Hello Community.
Im hosting some assets on Synology box. one of it is Synology Drive. Its accessible from WAN - mainly it works as "One Drive".
I have been create a discussion asking for help https://community.sophos.com/sophos-xg-firewall/f/discussions/131202/waf-inspection
Now when all is setup im seeing thones of false positive warrings in logs. I did tail -f /log/reverseproxy.log it shows:
[Sun Nov 14 21:14:58.253577 2021] [security2:error] [pid 28228:tid 139994878416640] [client SomeIP:64535] [client SomeIP] ModSecurity: Warning. Pattern match "(?i:[\\"'`]\\\\s*?(?:(?:n(?:and|ot)|(?:x?x)?or|between|\\\\|\\\\||and|div|&&)\\\\s+[\\\\s\\\\w]+=\\\\s*?\\\\w+\\\\s*?having\\\\s+|like(?:\\\\s+[\\\\s\\\\w]+=\\\\s*?\\\\w+\\\\s*?having\\\\s+|\\\\W*?[\\"'`\\\\d])|[^?\\\\w\\\\s=.,;)(]++\\\\s*?[(@\\"'`]*?\\\\s*?\\\\w+\\\\W+\\\\w|\\\\*\\\\s*?\\\\w+\\\\W+[\\"'`])|(?:unio ..." at ARGS:__cIpHeRtExT. [file "/usr/apache/conf/waf/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf"] [line "803"] [id "942260"] [msg "Detects basic SQL authentication bypass attempts 2/3"] [data "Matched Data: \\x22:\\x22cpK5zMwJbAprUmqMxSW9ZgYXsD3CALcCg1XaDKItG6jXPkubN91qQwnmRN6fpp8nANKEXr/i found within ARGS:__cIpHeRtExT: {\\x22rsa\\x22:\\x22cpK5zMwJbAprUmqMxSW9ZgYXsD3CALcCg1XaDKItG6jXPkubN91qQwnmRN6fpp8nANKEXr/iaCDX5DLJy76aOiWBJEXlG5m/3AGwGLeJQi3dLeGEWv PmgJjeReelZ86XrZeNGBopPrYoqZgYR5QaAqGTqEQaFOeEXPjXkS5nktMFZgTbe1 0DsBoi1226Bjd/e5gaZDx7YitGyBy8jXhnDSeNPeIbTuHIZx8d6VaXyq1kwmpqR6fqPVrvqWdKQsU1nEY41pfUeZcUC6mQnybuha2am9TRuWRpebObnukonwlLHYa7djc6vcHDO4NK961ymdaDkwYl5bC7AGEjHAu65kLz2etBZ8pHORJ2kAci6t..."] [severity "CRITICAL"] [ver "OWAS [hostname "FQDN_Name.synology.me"] [uri "/webman/login.cgi"] [unique_id "YZFuQpZ5F@glMrouUzA4UQAAAD8"], referer: FQDN_Name.synology.me:7001/
[Sun Nov 14 21:14:58.254527 2021] [security2:error] [pid 28228:tid 139994878416640] [client SomeIP:64535] [client SomeIP] ModSecurity: Warning. Pattern match "(?i:(?:[\\"'`](?:\\\\s*?(?:is\\\\s*?(?:[\\\\d.]+\\\\s*?\\\\W.*?[\\"'`]|\\\\d.+[\\"'`]?\\\\w)|\\\\d\\\\s*?(?:--|#))|(?:\\\\W+[\\\\w+-]+\\\\s*?=\\\\s*?\\\\d\\\\W+|\\\\|?[\\\\w-]{3,}[^\\\\w\\\\s.,]+)[\\"'`]|[\\\\%&<>^=]+\\\\d\\\\s*?(?:between|like|x?or|and|div|=))|(?i:n?and|x?x?or|div|like|between|not| ..." at ARGS:__cIpHeRtExT. [file "/usr/apache/conf/waf/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf"] [line "941"] [id "942340"] [msg "Detects basic SQL authentication bypass attempts 3/3"] [data "Matched Data: \\x22rsa\\x22:\\x22 found within ARGS:__cIpHeRtExT: {\\x22rsa\\x22:\\x22cpK5zMwJbAprUmqMxSW9ZgYXsD3CALcCg1XaDKItG6jXPkubN91qQwnmRN6fpp8nANKEXr/iaCDX5DLJy76aOiWBJEXlG5m/3AGwGLeJQi3dLeGEWv PmgJjeReelZ86XrZeNGBopPrYoqZgYR5QaAqGTqEQaFOeEXPjXkS5nktMFZgTbe1 0DsBoi1226Bjd/e5gaZDx7YitGyBy8jXhnDSeNPeIbTuHIZx8d6VaXyq1kwmpqR6fqPVrvqWdKQsU1nEY41pfUeZcUC6mQnybuha2am9TRuWRpebObnukonwlLHYa7djc6vcHDO4NK961ymdaDkwYl5bC7AGEjHAu65kLz2etBZ8pHORJ2kAci6tKbqvR1VWu2MMrJJc2MAyTCj shpmMuGVkfrV1U9/5IBGFMe/sJ8IlKlbjNTY2XMSu..."] [severity "CRITICAL"] [ver "OWAS [hostname "FQDN_Name.synology.me"] [uri "/webman/login.cgi"] [unique_id "YZFuQpZ5F@glMrouUzA4UQAAAD8"], referer: FQDN_Name.synology.me:7001/
[Sun Nov 14 21:14:58.255105 2021] [security2:error] [pid 28228:tid 139994878416640] [client SomeIP:64535] [client SomeIP] ModSecurity: Warning. Pattern match "((?:[~!@#\\\\$%\\\\^&\\\\*\\\\(\\\\)\\\\-\\\\+=\\\\{\\\\}\\\\[\\\\]\\\\|:;\\"'\\xc2\\xb4\\xe2\\x80\\x99\\xe2\\x80\\x98`<>][^~!@#\\\\$%\\\\^&\\\\*\\\\(\\\\)\\\\-\\\\+=\\\\{\\\\}\\\\[\\\\]\\\\|:;\\"'\\xc2\\xb4\\xe2\\x80\\x99\\xe2\\x80\\x98`<>]*?){12})" at ARGS:__cIpHeRtExT. [file "/usr/apache/conf/waf/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf"] [line "1255"] [id "942430"] [msg "Restricted SQL Character Anomaly Detection (args): # of special characters exceeded (12)"] [data "Matched Data: {\\x22rsa\\x22:\\x22cpK5zMwJbAprUmqMxSW9ZgYXsD3CALcCg1XaDKItG6jXPkubN91qQwnmRN6fpp8nANKEXr/iaCDX5DLJy76aOiWBJEXlG5m/3AGwGLeJQi3dLeGEWv PmgJjeReelZ86XrZeNGBopPrYoqZgYR5QaAqGTqEQaFOeEXPjXkS5nktMFZgTbe1 0DsBoi1226Bjd/e5gaZDx7YitGyBy8jXhnDSeNPeIbTuHIZx8d6VaXyq1kwmpqR6fqPVrvqWdKQsU1nEY41pfUeZcUC6mQnybuha2am9TRuWRpebObnukonwlLHYa7djc6vcHDO4NK961ymdaDkwYl5bC7AGEjHAu65kLz2etBZ8pHORJ2kAci6tKbqvR1VWu2MMrJJc2MAyTCj shpmMuGVkfrV1U9/5IBGFMe/sJ8IlKlbjNTY2XMSueDmHmSNsrzw4Jk5WwLY4XW1uXUjDRI778a56hgGDPFFlNbPjc..."] [severity "WARNING"] [ver "OWASP_CRS/3.2.0"] [tag "application-multi [hostname "FQDN_Name.synology.me"] [uri "/webman/login.cgi"] [unique_id "YZFuQpZ5F@glMrouUzA4UQAAAD8"], referer: FQDN_Name.synology.me:7001/
[Sun Nov 14 21:14:58.255594 2021] [security2:error] [pid 28228:tid 139994878416640] [client SomeIP:64535] [client SomeIP] ModSecurity: Warning. Pattern match "((?:[~!@#\\\\$%\\\\^&\\\\*\\\\(\\\\)\\\\-\\\\+=\\\\{\\\\}\\\\[\\\\]\\\\|:;\\"'\\xc2\\xb4\\xe2\\x80\\x99\\xe2\\x80\\x98`<>][^~!@#\\\\$%\\\\^&\\\\*\\\\(\\\\)\\\\-\\\\+=\\\\{\\\\}\\\\[\\\\]\\\\|:;\\"'\\xc2\\xb4\\xe2\\x80\\x99\\xe2\\x80\\x98`<>]*?){6})" at ARGS:__cIpHeRtExT. [file "/usr/apache/conf/waf/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf"] [line "1526"] [id "942431"] [msg "Restricted SQL Character Anomaly Detection (args): # of special characters exceeded (6)"] [data "Matched Data: {\\x22rsa\\x22:\\x22cpK5zMwJbAprUmqMxSW9ZgYXsD3CALcCg1XaDKItG6jXPkubN91qQwnmRN6fpp8nANKEXr/iaCDX5DLJy76aOiWBJEXlG5m/3AGwGLeJQi3dLeGEWv PmgJjeReelZ86XrZeNGBopPrYoqZgYR5QaAqGTqEQaFOeEXPjXkS5nktMFZgTbe1 0DsBoi1226Bjd/e5gaZDx7YitGyBy8jXhnDSeNPeIbTuHIZx8d6VaXyq1kwmpqR6fqPVrvqWdKQsU1nEY41pfUeZcUC6mQnybuha2am9TRuWRpebObnukonwlLHYa7djc6vcHDO4NK961ymdaDkwYl5bC7AGEjHAu65kLz2etBZ8pHORJ2kAci6tKbqvR1VWu2MMrJJc2MAyTCj shpmMuGVkfrV1U9/5IBGFMe/sJ8IlKlbjNTY2XMSueDmHmSNsrzw4Jk5WwLY4XW1uXUjDRI778a56hgGDPFFlNbPjc..."] [severity "WARNING"] [ver "OWASP_CRS/3.2.0"] [tag] [hostname "FQDN_Name.synology.me"] [uri "/webman/login.cgi"] [unique_id "YZFuQpZ5F@glMrouUzA4UQAAAD8"], referer: FQDN_Name.synology.me:7001/
[Sun Nov 14 21:14:58.255666 2021] [security2:error] [pid 28228:tid 139994878416640] [client SomeIP:64535] [client SomeIP] ModSecurity: Warning. Pattern match "\\\\W{4}" at ARGS:__cIpHeRtExT. [file "/usr/apache/conf/waf/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf"] [line "1559"] [id "942460"] [msg "Meta-Character Anomaly Detection Alert - Repetitive Non-Word Characters"] [data "Matched Data: =\\x22,\\x22 found within ARGS:__cIpHeRtExT: {\\x22rsa\\x22:\\x22cpK5zMwJbAprUmqMxSW9ZgYXsD3CALcCg1XaDKItG6jXPkubN91qQwnmRN6fpp8nANKEXr/iaCDX5DLJy76aOiWBJEXlG5m/3AGwGLeJQi3dLeGEWv PmgJjeReelZ86XrZeNGBopPrYoqZgYR5QaAqGTqEQaFOeEXPjXkS5nktMFZgTbe1 0DsBoi1226Bjd/e5gaZDx7YitGyBy8jXhnDSeNPeIbTuHIZx8d6VaXyq1kwmpqR6fqPVrvqWdKQsU1nEY41pfUeZcUC6mQnybuha2am9TRuWRpebObnukonwlLHYa7djc6vcHDO4NK961ymdaDkwYl5bC7AGEjHAu65kLz2etBZ8pHORJ2kAci6tKbqvR1VWu2MMrJJc2MAyTCj shpmMuGVkfrV1U9/5IBGFMe/sJ8IlKlbjNTY2XMSueDmHmS..."] [severity "WARNING"] [ver "OWASP_CRS/3.2.0"] [tag] [tag] [tag] [tag] [tag] [tag] [tag] [tag] [tag "OWASP_AppSe [hostname "FQDN_Name.synology.me"] [uri "/webman/login.cgi"] [unique_id "YZFuQpZ5F@glMrouUzA4UQAAAD8"], referer: FQDN_Name.synology.me:7001/
[Sun Nov 14 21:14:58.256559 2021] [security2:error] [pid 28228:tid 139994878416640] [client SomeIP:64535] [client SomeIP] ModSecurity: Access denied with code 403 (phase 2). Operator GE matched 5 at TX:anomaly_score. [file "/usr/apache/conf/waf/rules/REQUEST-949-BLOCKING-EVALUATION.conf"] [line "91"] [id "949110"] [msg "Inbound Anomaly Score Exceeded (Total Score: 24)"] [severity "CRITICAL"] [tag] [tag] [tag] [tag] [hostname "FQDN_Name.synology.me"] [uri "/webman/login.cgi"] [unique_id "YZFuQpZ5F@glMrouUzA4UQAAAD8"], referer: FQDN_Name.synology.me:7001/
[Sun Nov 14 21:14:58.256718 2021] [security2:error] [pid 28228:tid 139994878416640] [client SomeIP:64535] [client SomeIP] ModSecurity: Warning. Operator GE matched 5 at TX:inbound_anomaly_score. [file "/usr/apache/conf/waf/rules/RESPONSE-980-CORRELATION.conf"] [line "86"] [id "980130"] [msg "Inbound Anomaly Score Exceeded (Total Inbound Score: 24 - SQLI=19,XSS=0,RFI=0,LFI=0,RCE=0,PHPI=0,HTTP=0,SESS=0): individual paranoia level scores: 5, 13, 6, 0"] [tag] [hostname "FQDN_Name.synology.me"] [uri "/webman/login.cgi"] [unique_id "YZFuQpZ5F@glMrouUzA4UQAAAD8"], referer: FQDN_Name.synology.me:7001/
[Sun Nov 14 21:14:58.246184 2021] timestamp="1636920898" srcip="SomeIP" localip="SomeIP" user="-" method="POST" statuscode="403" reason="WAF Anomaly" extra="Inbound Anomaly Score Exceeded (Total Score: 24)" exceptions="-" duration="10579" url="/webman/login.cgi" server="FQDN_Name.synology.me:7001" referer="">FQDN_Name.synology.me:7001/" cookie="stay_login=0" set-cookie="-" recvbytes="1797" sentbytes="429" protocol="HTTP/1.1" ctype="text/html" uagent="Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0" querystring="?enable_syno_token=yes" websocket_scheme="-" websocket_protocol="-" websocket_key="-" websocket_version="-" ruleid="32"
I have pulled IDs (no information what they are meaning)
[id "942460"]
[id "942340"]
[id "942430"]
[id "942431"]
[id "942460"]
[id "949110"] - acording to sophos its not reccomended to add ths as exception
[id "980130"] - acording to sophos its not reccomended to add ths as exception.
i thought, ive got two options - add these IDs to exceptions or URL path mentioned below. Im not sure which is more secure or less.
url="/boaform/admin/formLogin"
uri "/webman/login.cgi"
OR
url="/webapi/*"
uri "/webman/*"
screen from configuration:
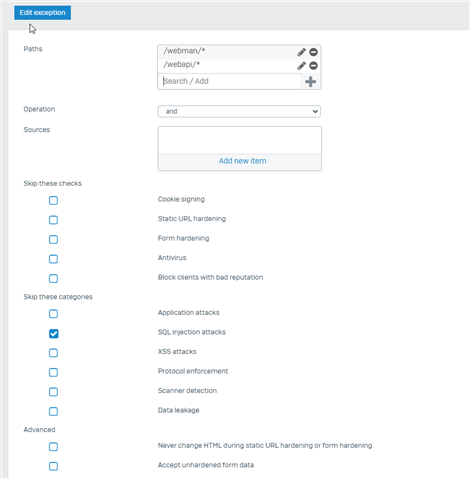
There maight be a few more.
What are your thoughts.
Thank you in advanced
This thread was automatically locked due to age.


