Hello there,
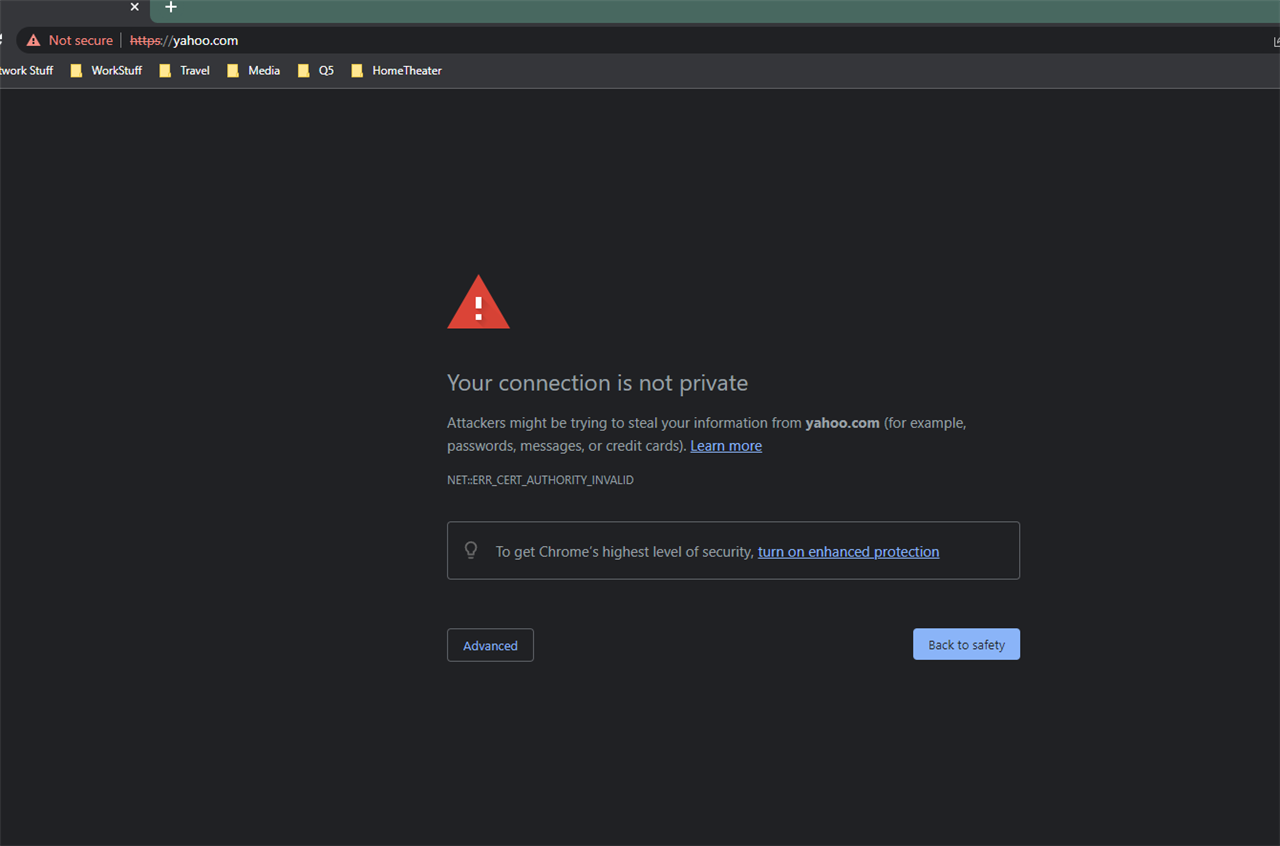
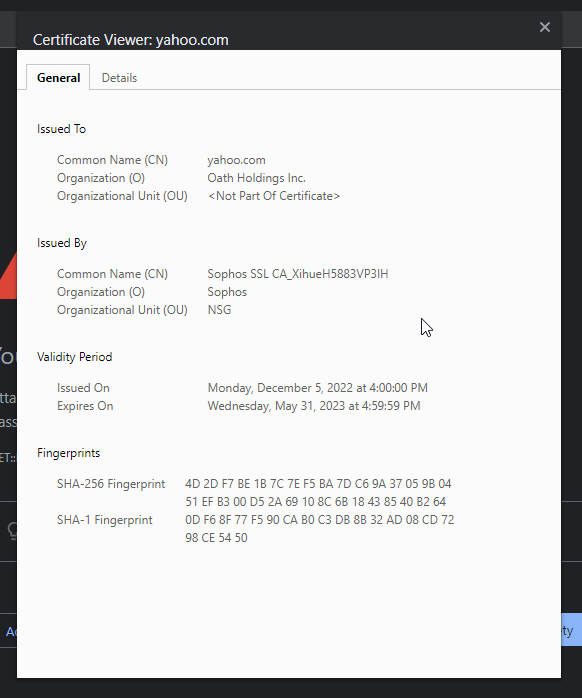
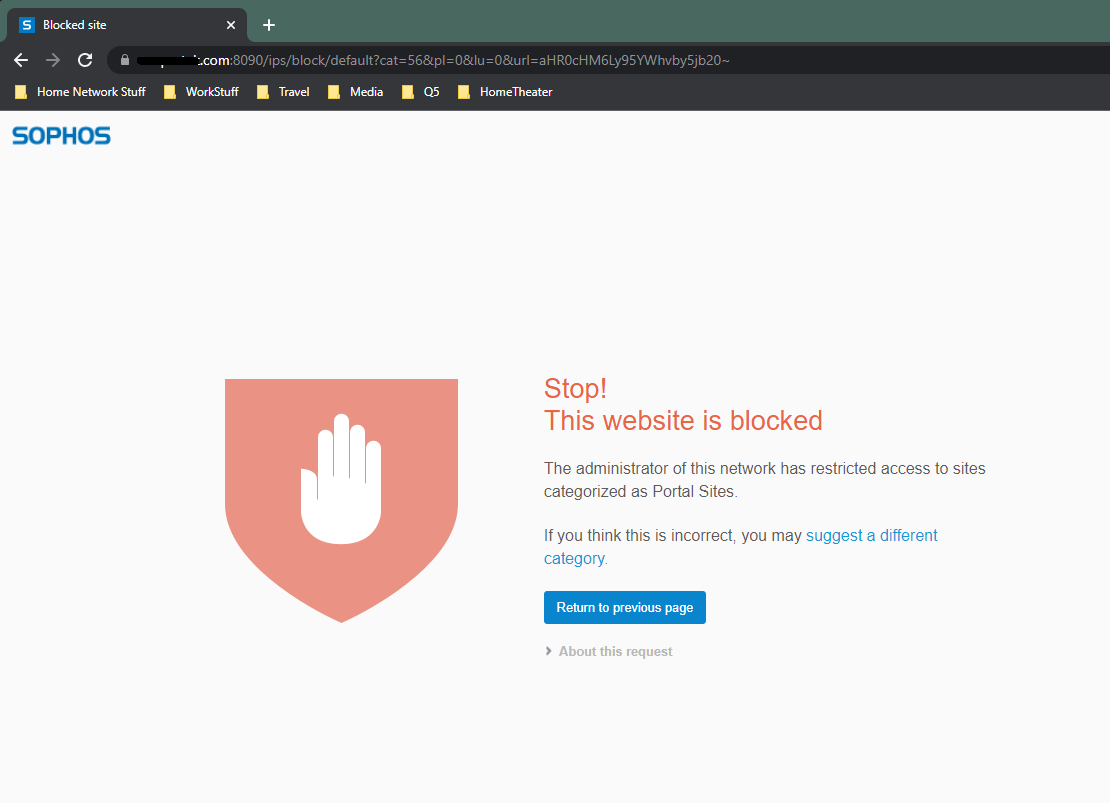
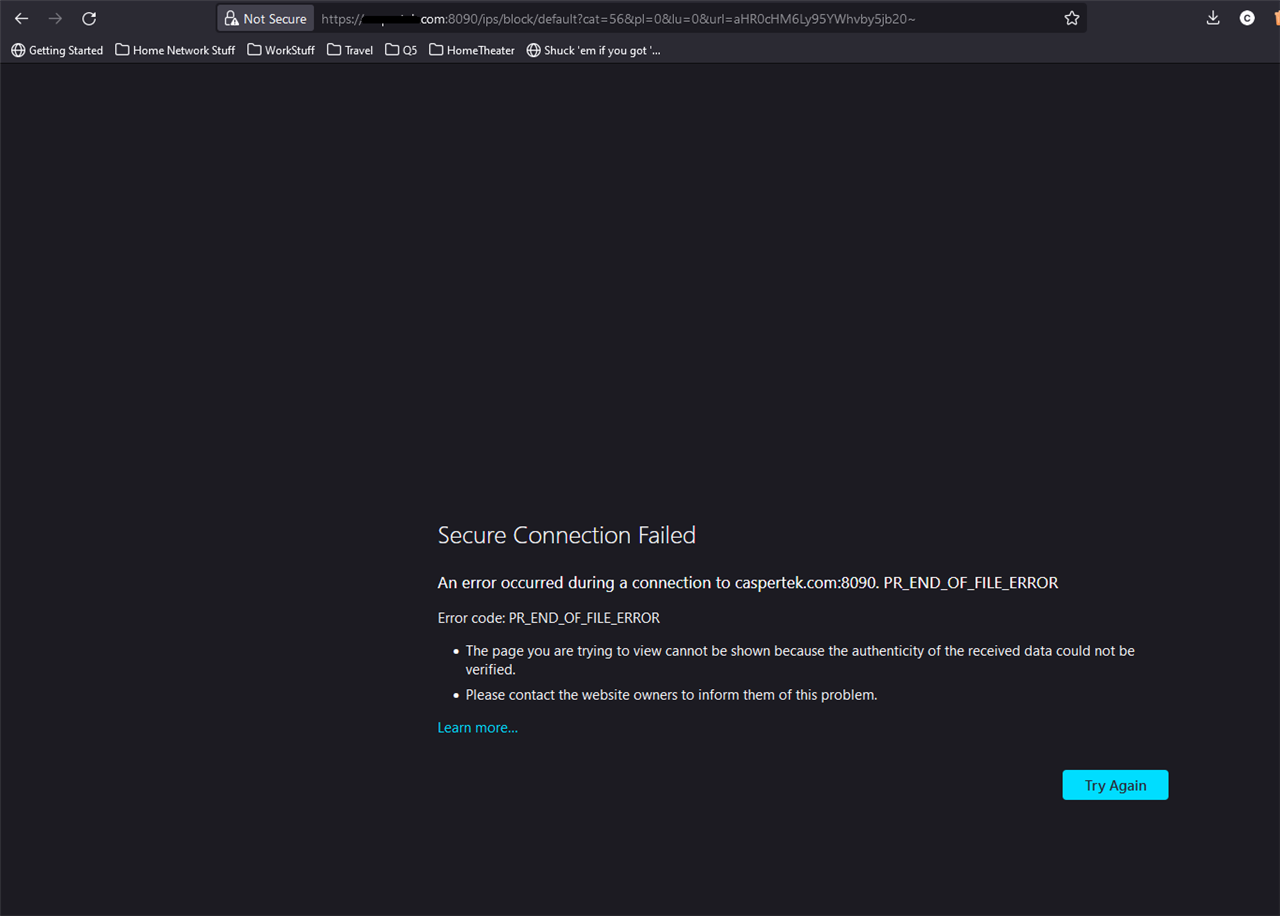
I just enabled a web filter policy to block various websites, but I'm having issues with the user notification options. I have installed a valid LetsEncrypt SSL certificate and it's working great for the user portal. However when a webpage is blocked, the page fails to load as the user is redirected to https://mydomain.com:8090 and the web browser just flops and loads nothing at all.
I can work around this by going to System > Administration > Admin and User Settings > Admin console and end-user interaction > Use the IP address of the first internal interface.
However then users get the typical browser certificate error because the blocked webpage notice is coming from an internal IP. How can I get internal users the ability to load https://mydomain.com:8090 and have it load properly in their web browser with a valid cert?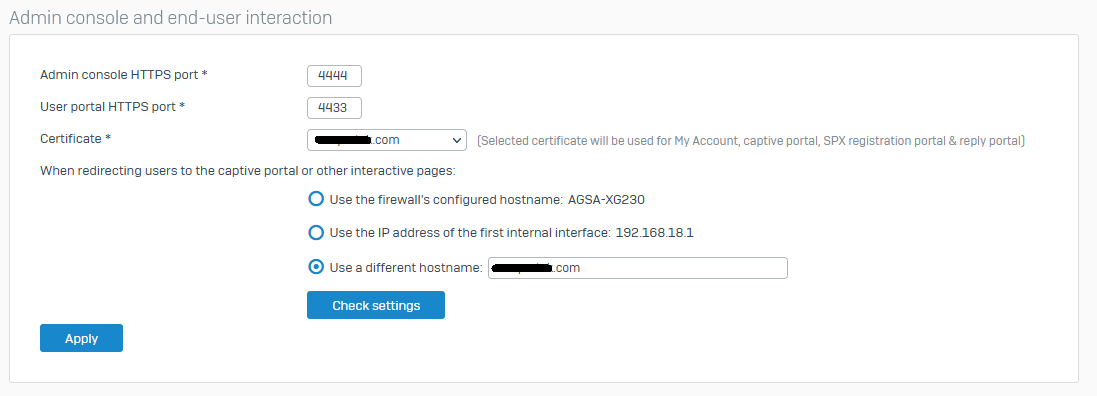
This thread was automatically locked due to age.