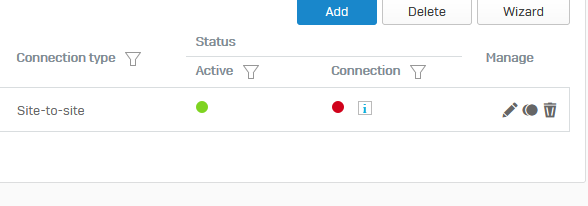
We have a Site-2-Site from XGS 136 with SFOS 18.5 RM3 to SG Firewall 9.711-5. Connection works and we have also other XGS's connecting to that SG also without problems.
The SG is the receiving side while the XGS's are the IPSec initiator.
Quite basic stuff though.
But at this particular site we noticed an issue after the tunnel disconnected for the first time after a problem with the WAN line. The XGS machine did not re-initiate the connection after the first failure even if configured to do so.
The events in chronological order:
03.06.2022 10:18 IPSec Failed IKE message retransmission timed out
03.06.2022 10:27 IPSec Terminated
03.06.2022 10:28 IPSec Deny received IKE message with invalid SPI
07.06.2022 16:58 IPSec Established (my manual connect)
So the tunnel was down for 4 days until manual reconnect.
After login at the XGS machine the VPN status was shown on the XGS as this:
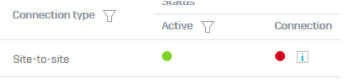
I clicked on the red dot to reconnect
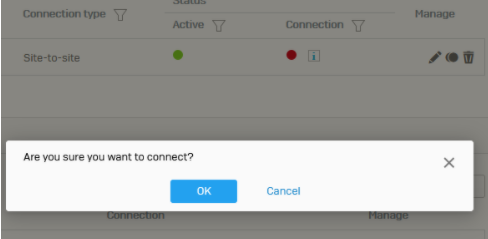
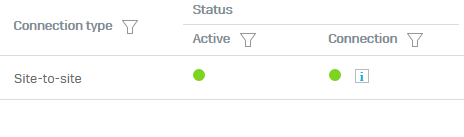
The connection has been established by the manual connect without problems.
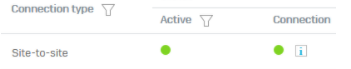
Nothing on that VPN has been changed, enabled, or disabled on the SG firewall.
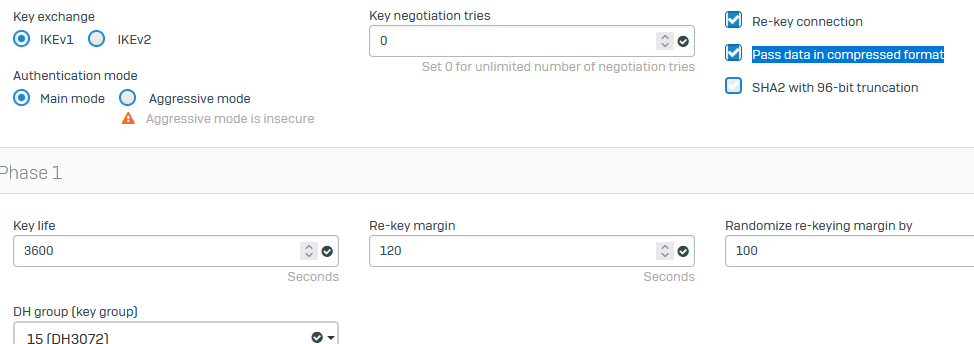
VPN Settings on XGS:
Dead Peer Detection is set to Re-initiate
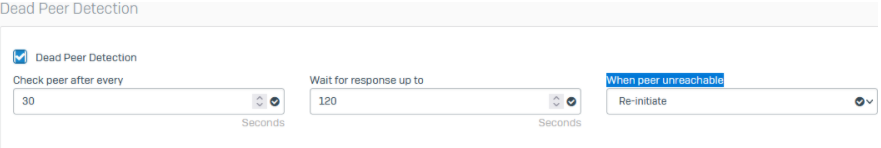
Something wrong? Why did it not reconnect?
This thread was automatically locked due to age.