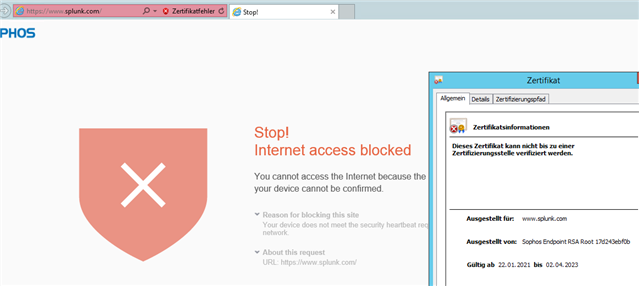
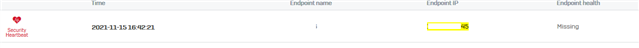
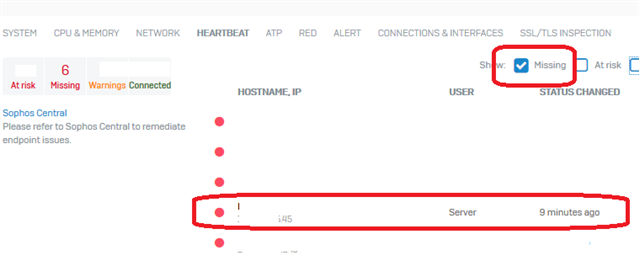
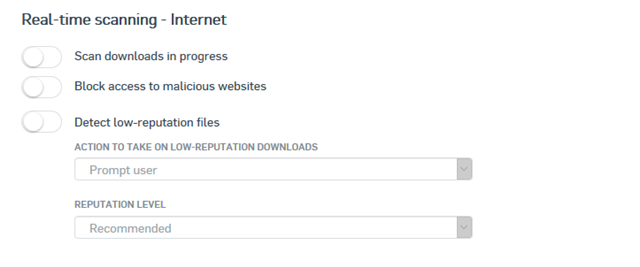
We had a customer put a case in yesterday about having the Server Endpoint Software configured to replace the failing SATC software. I advised I knew it was in the pipe but hadn't heard it had been released yet, and then he shared these two links:
Set up SATC with Sophos Server Protection
Sophos Firewall: SATC with Server Protection
I worked through it with him, and I'm happy to report it all worked a treat across multiple browsers and clients on his THIN Client. Just thought I'd give anyone a heads up who has been waiting and may have missed the announcement.
This thread was automatically locked due to age.