Networking has evolved substantially over the last few years with more users working remotely, networks becoming more distributed, and cloud application usage exploding. Sophos is ensuring you keep pace with new products like ZTNA for remote workers, and now an extremely powerful and helpful Sophos Firewall release with Xstream SD-WAN.
SFOS v19 delivers greatly enhanced SD-WAN, VPN, and networking capabilities, enabling you to easily meet your networking goals, while making day-to-day management even easier.
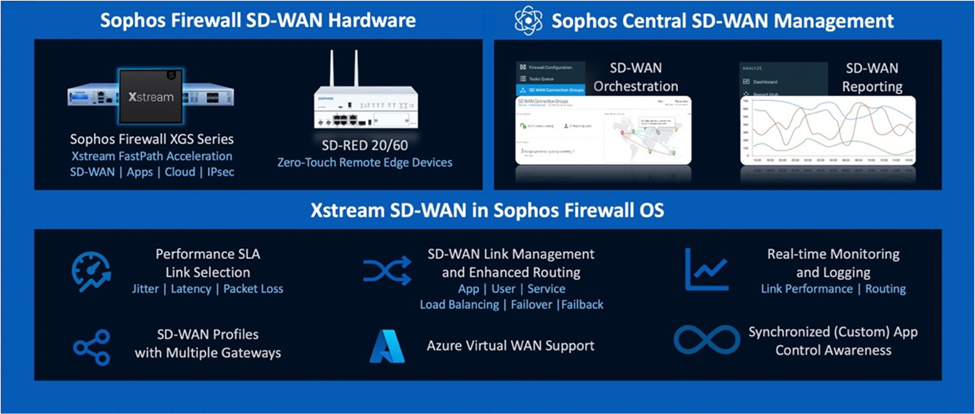
SFOS v19 Highlights:
- Xstream SD-WAN utilizing the powerful performance of the Xstream Flow Processors in all XGS Series appliances to put IPsec traffic on the FastPath resulting in up to a 5x VPN performance improvement
- Performance-Based Link Selection ensures your most important traffic is routed over your best performing WAN connection, based upon latency, jitter, or packet loss
- Zero-Impact Transitions between WAN links ensures end-user applications are not impacted by ISP outages or disruption
- SD-WAN Orchestration in Sophos Central enables you to quickly and easily setup complex site-to-site VPN overlay networks with just a few clicks
- VPN Enhancements make it much easier and more intuitive to manage your site-to-site and remote-access VPN connections including a new AWS VPC import tool
- New Search Capabilities allow you to quickly find exactly what you’re looking for, both in the product, and in your networking objects when building rules
The full list of new features is available in the What’s New PDF and you can take a quick tour of the new features in this video:
How to Get the Firmware, Documentation and Training
As usual, Sophos Firewall OS v19 is a free upgrade for all licensed Sophos Firewall customers and should be applied to all supported firewall devices as soon as possible as it not only contains great features and performance enhancements, but also important security fixes.
You can manually download SFOS v19 from Licensing Portal and update anytime. Otherwise, it will be rolled out to all connected devices over the coming weeks. A notification will appear on your local device or Sophos Central management console when the update is available allowing you to schedule the update at your convenience.
Sophos Firewall OS v19 is a fully supported upgrade from v17.5 MR14 and later, v18 MR3 and later and all previous versions of v18.5 including v18.5 MR3. Please refer to the Upgrade information tab in the release notes for more details.
Check out the SFOS v19 release notes for full details.
Full product documentation is available online and within the product.
Update training (for v18.5 to v19) is available on the Sophos Training Portal.
Learn More About Sophos Firewall
If you’re new to Sophos Firewall and the new XGS Series Firewall Appliances, they set the standard for firewall protection and performance, ensuring you get the most value for your firewall investment with unique features you just can’t find anywhere else:
- Unmatched Visibility with industry-leading TLS inspection, dashboarding, and reporting
- Powerful Protection with the new streaming DPI engine, Zero-Day Threat Protection, and Xstream Flow Processors in every XGS Series appliance
- Automated Response to isolate any active threat on your network with Synchronized Security
- Easy Cloud-Management for your Firewalls, Reporting, ZTNA, Endpoint, and other Sophos products through Sophos Central
- The Full-Stack of network security solutions that help you extend your secure network anywhere it needs to be with Sophos ZTNA, SD-RED devices, our new Sophos Switch product line and APX Wireless Access Points – all managed from Sophos Central.
Get started today with a 30-day free trial, or download our Sophos Firewall Solution Brief to learn more about how Sophos Firewall can transform your network protection.
Sincerely,
Sophos Firewall Product Team


-

Cameron Savage1
-
Cancel
-
Vote Up
0
Vote Down
-
-
More
-
Cancel
Comment-

Cameron Savage1
-
Cancel
-
Vote Up
0
Vote Down
-
-
More
-
Cancel
Children