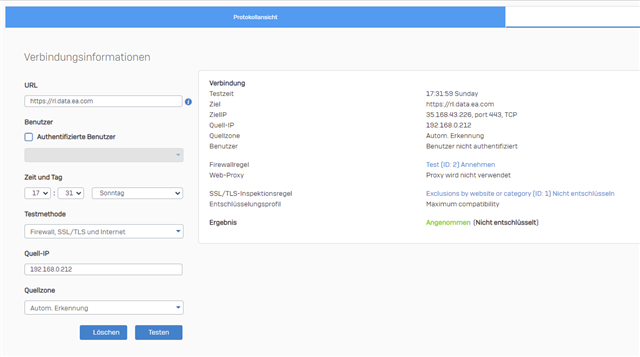
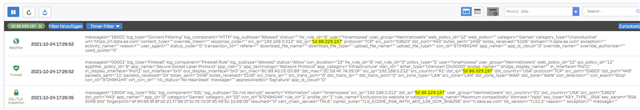
Hello,
I'm really not new to the XG system, but right now I got no clue what's going on.
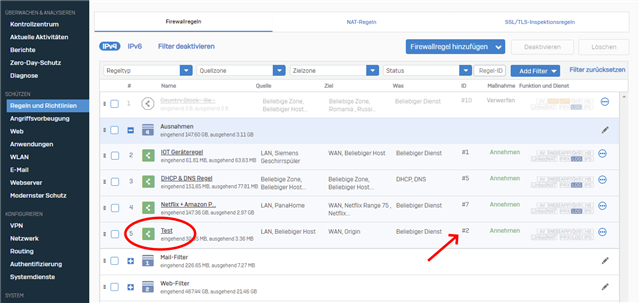
I defined a firewall rule (Test) in my 'exeptions' group. The rule ID is #2:
The destination is a FQDN-hostgroup "Origin" with several FQDN-hosts associated:
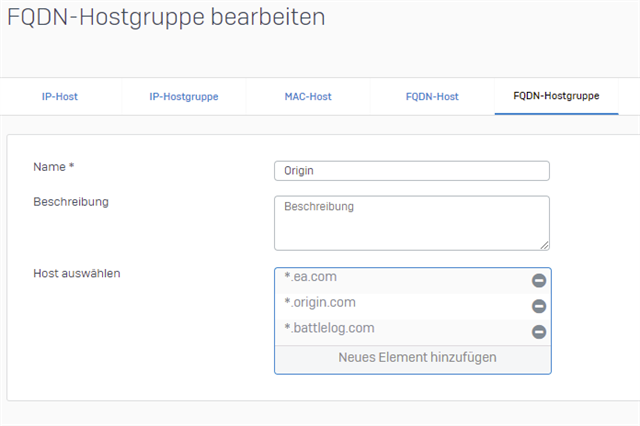
The "IP-collector" for the domain "ea.com" for example, works flawless and it collects all the associated IPs automatically:
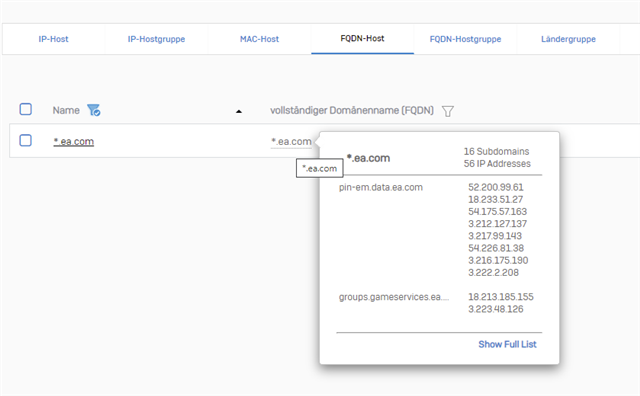
But when I now start a origin game like "BFV" the "Test" rule (#2) will not be triggered like expected. Instead of the Test rule, the rule with ID6 is triggered:
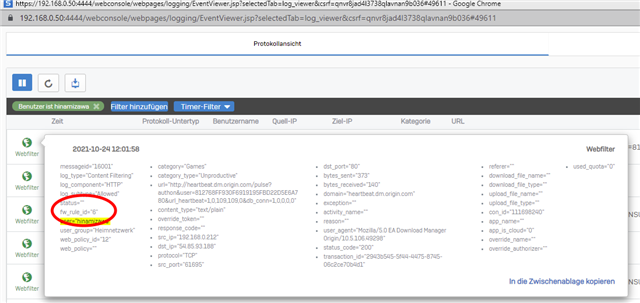
As you can see, this is a rule I defined under the "Web-Filter" group. It's my HTTPS-scanning rule.
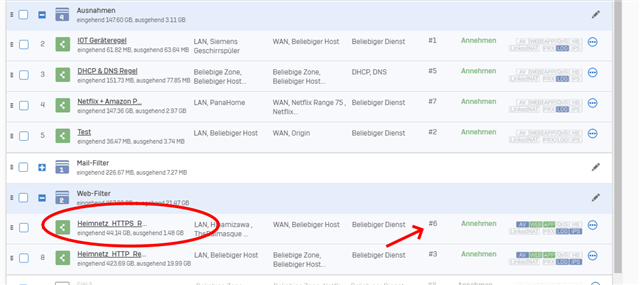
BTW: I use the DPI engine instead of proxy and already defined exeptions for the domains "ea.com" etc. destinations...
What I am doing wrong? Maybe it's really something simple I don't see right now...
Thank you.
This thread was automatically locked due to age.