Hi,
I have the following setup:
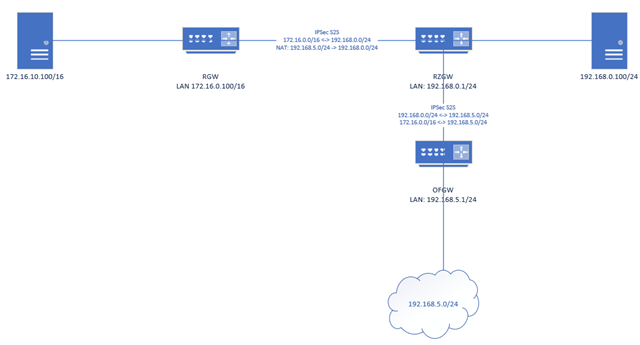
The ipsec policy between RGW and RZGW cannot be extended by the net 192.168.5.0/24 so I have to do a NAT (enabled in the vpn config screen).
The main goal that both nets (192.168.0.0/24 and 192.168.5.0/24) can access the remote host 172.16.10.100.
My problem is that RGW tries to ping one of my servers (192.168.0.100). I see the packets coming in via ipsec0, but the outgoing packets leave RZGW on the WAN interface where they get natted. I already tried to establish a SNAT, but there I cannot select ipsec0 as incoming/outgoing interface.
Can anyone point me in the right direction on how to create a nat rule (or multiple manual nat rules) to enable ping from RGW to 192.168.0.100 while maintaining the accessability of 172.16.10.100 from both local networks?
Cheers and thanks,
Nicki
This thread was automatically locked due to age.