We're having the situation that we cannot allow SSL VPN Device Access to a central XG Firewall from locations connected by Site-2-Site IPSec tunnels.
That's because the remote locations are automatically assigned to VPN zone in XG.
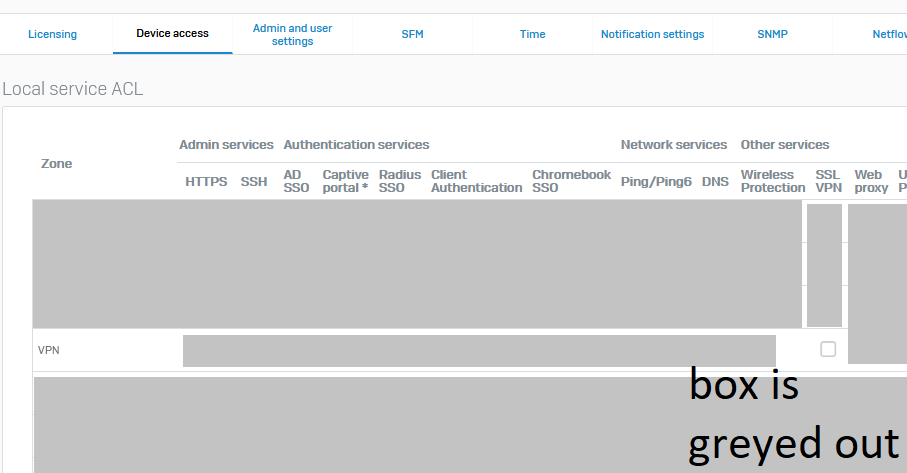
And SFOS does not allow to enable SSL VPN for the VPN zone - it's disabled. I wonder why there is this limitation? What's the reason that there is the need to deny this?
The only way to enable this is by ACL Exceptions from "Any Zone" and I hate that.
Isn't there a better way to do that? Transparent and easy to manage?
You may ask why we're doing such things: that is because we're requesting users to connect once to SSL VPN from their office after they received a new computer or a new Sophos Connect Client installation with .pro file. So they can be sure, they have the configuration loaded in their SSL VPN client and that it's working.
SFOS 18.5. MR3
This thread was automatically locked due to age.

