Hello,
I do not understand how XG's Application Control work in detail (under the hood). Are any documentation somewhere?
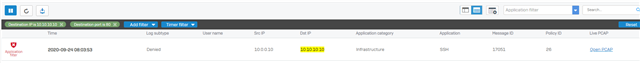
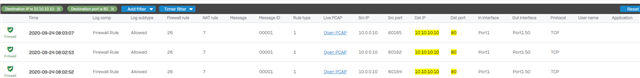
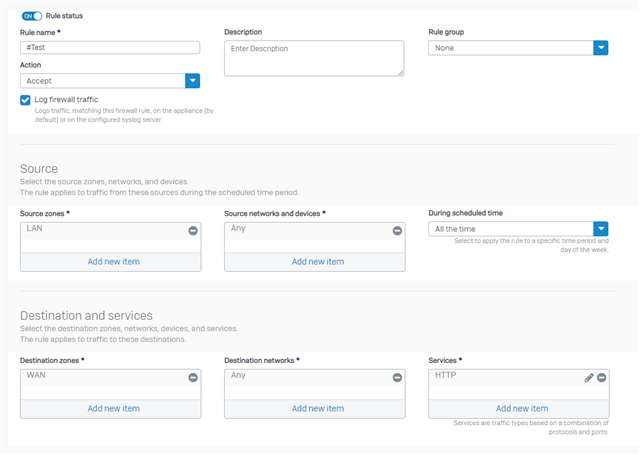
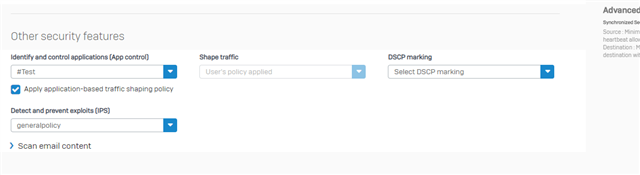
I have to control and restrict some Traffic between LAN and Production due to written regulation of security.
e.g. for understanding
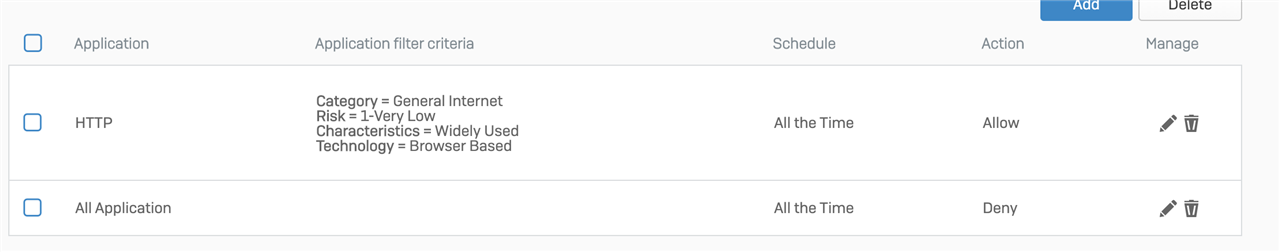
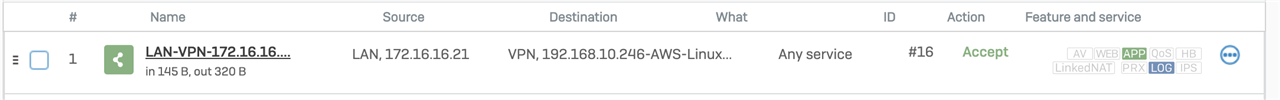
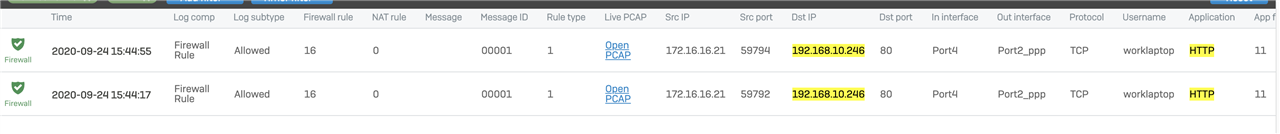
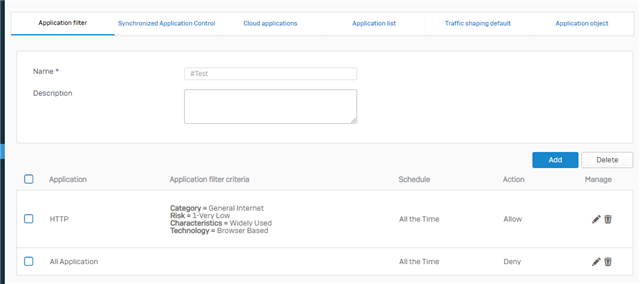
- LAN->Production:
- Allow Port 80 if it is HTTP
- Allow Port 25 if it is STMP
- Block all Traffic in all other cases
In this example we have to Block HTTP on Port 25.
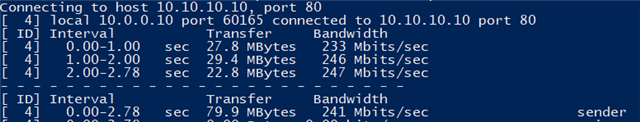
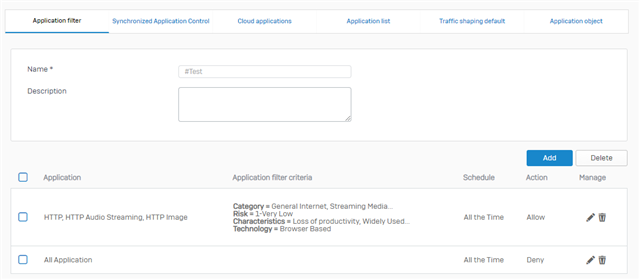
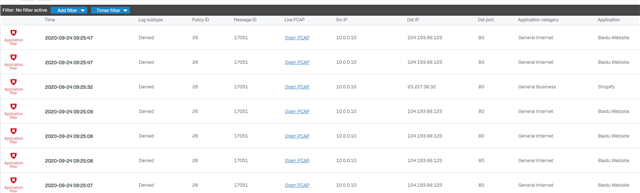
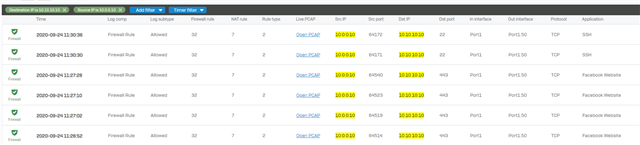
How can I solve this with Sophos XG?
sincerly
Guenter
This thread was automatically locked due to age.