Hello,
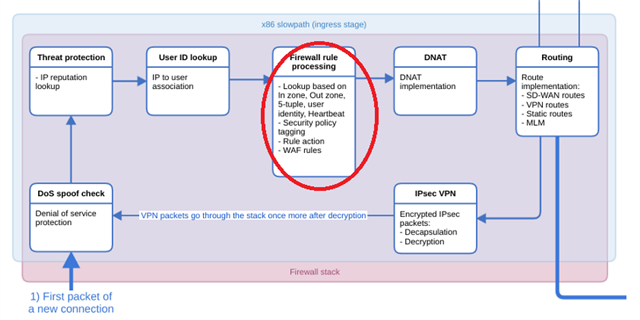
I created a Countryblock Rule as described here (https://docs.sophos.com/nsg/sophos-firewall/18.0/Help/en-us/webhelp/onlinehelp/nsg/sfos/tasks/CreateFirewallSecurityRule.html) but this rule does not match.
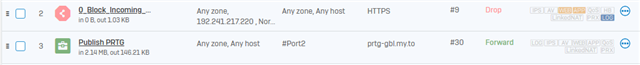
My published Webserver must not available outside my Country (one in Europe).
On my Deviceaccess / WAN Zone there ist nothing enabled and there is no ACL.
In my Webserver Log I see many acces from USA, China and so on.
Why?
How can I fix it?
sincerly
Guenter
This thread was automatically locked due to age.