Our networks include a LAN (192.168.0.0/20) and a VPN area (172.x.x.0/24). There is a firewall rule allowing two-way routing between these two zones:
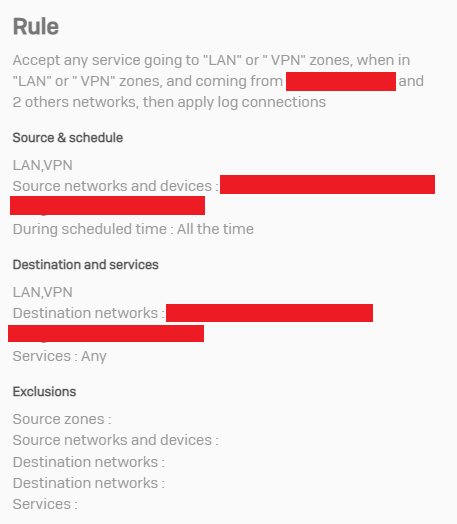
Now the problem we witness is that the firewall blocks VPN → LAN traffic unless it has seen traffic from the LAN host. . Initially, the above rule simply does not match:
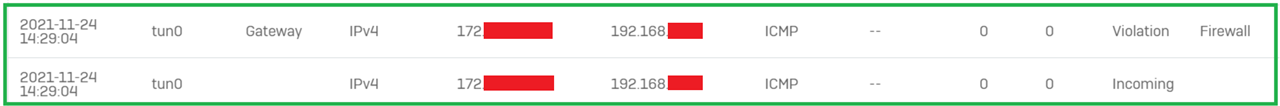
This happens regardless of the protocol (ICMP, TCP, UDP…)
Indeed the policy tester indicates that such traffic is prohibited: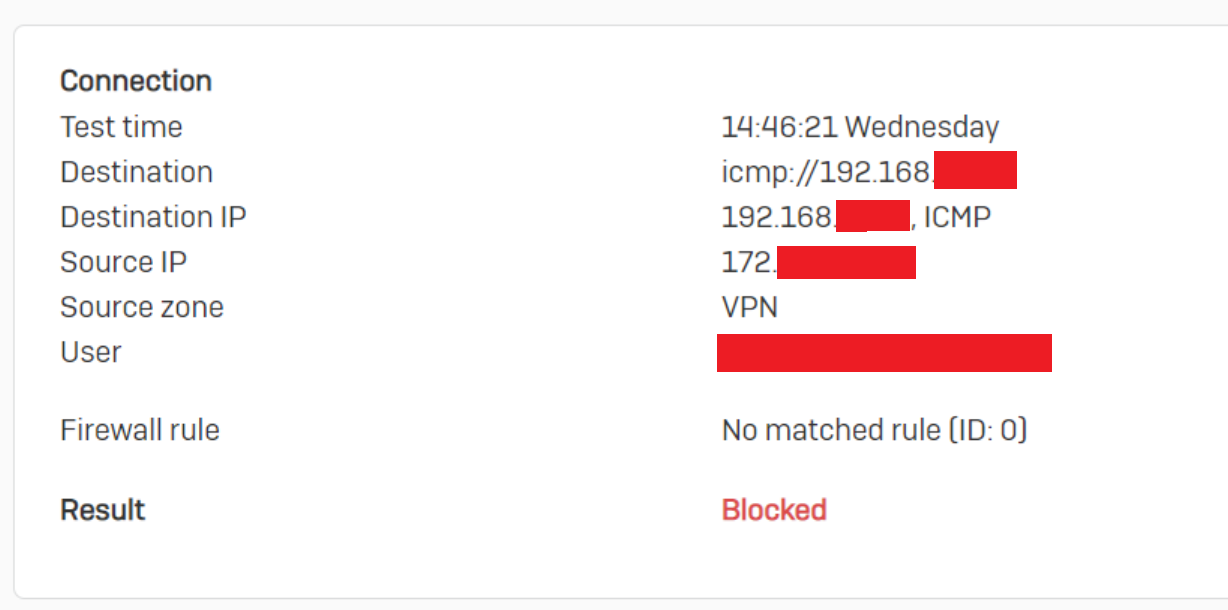
Now the really strange thing happens when I initiate random traffic from the LAN host (the destination in the above screenshots) that the firewall can see (e.g. connect to something on the internet, or broadcast a single UDP packet), and now suddenly the hosts gets “known” and VPN → LAN traffic is no longer blocked: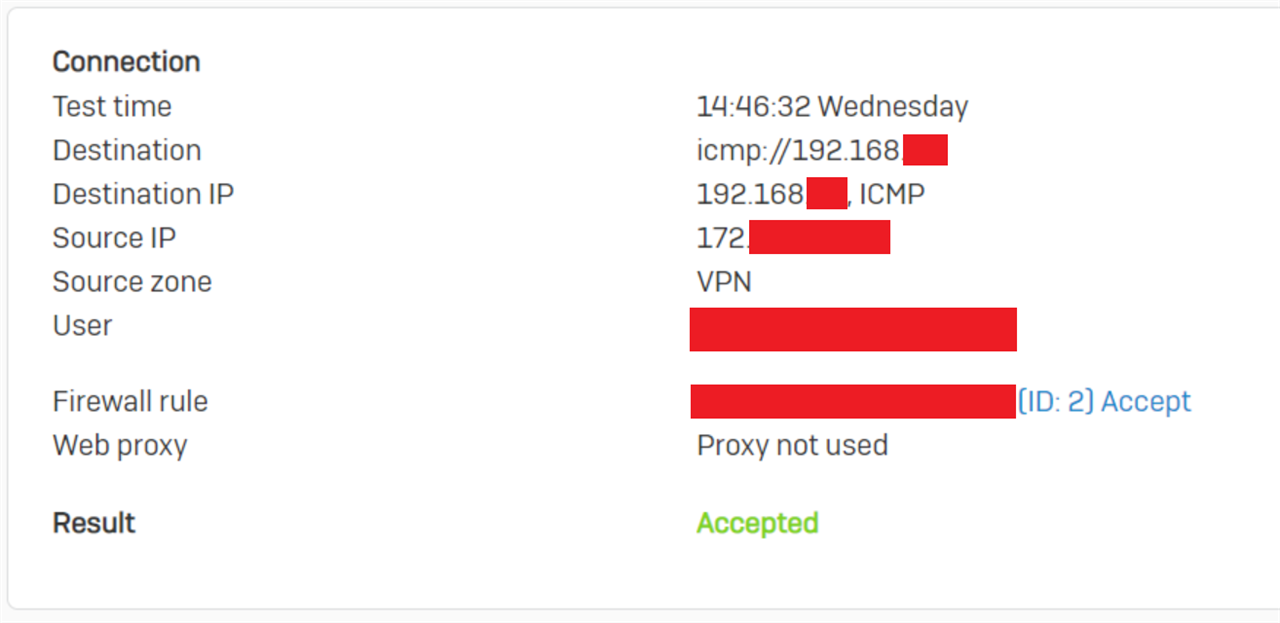
Then after some time of not seeing any traffic from the LAN host, the traffic is again blocked.
Does anyone understand what is happening?
Note: the issue appears unrelated to ARP, because it still happens if the target host is in the firewall’s ARP table (I even tried adding a PERM entry).
This thread was automatically locked due to age.


