Too many cooks and something has become messy with certificates on our XG and I need some help to get this sorted.
(SFOS 18.0.5 MR-5-Build586) virtual
Trying to upload a pfx-certificate generated by our certbot gives the dreaded red X. Mousing over the red X it says:
Certificate authority: Invalid or not installed
Issuer /C=US/O=Let's Encrypt/CN=R3
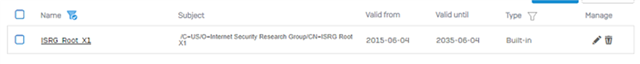
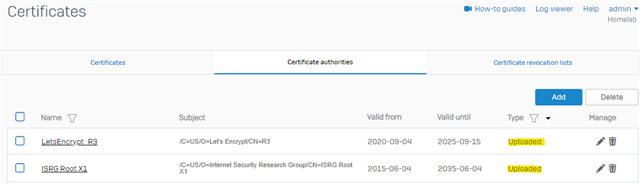
When I sort "Certificate Authorities" on "Type" I find the following certificates "Uploaded":
|
|
Name
|
Subject
|
Valid from
|
Valid until
|
Type
|
Manage
|
|
|---|---|---|---|---|---|---|---|
|
|
lets-encrypt-r3
|
/C=US/O=Let's Encrypt/CN=R3 |
2020-09-04
|
2025-09-15
|
Uploaded
|
|
|
|
|
admin7_CA_60F4B3F1
|
/C=US/O=Let's Encrypt/CN=R3 |
2020-09-04
|
2025-09-15
|
Uploaded
|
|
|
|
|
admin_CA_6075D377
|
/C=US/O=Let's Encrypt/CN=R3 |
2020-10-07
|
2021-09-29
|
Uploaded
|
|
|
|
|
LetsEncrypt
|
/C=US/O=Let's Encrypt/CN=Let's Encrypt Authority X3 |
2016-10-06
|
2021-10-06
|
Uploaded
|
I have opened a support-case regarding this and they did the same as I tried....we took a backup, deleted all the above except the first one. Then downloaded and updated the first one with this:
https://letsencrypt.org/certs/lets-encrypt-r3.pem
Then we tried to reupload the certificate, but it still gave the same message.
Support imported the pfx on my computer:
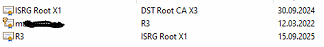
Support then uploaded some ISRG root certificate under "Certificate Authorities" but this rendered ALL the uploaded certificates unusable and we had to restore backup.
Support kinda gave up - took my certificate and tested this in a "lab" - they say they were able to upload the certificate (with no red X) and they sent me a .cer-file they told me to use, but it also gives the same message.
Anyone please help?
This thread was automatically locked due to age.