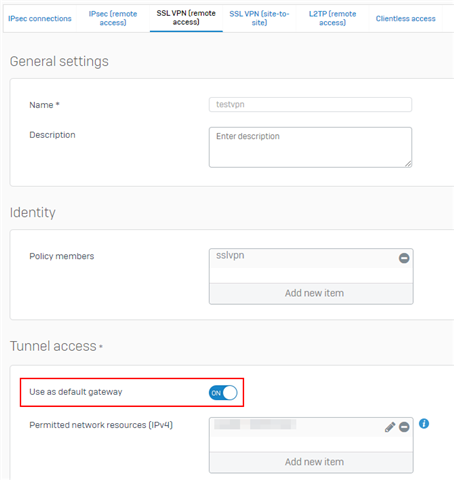
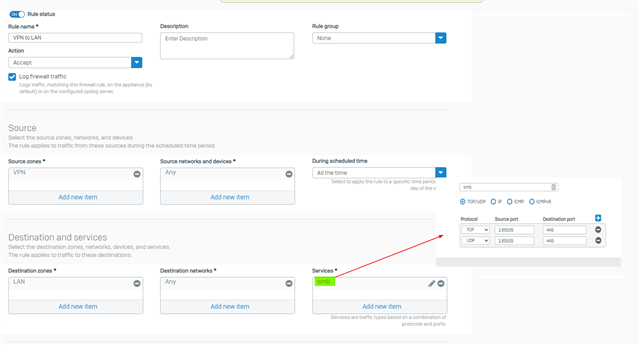
I don't think routes are being added when openvpn connects. Here is the issue..
I've set up Sopos XG with VMWARE Fusion, port forwarding is done on for WAN access, and testng va iPhone... I'e also set up seperate VM on LAN for SMB sharing of folder and enabled sharing on that with rules in place on Sophos.
UDP & TCP: 135-139 and port 445 from WAN to LAN rule
Testing Open VPN app on iPhone over cellular on purpose so I'm outside network 1.x Host only, 1x Bridged.nics.
imported .ovpn, and openVPN connects... It shows under "Current activities" on Sophos,, but despite seeing logs in openvpn, about "route added <IP address>:8843 doing a "what is my ip" check from iPhone while connected still resolves to mobile career, which indicates to routes are NOT added. Otherwise the VPN server would be shown instead.
This would be basically the same as a DNS leak from VPN providers.. It also explains why I cannot acts mapped share... Although I do see folder after I tap "connect to server" in the Files app on iOS, and enter details... "Content is unavailable" when I open share folder.
I just assumed since Sophos WAN has internet access, I just assumed that would be the same when connected remotely over VPN as well. (Unless I restricted it)
Everting is ok locally though, I cannot ping mobile when vpn connected and visa vera... Any suggestions ?
This thread was automatically locked due to age.