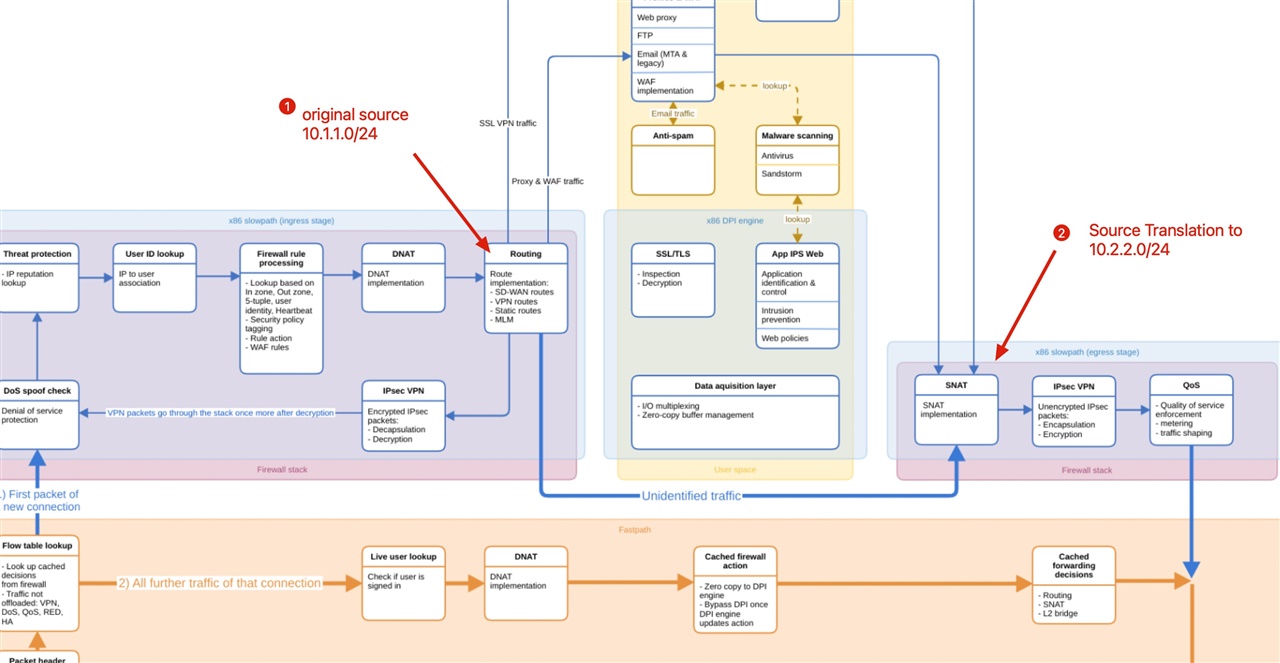
our customer has an IPSEC VPN Tunnel to a bunch of 10.x.x.x/y destinations.
Also he has a summarised 10.0.0.0/8 pointing towards another directly connected router (10.116.35.1).
they are not the same destinations. The IPSEC Traffic must go over the VPN Tunnel and the rest needs to go over the connected router.
Enjoy my super dope schema for this:
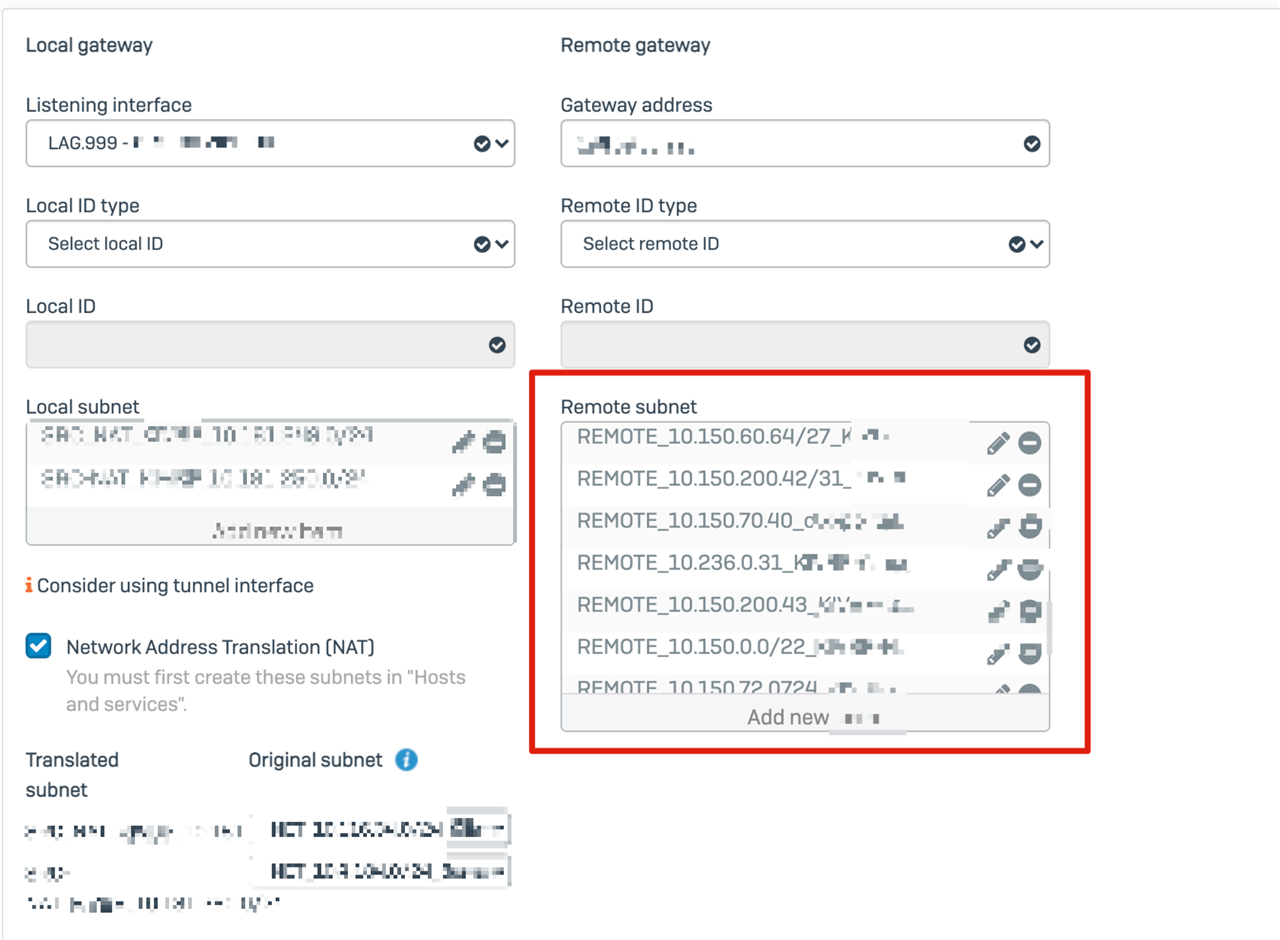
the achieve this we reconfigured the route precedence as below:
Sophos Firmware Version SFOS 18.0.4 MR-4
console> system route_precedence show
Routing Precedence:
1. VPN routes
2. Static routes
3. SD-WAN policy routes
now, regardless if we configure a static route or a policy based router for the 10.0.0.0/8 network, it will overwrite the IPSEC Tunnel routes and will route traffic for 10.x.x.x/y to the connected router.
SD-WAN Policy 10.0.0.0/8
IPSEC Tunnel Policy 10.x.x.x/y
Here is a ping example of the IPSEC Remote destination before the SD-WAN Rule is Disabled
SWC-RATH-GV00-1 ping 10.150.70.40 source-interface VL184_Server
PING 10.150.70.40 (10.150.70.40) from 10.4.184.184 : 56(84) bytes of data.
64 bytes from 10.150.70.40: icmp_seq=1 ttl=251 time=22.8 ms
64 bytes from 10.150.70.40: icmp_seq=2 ttl=251 time=20.2 ms
64 bytes from 10.150.70.40: icmp_seq=3 ttl=251 time=20.4 ms
64 bytes from 10.150.70.40: icmp_seq=4 ttl=251 time=22.3 ms
64 bytes from 10.150.70.40: icmp_seq=5 ttl=251 time=24.3 ms
64 bytes from 10.150.70.40: icmp_seq=6 ttl=251 time=17.7 ms
After it's active:
--- 10.150.70.40 ping statistics ---
6 packets transmitted, 6 received, 0% packet loss, time 5006ms
rtt min/avg/max/mdev = 17.781/21.336/24.335/2.119 ms
SWC-RATH-GV00-1 ping 10.150.70.40 source-interface VL184_Server
PING 10.150.70.40 (10.150.70.40) from 10.4.184.184 : 56(84) bytes of data.
^C
--- 10.150.70.40 ping statistics ---
6 packets transmitted, 0 received, 100% packet loss, time 5039ms
SWC-RATH-GV00-1 traceroute 10.150.200.45 source-interface VL184_Server
traceroute to 10.150.200.45 (10.150.200.45), 30 hops max, 60 byte packets
1 (10.116.35.10) 0.535 ms 0.454 ms 0.487 ms
2 (10.116.35.1) 5.531 ms 3.611 ms 1.682 ms. <-- router, not ipsec
3 (10.254.97.15) 13.688 ms 13.218 ms 17.153 ms
4 (10.254.98.5) 15.497 ms 15.137 ms 15.718 ms
5 (10.254.98.6) 15.052 ms 15.349 ms 15.046 ms^C
any ideas why this is not working?
This thread was automatically locked due to age.