Hello,
can someone explain to me when I should use a MAC host and / or an IP host, when does that make sense.
Or do I even have to create both, although in my other thread it was already discussed why there is not a finished client object.
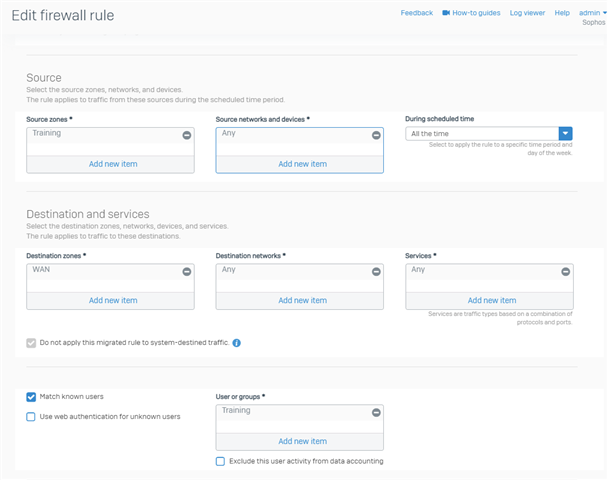
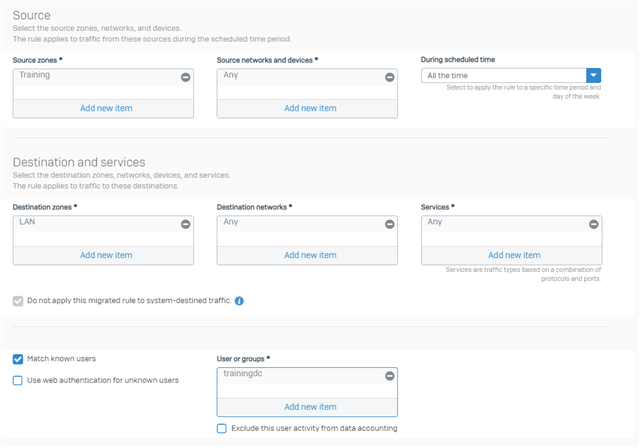
It is absolutely not understandable for me what it is supposed to create a MAC host or IP host separately.
Well, that would be worth an answer in my other thread.
Back again, when do I use a MAC host or IP host.
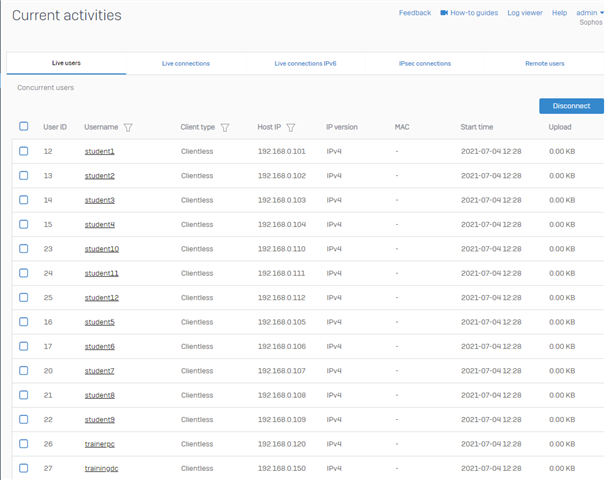
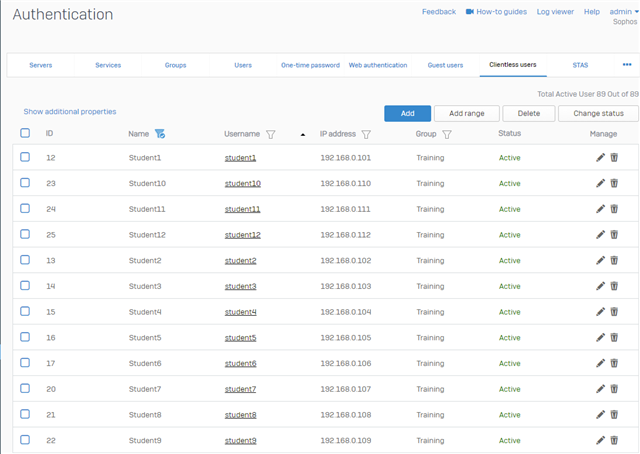
I absolutely do not understand this type, because a client basically has a MAC and IP, at least for my understanding when trying to work with rules.
Thanks and greetings
This thread was automatically locked due to age.