Hi folks,
another post on my issues about creating a firewall hairpin nat rule.
I have an NTP server on my network and I want devices to use it as a reference time source. I know the device works when I change network devices to query it for time, they update correctly.
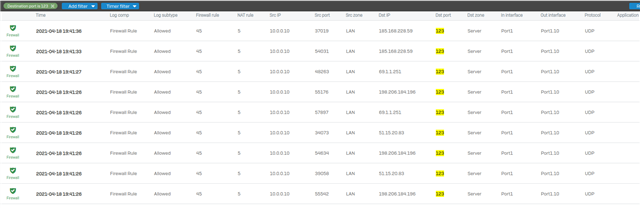
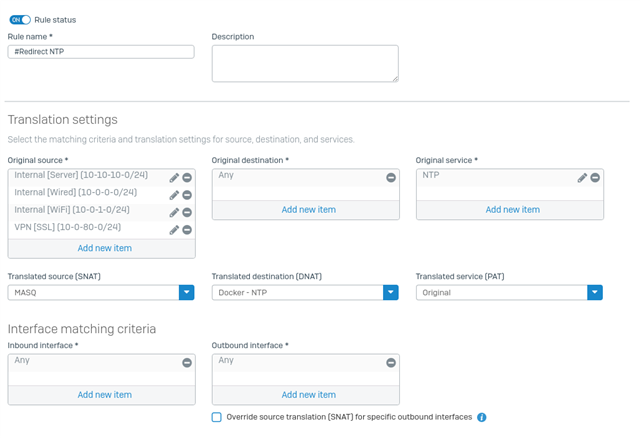
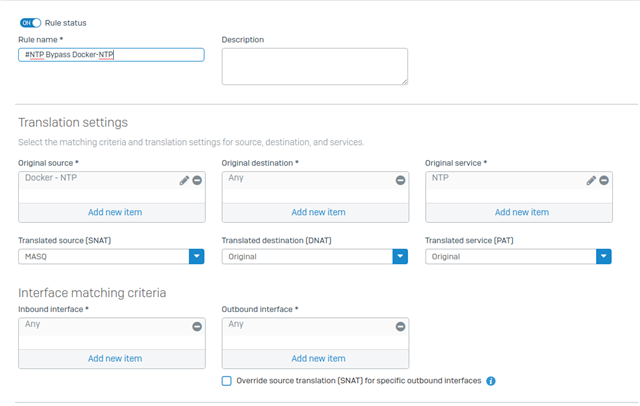
When I built my own firewall rule using a linked NAT rule there was lots of queries to the rule but nothing was returned.
So, I have decided to use the XG build a server access rule.
I think one of the questions in the create wizard is wrong
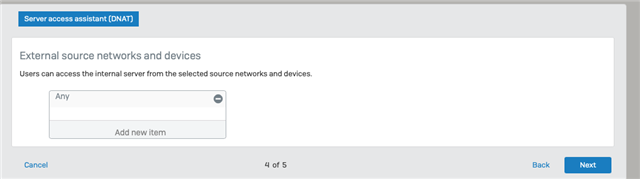
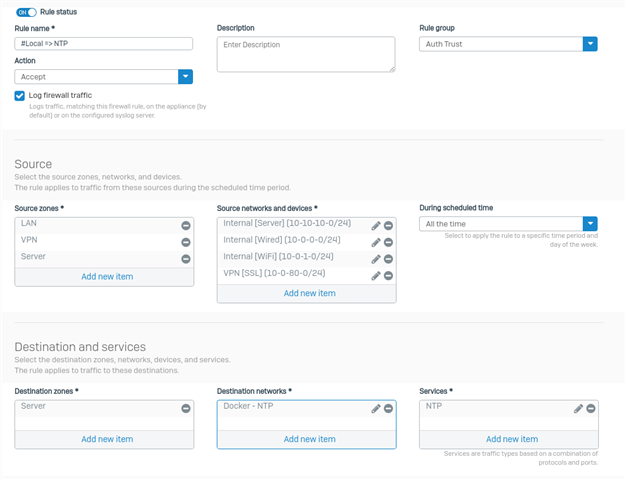
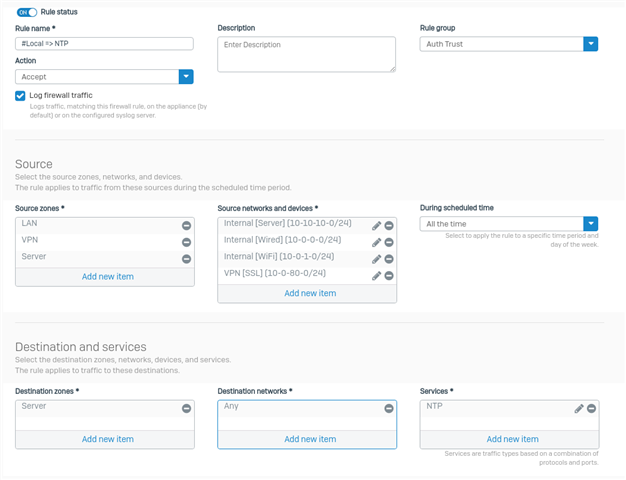
It asks for the external source networks and devices, but never asks for the internal networks. You can add your internal networks which I did.
Next issue is the reflexive rule automatically created does not use the required service as entered in previous pages, just uses ANY which allows all traffic to bypass the specific NAT and linked NAT rules. Again you can change it to the required service.
Next issue is the created firewall rule appears to be wrong.
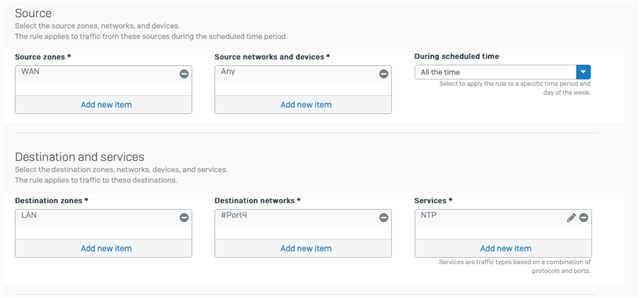
Destination zone is LAN but the destination network is the external interface which is a WAN zone.
The result is the rule does not work.
I have tried creating a FQDN for the external internal access to the NTP, but there is nowhere to add it to the rule along with a number of other issues of trying to add another external url for the same address, the XG does not like it.
Please advise what is required to make the hairpin NAT work. I have read the KBA and followed that document and ended up with the above issues.
Ian
.
This thread was automatically locked due to age.