Hi everybody,
I have done an Update from SFOS 18 to SFOS 19 and since the Update I am not able to connecto to SSLVPN any more.
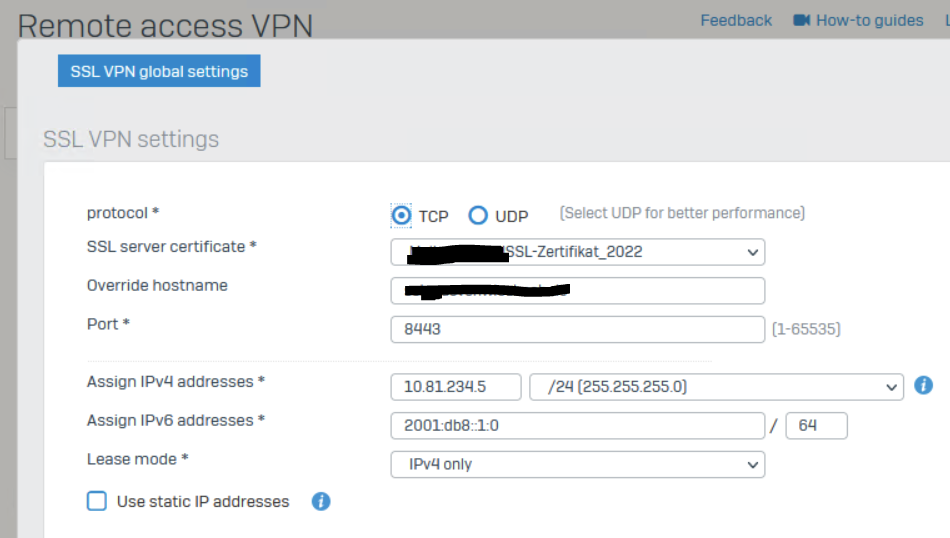
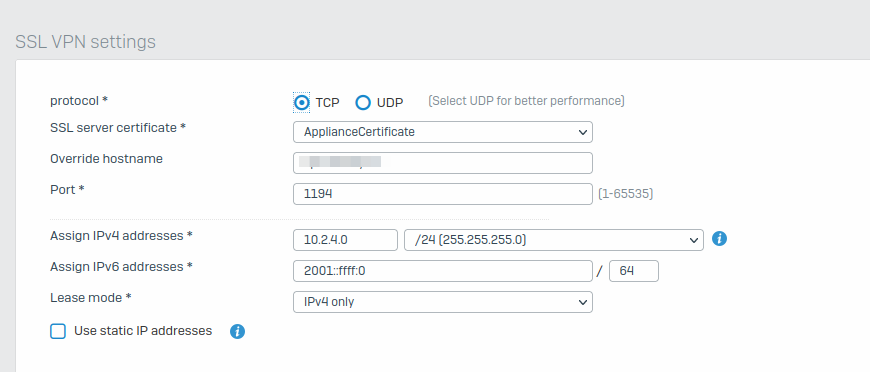
In CLI I can see that all incomming Packets are dropped for SSLVPN when running (drop-packet-capture "port 1194").
But I can access SSH and HTTPS Management from Internet.
So I guesss the Problem is somehow caused by having NAT-Rules on the same official IP (Mailserver Port 25 and HTTPS-Server Port 443) and therefore the Appliance does not accept running SSLVPN on Port 1194 or Port 8443.
I would appreciate if somebody has a Solution on that, as I only have one Official IP and SSLVPN is not working at all (neither Site2Site, nor Client-VPN)
In SFOS 18.5 exactly the same setup was working.
Thank you!
Markus
This thread was automatically locked due to age.