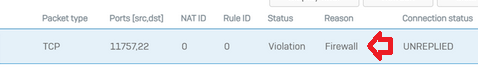
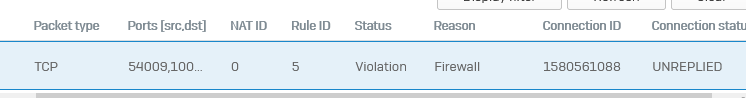
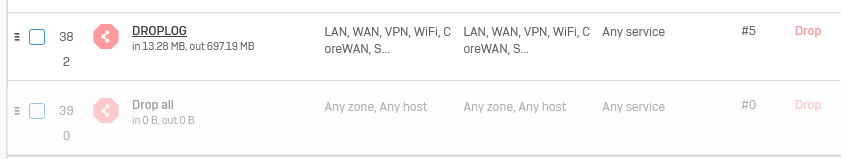
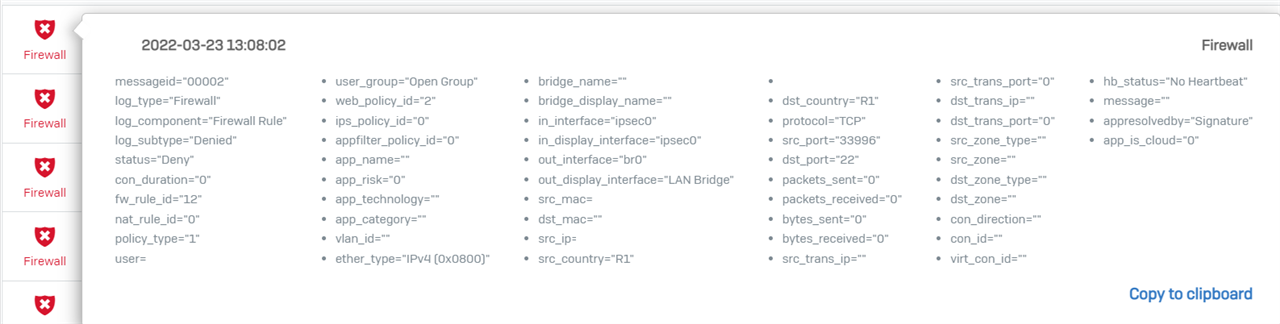
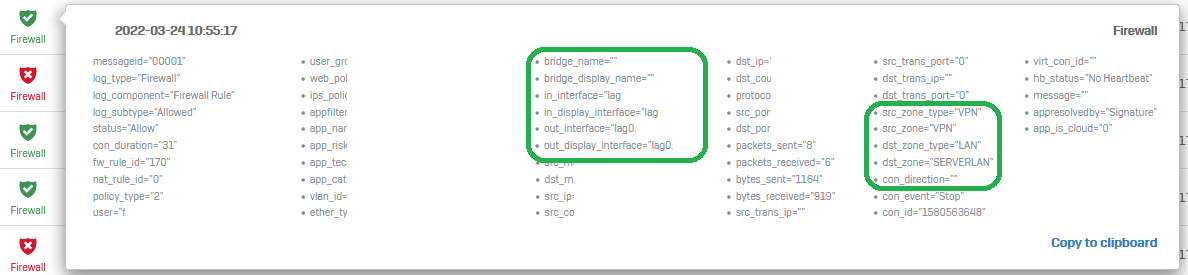
We have had reports of a certain IP address being available most of the time but occasionally it will become unavailable and the user is unable to ping it at this time. We have an XG 135 running SFOS 18.5.1 MR-1-Build326.
I don't see any blockages in the firewall logs for the timeframe in which the problem last happened. I would like to try and rule out the XG 135 and would appreciate any suggestions for debugging. It is difficult as it is intermittent.
This thread was automatically locked due to age.