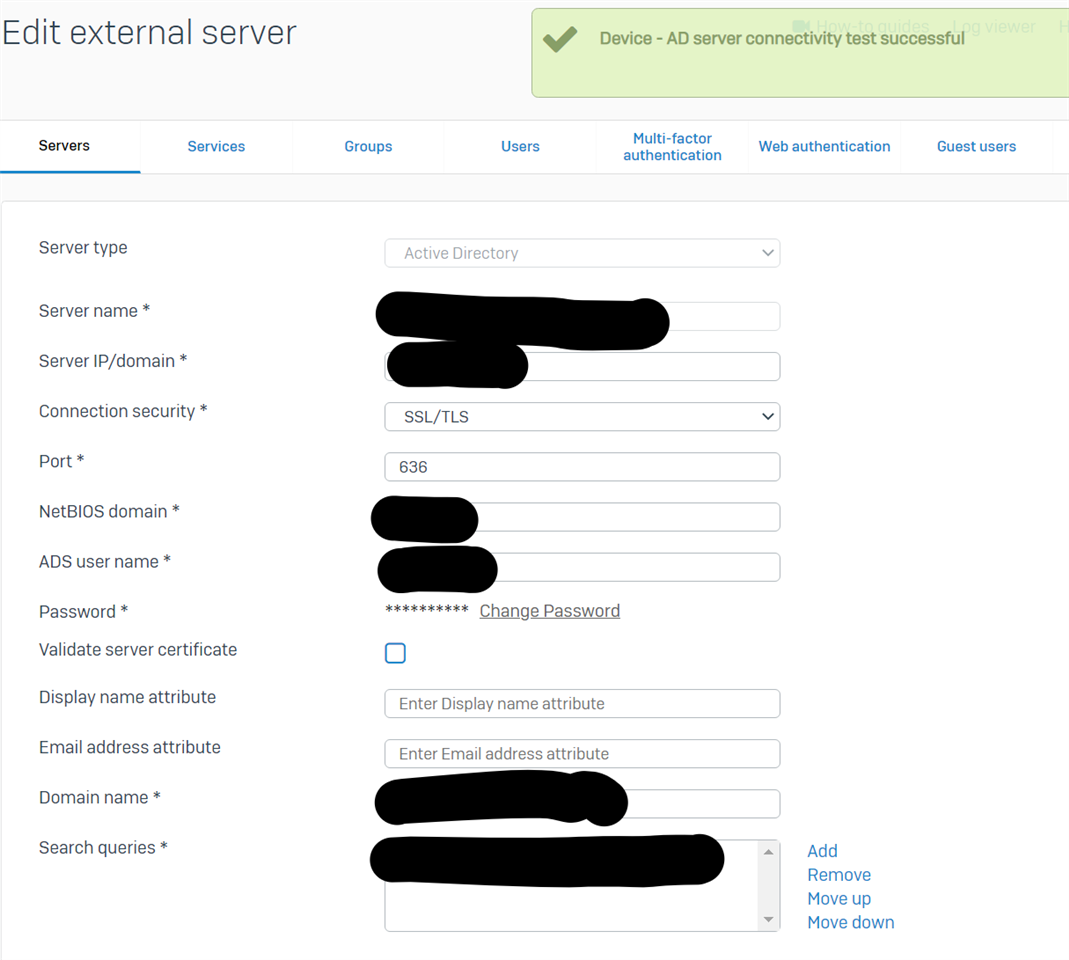
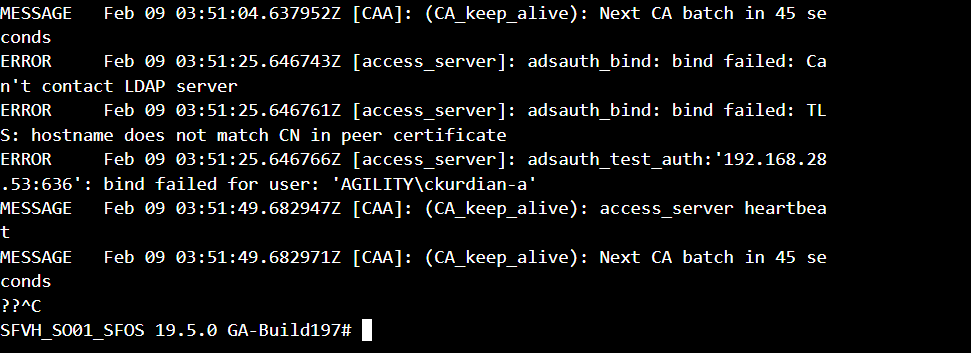
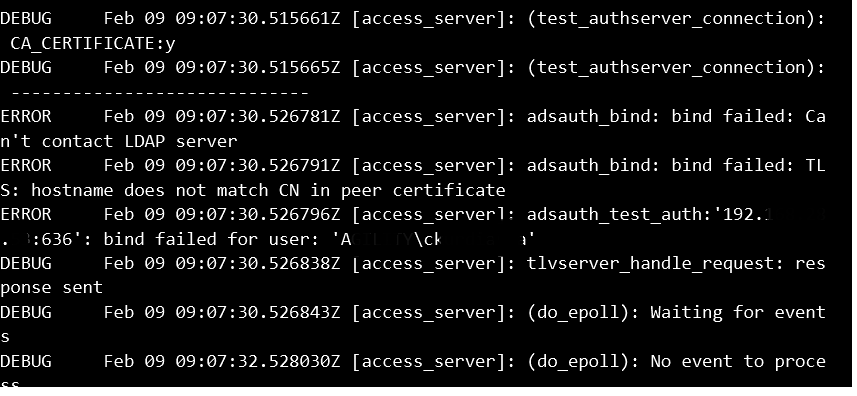
However, when I select Validate server Certificate I get:
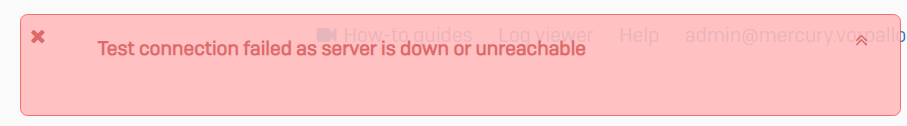
What is the firewall doing here, which server is down or unreachable? Is it my Root CA server that is in active directory? Or is it the domain controller? (CA is install on a Domain Member, not on the domain controller)
Note: Firewalls are not active on the Windows Domain Controller and Domain Members.
All active directory servers and workstation are on the local network. I don't think I am restricting anything on the local network. Or is there a predefined rule that does?
What am I missing here? Any advice would be greatly appreciated.
Thankyou.
This thread was automatically locked due to age.