Hello folks.
Currently my team is reporting slow download and upload speeds far under our ISP internet plan. I've been trying to diagnose it, but everything I try doesn't seem to have any positive or negative affect.
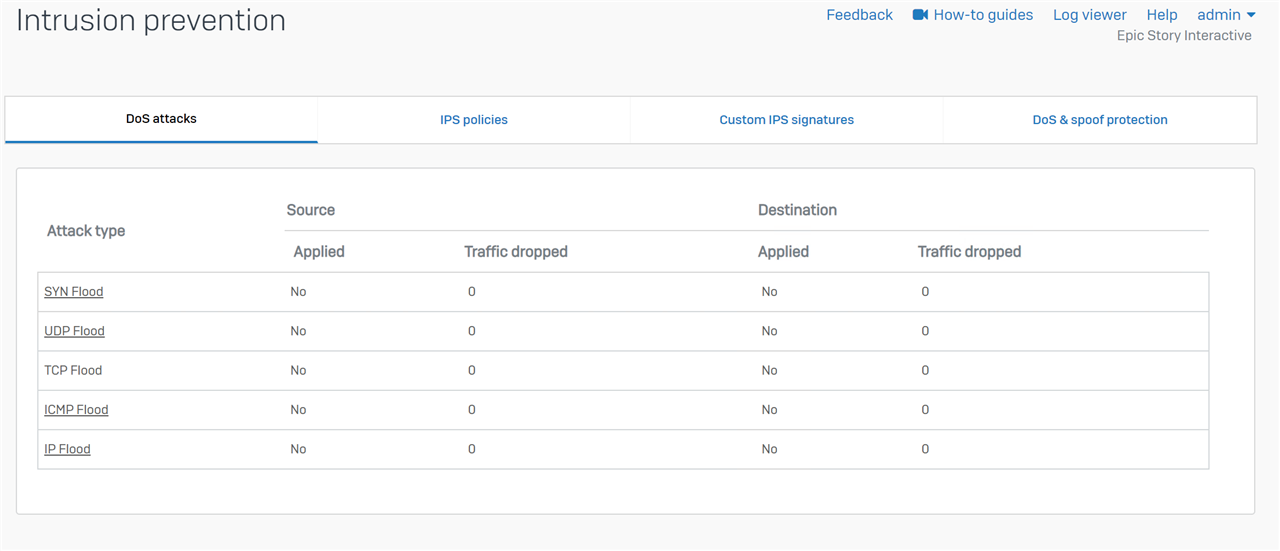
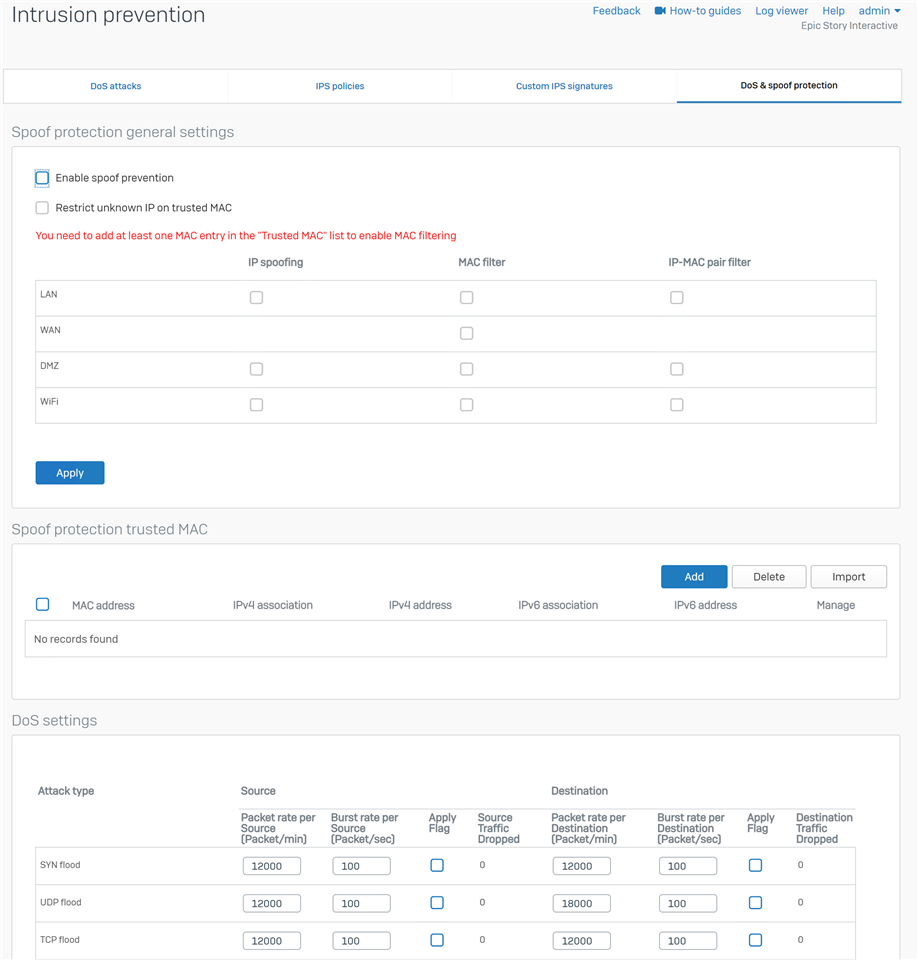
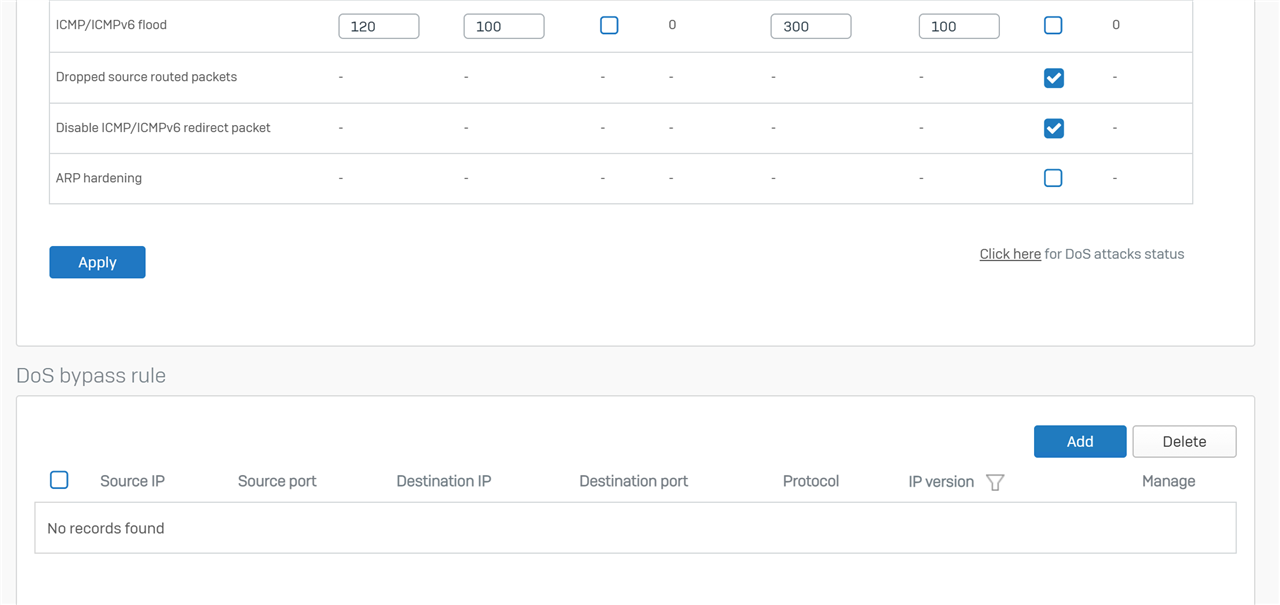
Here are my current settings. I wasn't sure what I should black out, so I kinda went crazy...which hopefully doesn't hinder someones ability to help.
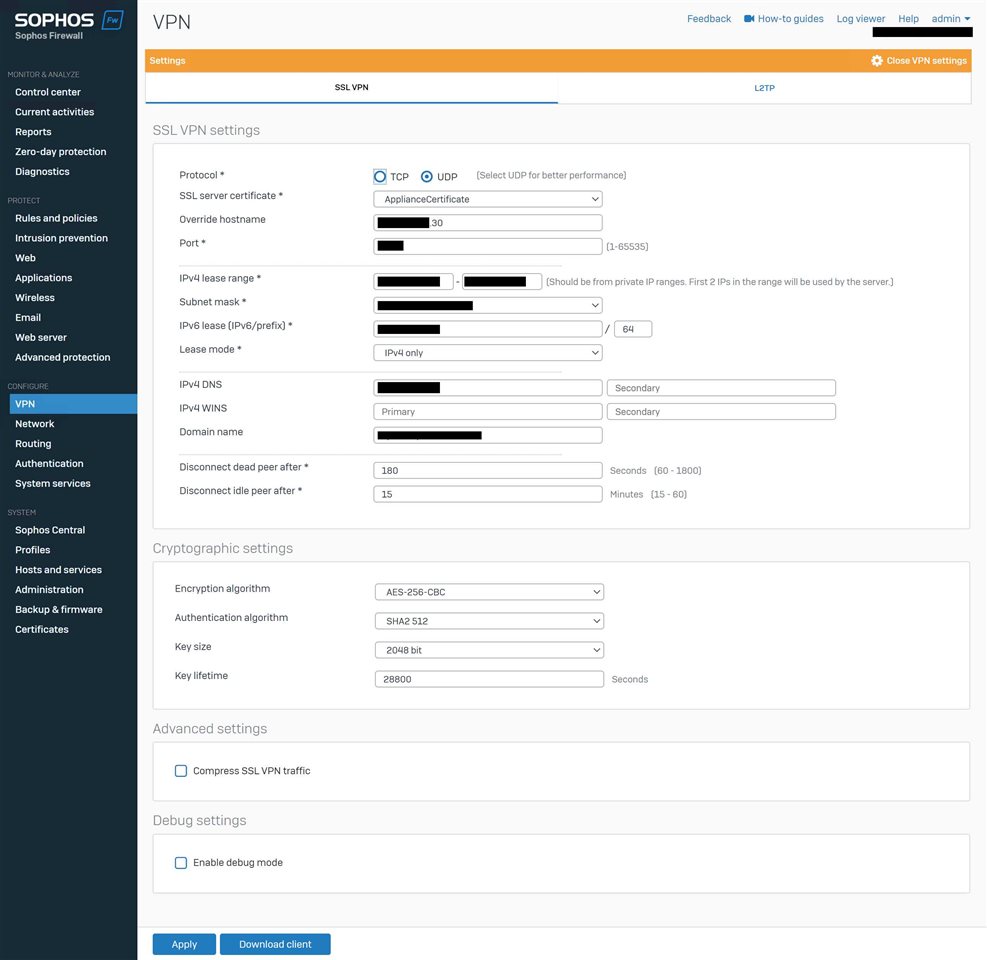
Beyond these SSL VPN settings, is there anything else I can setup to get the full ISP bandwidth for my users?
This thread was automatically locked due to age.