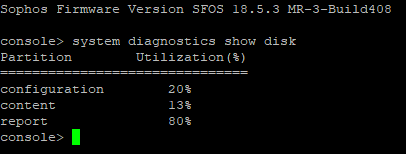
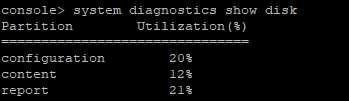
Hello team,
I have configured SSL VPN for my organization. But it will show below error during connect SSL VPN. And SSL VPN Not connected. Please refer below error logs.
Sat Jun 18 17:24:44 2022 TCP connection established with [AF_INET]xxx.xxx.xxx.xxx:8443
Sat Jun 18 17:24:44 2022 TCPv4_CLIENT link local: [undef]
Sat Jun 18 17:24:44 2022 TCPv4_CLIENT link remote: [AF_INET]xxx.xxx.xxx.xxx:8443
Sat Jun 18 17:24:44 2022 MANAGEMENT: >STATE:1655553284,WAIT,,,,,,
Sat Jun 18 17:24:44 2022 MANAGEMENT: >STATE:1655553284,AUTH,,,,,,
Sat Jun 18 17:24:44 2022 TLS: Initial packet from [AF_INET]xxx.xxx.xxx.xxx:8443, sid=5cf0b8d2 5ad9b415
Sat Jun 18 17:24:44 2022 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Sat Jun 18 17:24:45 2022 VERIFY OK: depth=1, C=IN, ST=Gujarat, L=SURAT, O=ld, OU=1985, CN=XXXX, emailAddress=XX@xxxxxxxxxxxx.com
Sat Jun 18 17:24:45 2022 VERIFY X509NAME OK: C=NA, ST=NA, L=NA, O=NA, OU=NA, CN=Appliance_Certificate_VEVBvvJkVo44PSp, emailAddress=na@example.com
Sat Jun 18 17:24:45 2022 VERIFY OK: depth=0, C=NA, ST=NA, L=NA, O=NA, OU=NA, CN=Appliance_Certificate_VEVBvvJkVo44PSp, emailAddress=na@example.com
Sat Jun 18 17:24:48 2022 Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Sat Jun 18 17:24:48 2022 Data Channel Encrypt: Using 256 bit message hash 'SHA256' for HMAC authentication
Sat Jun 18 17:24:48 2022 Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Sat Jun 18 17:24:48 2022 Data Channel Decrypt: Using 256 bit message hash 'SHA256' for HMAC authentication
Sat Jun 18 17:24:48 2022 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Sat Jun 18 17:24:48 2022 [Appliance_Certificate_VEVBvvJkVo44PSp] Peer Connection Initiated with [AF_INET]xxx.xxx.xxx.xxx:8443
Sat Jun 18 17:24:50 2022 MANAGEMENT: >STATE:1655553290,GET_CONFIG,,,,,,
Sat Jun 18 17:24:51 2022 SENT CONTROL [Appliance_Certificate_VEVBvvJkVo44PSp]: 'PUSH_REQUEST' (status=1)
Sat Jun 18 17:24:51 2022 AUTH: Received control message: AUTH_FAILED
Sat Jun 18 17:24:51 2022 SIGUSR1[soft,auth-failure] received, process restarting
Sat Jun 18 17:24:51 2022 MANAGEMENT: >STATE:1655553291,RECONNECTING,auth-failure,,,,,
Sat Jun 18 17:24:51 2022 Restart pause, 5 second(s)
Can you pls help on this error.
This thread was automatically locked due to age.