Hi.
I am looking for some advise around the best practise for Web Filtering for a BYOD network.
We have a seperate network setup on our XG for residents who connect their own devices which are mainly mobile devices. We have a firewall rule crated to allow this dedicated zone out on the internet and in this rule I want to setup Web Filtering. I have created a Web Policy which includes a large amount of categories to block but I am unsure which of the other settings under this feature to enable or disable. These settings are shown as:
Web Policy:
Apply web category-based traffic shaping (currently disabled)
Block QUC propocol (currently enalbed)
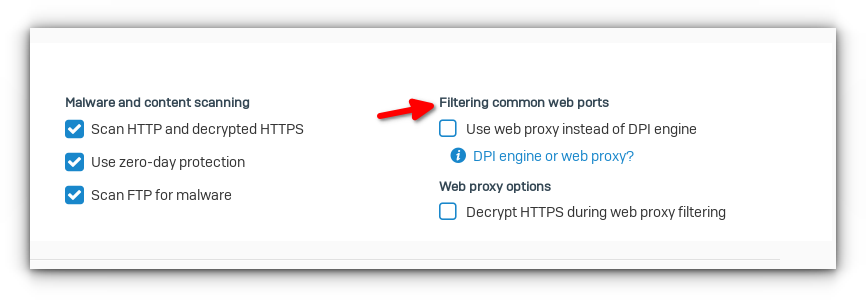
Malware and contect scanning
Scan HTTP and decrypt HTTPS (currently disabled)
Use zero-day protection (currently disabled)
Scan FTP for malware (currently enabled)
Filtering common web ports
Use web proxy instead of DPI engine (currently enabled)
Web Proxy Options
Decrypt HTTPS during web proxy filtering (currently disabled)
I have SSL / TLS Inspection enabled but I read somewhere about a certificate being needed to allow this to work correctly.
On the same XG we do have a corporate network which is setup against a different firewall rule and I plan to setup SSL and TLS inpection against this.
With the testing I have done on the residents network I have found internet browsing to be slow which may be down to the amount of categories I have selected. As this is a residents network I need to make sure a solid level of proteciton is in place and I would like secure sites to be scanned as most sites have a certificate in place.
Any guidance would be greatly apprecaited.
Many thanks, Dan
corrected the spell
[edited by: Vivek Jagad at 9:11 AM (GMT -7) on 20 Jun 2023]