Hello,
what are the group rules of a firewall rule necessary for or what exactly do they do?
What influence do the group rule or when a firewall rule is created in a group ?
Greetings and thanks
This thread was automatically locked due to age.
Hello,
what are the group rules of a firewall rule necessary for or what exactly do they do?
What influence do the group rule or when a firewall rule is created in a group ?
Greetings and thanks

Hey,
Firewall groups are given for the admin's convenience as admins can group the rules for a similar purpose or source or destination etc..
XG follows a top-down approach when it comes to matching the traffic against the firewall rules. Firewall rules added in the group don't have any influence over the ones which aren’t.
Whichever rule is matched first (from top to bottom) will be applicable for that specific traffic.
Hello,
I understood the top-down principle, only not in connection with the group and the rule within it.
Could you please explain it differently again?
The firewall does not care about groups. It simply use the order you see, if you expand all groups. The groups are only cosmetic for you.
Only the automatic order option within the creation of a rule could mess with your system, if you create a new firewall rule, the firewall can try to figure out, which group is handy for you. But the order still does not matter.
__________________________________________________________________________________________________________________
cosmetic is always good :-)
ok, i always pay attention to the order of my rules.
I've always been careful in the SG.
But I have a problem.
I have deactivated all of my rules, except for the standard rule that is available during the XG reinstallation (#Default_Network_Policy).
This is my last rule.
If I deactivate this rule, I no longer have internet access. The standard NAT rules are also in place.
Since the group principle of the rules is cosmetics, that shouldn't be a problem. Whereby all my rules are solved by groups.
What could possibly be the problem?
I know that is really difficult to determine, from the point of view, all standard installation rules and NAT are still there.
Can you share a screenshot of the entire firewalls?
__________________________________________________________________________________________________________________
Your Rules have no Traffic counter. You see 0 Bytes, this means, this firewall does not hit. You need to check why those rules are not hitting.
Firewall rules only apply on Source, Destination and service. In terms of User based firewall rules, the source is replaced with the user information of live user.
__________________________________________________________________________________________________________________
Hi,
yes I also saw that a lot of my rules show no traffic. That surprises me too, that's why I fight for it all the time.
Unfortunately I don't understand where the problem can be.
I didn't quite understand what would happen if.
Ok, so as soon as I apply a live user, the source is replaced. That means, he already knows exactly which one he comes from.
But what can be wrong there? I also tried to determine the problem via the live protocol, but it doesn't quite work for me when the protocol was just to get an understanding of it.
Yes, now I am at a loss. !!!
Show me your Liveusers in current activities.
Try to switch the zone to ANY zone. Check the Services, move to ANY services, check if it will apply generally speaking to the source without a service.
Likely its a matter of matching (Service or Zone or live user).
__________________________________________________________________________________________________________________
Hi,
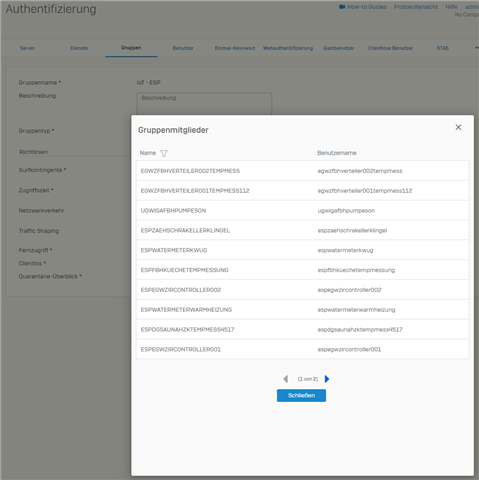
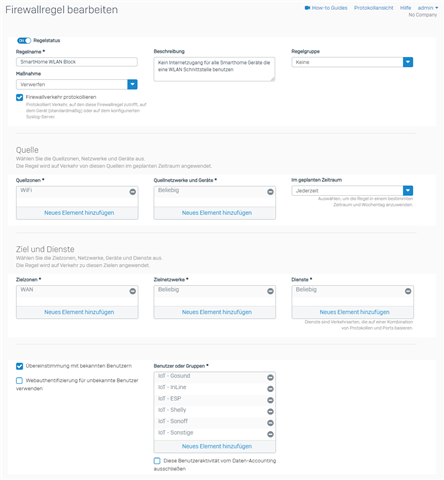
So I showed the firewall rule. In it you can see the groups of clientless users that should normally be used.
In the "IoT ESP" group, you can also see e.g. the two controllers 001/002 that are inserted there in the group.
I then carried out a firmware update on one of the controllers via the web server from the client and it received the firmware update, although the rule is active and the IoT ESP group is stored for the user.
The rule itself does not show any traffic that has passed over it.
Are the screenshots enough for you?
greeting