Hi,
I'm experiencing a strange issue with the SDWAN routing engine. I have 2 Sophos XG connected via route-based ipsec (xfrm interfaces) and using SDWAN rules for the routing decision.
The XG located at the branch office route traffic, using a SDWAN rule, from the subnet 192.168.112.0/24 to 192.168.111.0/24.
In the SDWAN rule I'm using the "Route only through specified gateways" options.
As you can see the traffic incoming is routed via xfrm6 interface.
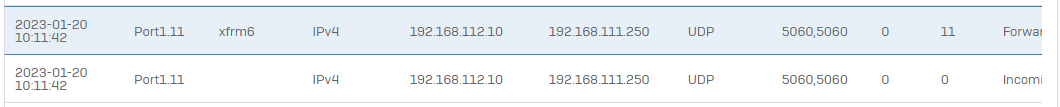
But sometimes the packets are not routed correctly. Instead of going out through the xfrm tunnel they are routed to the PPPoE interface.
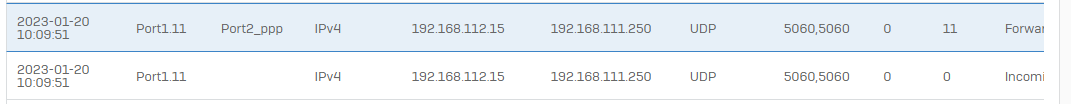
Disable, and re-enable, the SDWAN rule fix the issue, at least temporarily.
I'm not able to determine the root cause of the issue. Any ideas?
Thanks
This thread was automatically locked due to age.


