Just setup a VTI / route-based VPN with a customer who is using AWS VPC. Unfortunately, AWS side is using a link-local address (169.254.x.x/30) for the tunnel interfaces. I was able to assign the xfrm interface the needed IP, I can ping the aws side interface as well. The issue is I went to go and add a route to the VPC, but the WebAdmin won't allow this as it's a link-local address. Seems a lot of firewalls use this address space for this, so what kind of testing was done with RBVPNs in v18?
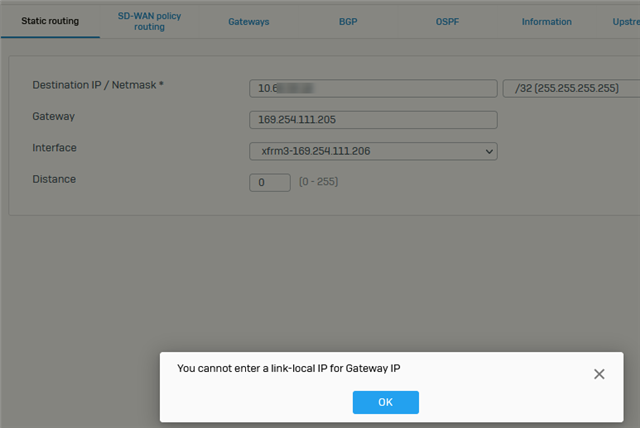
I was able to add this route in the advanced console, and reach the needed server in AWS, but I understand these kernel routes won't persist reboots, so what now? Any scripts that I can inject at boot to insert this route?
ip route add 10.0.0.1 via 169.254.111.205 proto zebra
This thread was automatically locked due to age.


