Hello,
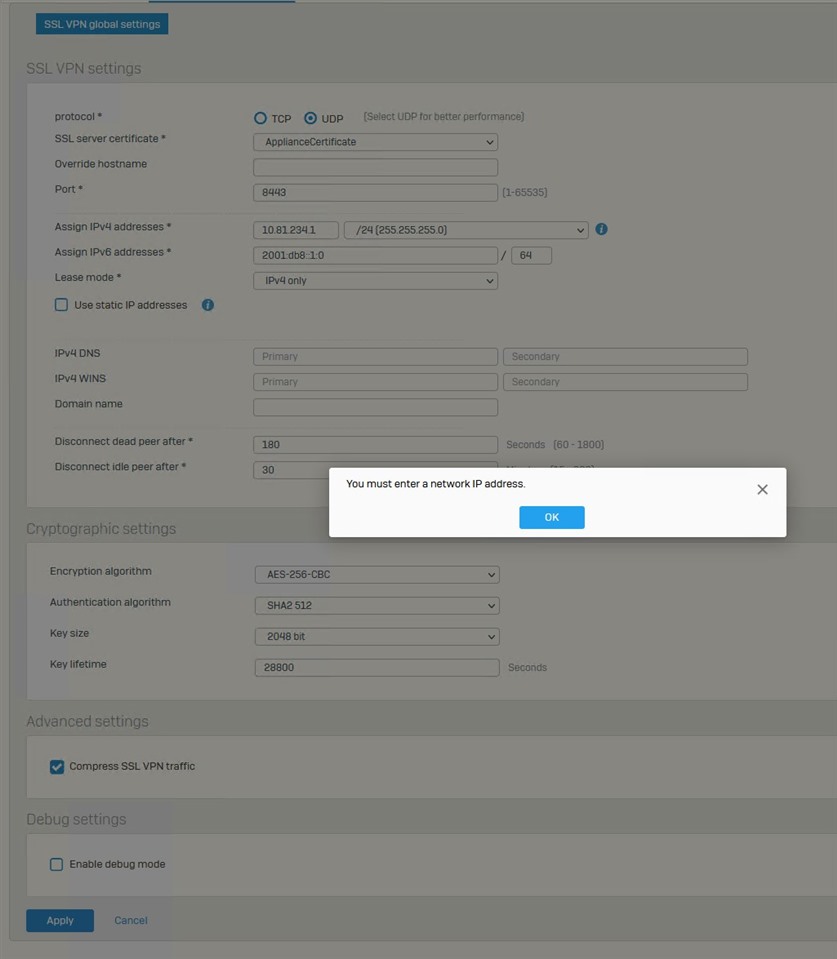
from one day to another I cant connect to XQ (latest Firmware). Opebn VPN sayes (I wil post only RED sections here):
Fri Sep 2 15:43:48 2022 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless "allow-compression yes" is also set.
Fri Sep 2 15:43:48 2022 DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES-256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to silence this warning.
And later:
Fri Sep 2 15:44:00 2022 ROUTE: route addition failed using service: Das Objekt ist bereits vorhanden. [status=5010 if_index=6]
Fri Sep 2 15:44:00 2022 Route addition via service failed.
Its green tough but I cant connect with RDP.
This thread was automatically locked due to age.