Hello,
we use the SSLVPN authentication to apply different rules for users and the heartbeat to have the synced security.
Sometimes the user still connected to the VPN but not visible in the live user, in this case the rules with match known user not work! He need to reconnect the vpn to be visible again.
I found on the log a lot of error in the authentication tab related to heartbeat. All heartbeat have the status FAILED.
If i compare with SSLVPN, the @domain is visible and the authentication work fine.
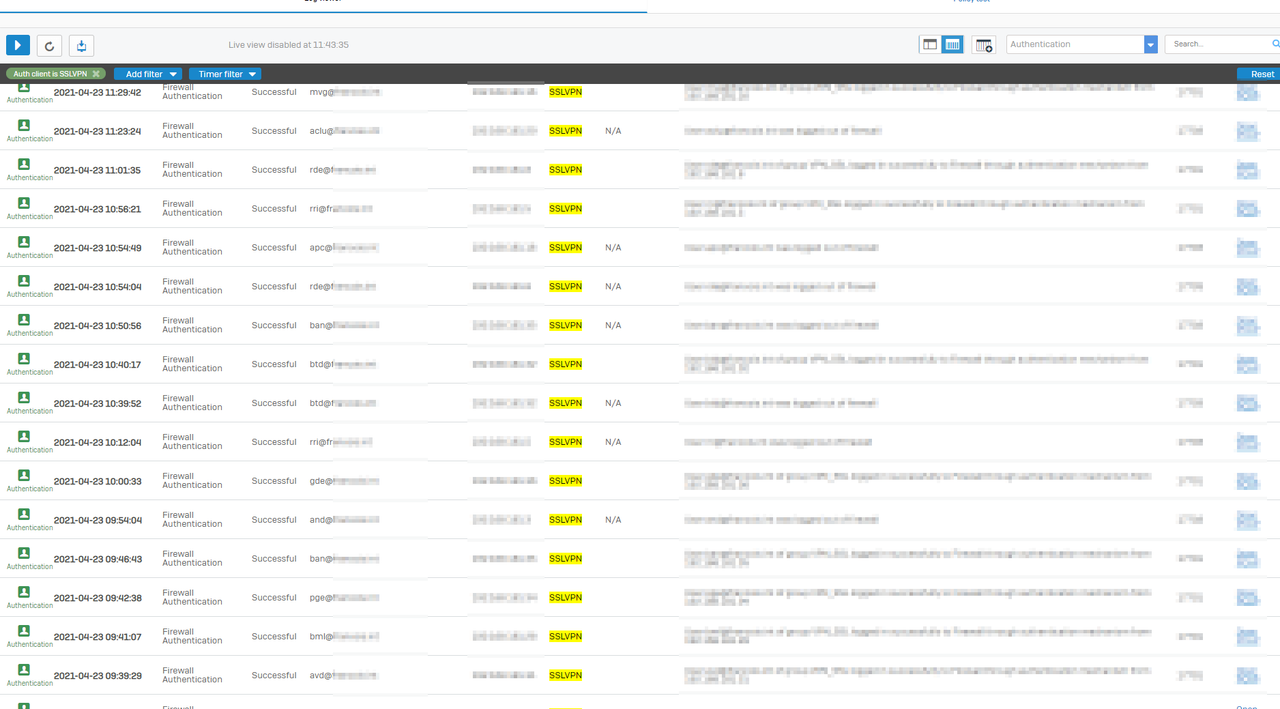
For the problematic user, we can see the logout in the log but on the desktop ,the vpn still connected !
Any idea why the heartbeat doesn't return the domain? Could be the cause of my problem? Thank you
This thread was automatically locked due to age.


