Hello community,
i have 2 Site2Site IPsec connections and 2 local LAN on the XG.
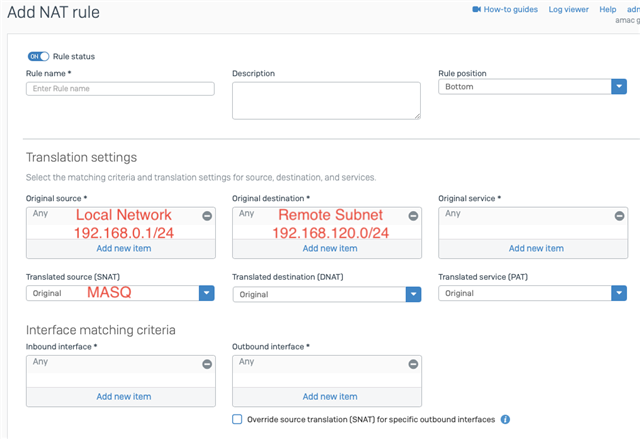
VPN connection 1:
Local Subnet: 192.168.1.0/24
Remote Subnet: 172.31.0.0/24
VPN connection 2:
Local Subnet: 192.168.2.0/24
Remote Subnet: 192.168.120.0/24
How can I connect the two local LANs on the XG so that I can access the remote subnets of the two VPN tunnels from both local LANs?
What is the best way to do this?
Thank you very much for your answers.
Best regards
This thread was automatically locked due to age.