Hello,
in our company we got about 60-80 users. Each department got his own vlan running over one port.
XGS2100 (SFOS 19.0.1 MR-1-Build365)
Over the year i was setting up the sopho xg and adding all Firewall rules, like all department are in one zone and got a any rule to our servers with the specific ports needed. (Each server his own rule) . I think i am about 80-85 rules now for evrything. (Yes i am using zones to group the departments atleast.)
Now most of them got ips and the other stuff activated (AV/WEB/APP/IPS/LOG) but even after using the predefined ips rule (LAN TO WAN and LAN to DMZ) in hope to reduce some stress, the cpu usage is still high.
I readed some does not use all this to lan to dmz? is that good? My thinking is, if user gets infected like over mail, and using thang a exchange vulnerability, i got atleast my sophos with ips and zero day, right?
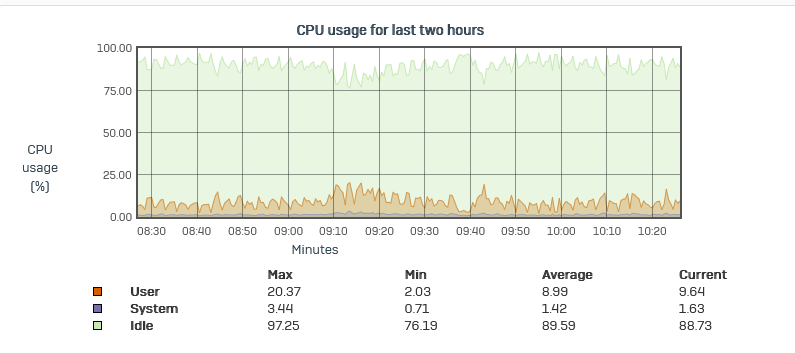
Usally at in break times, but sometimes also between them. You can always see in the Dignostic Graph a high cpu usage. The whole network get than sloppy and sometimes disconects applications, thats hell for running teams meeting and remote sessions.
Under the command "top" i can see multiple process with snort, which has 99 cpu usage, and i see all cpu most of time at 100.
All pattern should be up to date (intervall set to high). Ips Settings max packages 8 is still there.
Now my questions:
Is our sophos to small? Frankly speaking this got worse some months ago maybe at start of september, but maybe when we got the upgrade from version 18.xx to 19.xx.
Can i optimize the ips profiles?
My problem no matter where i look i cant find a good documentation what all categories means (like misc, scan) sure i can click os-windows, or server and client.
Are "clients" only win 10 ? Or does that mean which direction the attack is happening?
If i look at the lan to wan ips template,firstly you see many entrys like OS-windows, then browser, then windows clients and then all clients?? What does that mean all clients? Why are there entries before for windows/linux if i got entry for all clients? Is there difference or is it for the purpose i use it as template and delete what i dont need?
My biggest problem right now is, that i am missing the tools to investigate further, the reporting would be usefull if you could specifc a time, but no you can always do only days.
This thread was automatically locked due to age.