Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Overview
This recommended reading shows that security in AWS operates under a shared security responsibility model. AWS is responsible for the security of the underlying cloud infrastructure, and the customer is responsible for securing workloads deployed into their AWS accounts. This model gives customers the flexibility and agility needed to implement the most applicable security controls for their business functions in AWS. They can tightly restrict access to environments that process or hold sensitive data while deploying less stringent controls for information they want to make public.
To help customers with their security responsibilities, AWS offers many security services designed to help implement an optimal cloud security posture. AWS also provides security best practices and guidance and suggests that customers consider adding additional security tools from the AWS Marketplace. These 3rd party solutions are provided by AWS partners such as Sophos and offer industry-leading products that are equivalent, identical to, and/or integrate with existing controls in your on-premises environments. These products complement the AWS security services and help customers install comprehensive security across their cloud and on-premises environments.
Despite these resources, many customers still struggle with ensuring they are properly protected in AWS. This is often due to the complexity related to properly deploying and managing these services and tools, and the lack of expertise needed to identify potential threats and/or compromises.
Sophos Threat Protection, Monitoring, and Response on AWS
To help address the challenges mentioned, AWS and Sophos have partnered up to offer the Sophos Threat Protection, Monitoring, and Response Package on AWS. The offering combines key AWS security services with Sophos cloud security products, a cloud-based Central management platform, the Sophos Managed Threat Response service, and additional options for extending coverage to on-premise networks, remote users, and other cloud platforms. The service can be purchased directly via AWS Marketplace and deployed by a customer with assistance from the Sophos Professional Services team or using a Sophos authorized Managed Service Provider partner.
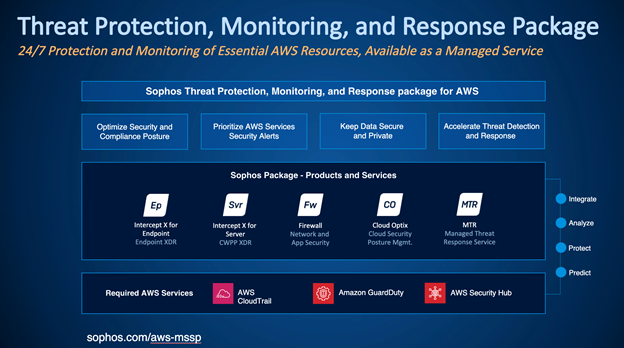
Sophos Threat Protection, Monitoring, and Response Package Details
The Sophos Threat Protection, Monitoring, and Response package consists of three required Sophos solutions to protect your AWS VPCs and workloads and integrates with both AWS security services and the Sophos Managed Threat Response service. The required Sophos products are:
Sophos Intercept X Advanced for Server with XDR: Sophos Intercept X for Server employs a comprehensive, defense-in-depth approach to server security. A combination of powerful defensive techniques and visibility capabilities gives organizations the best host protection against the latest threats.
- Stop Unknown Threats Deep learning AI in Intercept X for Server excels at detecting and blocking malware even when it hasn’t been seen before. It does this by scrutinizing file attributes from hundreds of millions of samples to identify threats without a signature.
- Block Ransomware Intercept X for Server includes advanced anti-ransomware capabilities that detect and block the malicious encryption processes used in ransomware attacks. Files that have been encrypted will be rolled back to a safe state, minimizing any impact to business productivity.
- Prevent Exploits Anti-exploit technology stops the exploit techniques that attackers rely on to compromise devices, steal credentials, and distribute malware. By stopping the techniques used throughout the attack chain, Intercept X for Server keeps your organization secure against file-less attacks and zero-day exploits.
- Control Your Servers Ensure only what you want can run. Server Lockdown (whitelisting) makes sure that only applications you have approved can run on a server. File Integrity Monitoring will notify you if there are unauthorized attempts to change critical files.
Sophos Cloud Optix: Cloud Optix is an agentless cloud security posture management solution that helps customers identify vulnerabilities, ensure compliance, and respond to threats in the cloud faster. Cloud Optix provides a complete picture of cloud resources and security configurations across AWS, Azure, Google Cloud, Kubernetes, and DevOps environments, enabling security teams to focus on and fix critical security vulnerabilities before they’re identified and exploited in cyberattacks.
- Complete Cloud Security Posture Management Sophos Cloud Optix provides a complete picture of cloud resources across multi-cloud environments. Monitoring costs, detecting insecure configurations and deployments, access anomalies, over-privileged IAM roles, and compliance failures from development to the ongoing security of live services.
- Identify and Respond to Threats Faster Focus on and fix your most critical security vulnerabilities before they’re identified and exploited in cyberattacks. By identifying and risk-profiling security, compliance, and cloud spend risks, Cloud Optix ensures teams respond faster, providing contextual alerts that group affected resources with detailed remediation steps.
- Security at The Pace of DevOps Block vulnerabilities in container images and infrastructure-as-code templates predeployment with Cloud Optix. Seamlessly integrate Sophos security and compliance checks at any stage of development to maintain the pace of DevOps without introducing threats into production environments.
- Manage Permissions Before They’re Exploited Cloud Optix analyzes complex, interwoven Identity and Access Management (IAM) roles to visualize relationships, making it simpler to manage access privileges for user, group and cloud service roles. Guiding you on where to make IAM policy updates with the cloud provider before over-privileged IAM access is exploited.
- Reduce Compliance Cost and Complexity Sophos Cloud Optix reduces the cost and complexity of compliance with policies that automatically map to your environments, producing audit-ready reports without diverting resources from other projects. Compliance and security best practice policies include: GDPR, HIPAA, PCI DSS, SOC2, ISO27001, FFIEC, EBU R 143, FedRAMP, CIS Benchmark Level 1 and Level 2 for AWS, Azure, Google Cloud and Kubernetes.
Sophos Firewall on AWS: Sophos Firewall makes security and compliance easy with the best next-generation protection against the latest advanced threats, including ransomware, crypto mining, bots, worms, hacks, breaches, and APTs with unique and innovative technologies designed to catch threats. We haven’t even seen it yet.
- SophosLabs Threat Intelligence, powered by deep learning, identifies new and zero-day threats before they infiltrate your network.
- Industry-leading IPS performance and protection ensure exploitive malware and hackers are stopped dead.
- Sandstorm sandboxing provides the ultimate in affordable protection by analyzing suspicious files in a safe cloud environment using the latest technology from Intercept X.
- An integrated web application firewall protects your cloud servers and helps meet compliance requirements with protection from SQL injection and cross-site scripting attacks, URL and form hardening, dual malware engines, GeoIP lists, TLS offloading, reverse authentication, and more.
Each of the solutions automatically sends information to the Sophos Managed Threat Response service, which is used to hunt for indicators of malicious activity proactively. The Managed Threat Response service includes 24/7 threat hunting, detection, and response delivered by an expert team as a fully-managed service.
- Proactively hunt for and validate potential threats and incidents.
- Use all available information to determine the scope and severity of threats.
- Apply the appropriate business context for valid threats.
- Start actions to remotely disrupt, contain, and neutralize threats.
- Provide actionable advice for addressing the root cause of recurring incidents.
Customers using the Sophos Threat Protection, Monitoring, and Response service can also add Sophos Endpoint protection to protect users.
- Central Intercept X Advanced with XDR and MTR Advanced Windows, Mac, and Linux endpoint protection features include Ransomware protection, deep-learning malware detection, exploit mitigation, file-less attack prevention, XDR, and MTR.
Required AWS Security Services
Key AWS Security Services gather infrastructure and service-level security information, which is then passed on to Sophos for further analysis. The services below must be turned on in each AWS account and region that the Sophos TMP covers on the AWS offering.
-
Amazon CloudTrail: AWS CloudTrail is a service that enables governance, compliance, operational auditing, and risk auditing of your AWS account. Note that CloudTrail is turned on automatically as part of the Cloud Optix setup.
-
AWS GuardDuty: Amazon GuardDuty is a continuous security monitoring service that analyzes and processes VPC Flow Logs, AWS CloudTrail management event logs, CloudTrail S3 data event logs, and DNS logs to identify unexpected and potentially unauthorized and malicious activity within your AWS environment. Note that GuardDuty must be manually enabled from the AWS console in each AWS region you want to support and then connected to Sophos Cloud Optix using the provided integration script.
- AWS Security Hub: AWS Security Hub gives you a comprehensive view of your security alerts and security posture across your AWS accounts.
Note that GuardDuty must be manually turned on from the AWS console in each AWS region you want to support and then connected to Sophos Cloud Optix using the Integration instructions.
Optional but recommended AWS Security Services
Along with the above required AWS Security services, the below AWS services are also recommended as they provide additional information which can be used by Sophos security solutions and the MTR service to help protect customer environments.
-
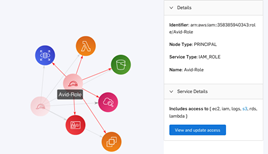
Amazon Detective: Amazon Detective automatically collects log data from AWS resources. It then uses device learning, statistical analysis, and graph theory to help you visualize and conduct faster and more efficient security investigations. Enabling this service allows Cloud Optix to include details highlighting IAM security misconfiguration and overprivileged users and roles, and also enables the IAM Visualization feature.
-
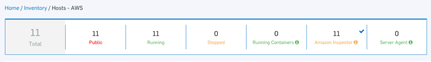
Amazon Inspector: Amazon Inspector tests the network accessibility of your Amazon EC2 instances and the security status of the applications that run on those instances. Amazon Inspector assesses applications for exposure, vulnerabilities, and deviations from best practices. Enabling Inspector allows Optix to filter the host inventory list to show EC2 instances for which there are Amazon Inspector findings. Click the Inspector icon in the "Actions" column to view findings for the last assessment run for that EC2 instance.
-
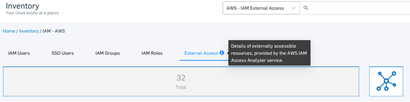
IAM Access Analyzer: AWS IAM Access Analyzer helps you identify the resources in your organization and accounts, such as Amazon S3 buckets or IAM roles, that are shared with an external entity.
-
AWS Systems Manager: AWS Systems Manager gives visibility and control of your AWS infrastructure. Systems Manager provides a unified user interface so you can view operational data from multiple AWS services and allows you to automate operational tasks across your AWS resources. The systems manager can also automatically Install Sophos Intercept X agents to EC2 instances, as described in the following KB. https://community.sophos.com/intercept-x-endpoint/f/recommended-reads/127860/how-to-auto-deploy-sophos-server-protection-on-aws-instances
Threat Protection, Monitoring, and Response Package Deployment Steps
- Purchase the Threat Protection, Monitoring, and Response Package via the AWS Marketplace.
- Receive license schedule email from Sophos. The license schedule contains details on the Sophos products purchased and should look similar to the below example.

- Sophos Central account signup and license activation. All Sophos products and services are managed from a Sophos Central account.
A. Go to https://central.sophos.com/ and sign in. If you don’t already have an account, then start a Sophos Central trial using the below link. https://secure2.sophos.com/en-us/products/sophos-central/free-trial.aspx
B. Once logged into the Sophos Central Admin console, look for your account name on the upper right of the user interface. Click the name and select Licensing.
C. On the licensing page, Click Apply License Key, copy/paste the License Key from your License schedule and then click Apply.
D. If you see an Apply License Key link, click it. Enter your key and click Apply.
E. If your account already has licenses for the features included in the key, you’ll see another dialog. This lets you choose how to use your new licenses.
i. Renew starts the new licenses when your current licenses expire.
ii. Change starts the new licenses now. We'll adjust the license term so all your licenses expire on the same date.
F. Click Apply again and confirm that the details on the licensing screen match those on the License Schedule. - Connect Sophos Cloud Optix to your AWS account(s):
A. Open a new tab in your browser and log in to your AWS console using an account with administrative-level permissions. These are needed to configure the connection between Optix and your AWS account and the AWS security services.
B. Navigate back to your Sophos Central console tab and click on Cloud Optix, located under the left-side menu under My Products.
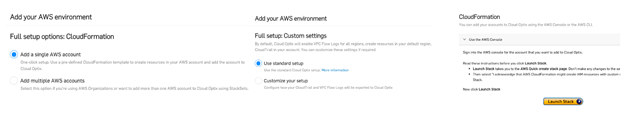
C. Once redirected to the Optix UI, you must be prompted to add a cloud environment. If not, click the ‘+ Add Environments’ option on the left side menu under Settings. Choose the Full Setup menu item, and then choose CloudFormation by clicking the ‘Go’ button to the right. You’ll then be prompted to connect either a single account or an AWS Organization and given the option to change default setup details. Once these steps are complete, click the ‘Launch Stack’ button to redirect to the AWS CloudFormation console page, where the Optix template is preloaded and ready to install. Follow on-screen instructions to complete it, or refer to the Optix help documentation for more details.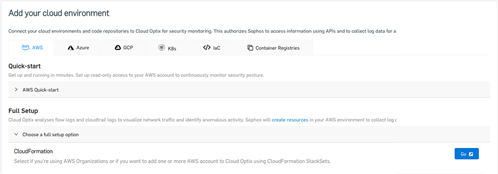
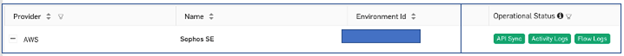
D. Once the CloudFormation stack has been launched, the setup and initial sync typically take 10-15 minutes to complete. Once done, the Optix Environments section should show the new environment connection along with green operational status indicators, as shown below. Note that the required AWS CloudTrail service is enabled as part of the Optix setup, with its status shown under ‘Activity Logs’.
If you encounter any issues or errors connecting Optix to your AWS accounts, kindly contact the Sophos public cloud team for assistance. Publiccloudteam@sophos.com - Run Optix AWS GuardDuty integration script: As discussed, the AWS GuardDuty service is a required AWS security service. Once turned on and configured using the Optix integration script, GuardDuty alerts will be sent to Cloud Optix. Detailed instructions on installing and running the script can be found in the Optix Integrations section.
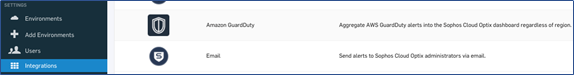
- Configure Optix to receive alerts from AWS Security Hub: As discussed, the AWS Security Hub service is required. Once turned on and configured using the Optix integration procedure, Security Hub alerts will be sent to Cloud Optix. Detailed instructions on installing and running the script can be found in the Optix Integrations section.
- Configure Intercept X Server policies and deploy agents
a. Configure ‘Best Practice’ Intercept X Server protection policies in Central (Please see Onboarding checklist section for details)
b. Use Optix Inventory>Hosts information to identify all EC2 instances in the attached AWS accounts.
c. Deploy Intercept X agents onto EC2 instances using the built-in link as shown below, or refer to KB in the onboarding checklist.
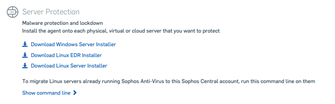
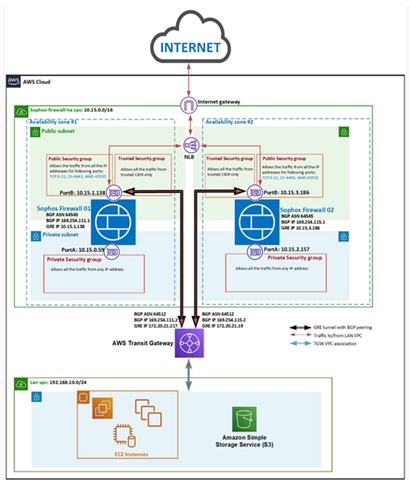
- Deploy an available pair of Sophos Firewalls into an AWS account: To comply with AWS architectural best practices, Sophos provides a high-availability solution that deploys a pair of Sophos Firewalls and utilizes an AWS Network Load Balancer and the AWS Transit Gateway service to ensure failover across availability zones. The solution is deployed via a Sophos-provided CloudFormation template available via AWS Marketplace and configured using the configuration guide.
- Configure XG FWs and connect to Central management: Once the Sophos firewalls are deployed, they must be configured to connect to the Sophos Central account.
Kindly refer to our how-to video showing the onboarding process and management of Sophos firewalls in the Sophos Central account.
Sophos Product Onboarding Configuration Checklist
|
Onboarding Item |
Policy/ Setting Detail |
Policy/ Setting Detail |
Notes or Comments |
Complete? |
|
General Setup |
|
|
https://docs.sophos.com/central/Customer/help/en-us/central/Customer/concepts/GettingStarted.html |
|
|
Customer has signed up for Sophos Central trial account |
|
|
https://secure2.sophos.com/en-us/products/sophos-central/free-trial.aspx |
|
|
Customer has logged into Sophos Central account and applied license keys |
|
|
https://docs.sophos.com/central/Customer/help/en-us/central/common/tasks/ActivateLicense.html |
|
|
Customer has configured Managed Threat Response preferences |
|
|
https://docs.sophos.com/central/MTR/newstartup/en-us/index.html |
|
|
Cloud Optix Setup |
|
|
|
|
|
Customer AWS accounts are connected to Cloud Optix |
|
|
https://docs.sophos.com/pcg/optix/help/en-us/pcg/optix/learningContents/AddEnvAWSCloudForm.html |
|
|
AWS required and optional security services are enabled and integrated with Optix |
|
|
https://docs.sophos.com/pcg/optix/help/en-us/pcg/optix/concepts/Integrations.html
|
|
|
Customer has reviewed the Optix AWS inventory section and is shown what AWS meta data information is captured |
|
|
|
|
|
Customer has reviewed Optix activity logs (CloudTrail) information |
|
|
|
|
|
At a minimum the following required Optix Policies are enabled: |
|
|
https://docs.sophos.com/pcg/optix/help/en-us/pcg/optix/concepts/OutOfBoxPolicies.html
|
|
|
Customer has reviewed Optix Integrations options and has chosen at least one option for Alerts |
|
|
https://docs.sophos.com/pcg/optix/help/en-us/pcg/optix/concepts/Integrations.html
|
|
|
Customer has reviewed Optix Host section and associated AWS GuardDuty information, and is shown how to filter on GuardDuty alerts in Alerts section |
|
|
|
|
|
Customer has reviewed different Optix Alert types including Anomaly and is shown how to filter and export |
|
|
|
|
|
Customer has reviewed Optix report settings section |
|
|
https://docs.sophos.com/pcg/optix/help/en-us/pcg/optix/concepts/WeeklySummaryReport.html |
|
|
Intercept X Server Policy Setup |
|
|
|
|
|
|
Threat Protection Policy |
Server Base Policy |
|
|
|
Runtime Protection |
|
|
|
|
|
Protect document files from ransomware (CryptoGuard) |
Enabled |
Enabled
|
|
|
|
Protect from remotely run ransomware |
Enabled
|
Enabled
|
|
|
|
Protect from Encrypting File System attacks |
Enabled
|
Enabled
|
|
|
|
Protect from master boot record ransomware |
Enabled
|
Enabled
|
|
|
|
Protect critical functions in web browsers (Safe Browsing) |
Enabled
|
Disabled |
|
|
|
Mitigate exploits in vulnerable applications |
Enabled
|
Enabled
|
|
|
|
Protect web browsers |
Enabled |
Enabled |
|
|
|
Protect web browser plugins |
Enabled |
Enabled |
|
|
|
Protect Java applications |
Enabled |
Enabled |
|
|
|
Protect media application |
Enabled |
Enabled |
|
|
|
Protect office applications |
Enabled |
Enabled |
|
|
|
Prevent credential theft |
Enabled |
Enabled |
|
|
|
Prevent code cave utilization |
Enabled |
Enabled |
|
|
|
Prevent APC violation |
Enabled |
Enabled |
|
|
|
Prevent privilege escalation |
Enabled |
Enabled |
|
|
|
Protect processes |
Enabled |
Enabled |
|
|
|
Prevent process hollowing attacks |
Enabled |
Enabled |
|
|
|
Prevent DLLs loading from untrusted folders |
Enabled |
Enabled |
|
|
|
Enable CPU branch tracing |
Enabled |
Disabled |
|
|
|
Dynamic shellcode protection |
Enabled |
Enabled |
|
|
|
Validate CTF Protocol caller |
Enabled |
Enabled |
|
|
|
Prevent side loading of insecure modules |
Enabled |
Enabled |
|
|
|
Deep Learning |
|
|
|
|
|
Enable deep learning |
Enabled |
Enabled |
|
|
|
Remediation |
|
|
|
|
|
Automatic cleanup of malware |
Enabled |
Enabled |
|
|
|
Send Endpoint Data to Sophos Central |
Enabled |
Enabled |
|
|
|
Runtime Protection |
|
|
|
|
|
Detect malicious connections to command and control servers |
Enabled |
Enabled |
|
|
|
Enable Sophos Security Heartbeat |
Enabled |
Enabled |
|
|
|
AMSI Protection |
Enabled |
Enabled |
|
|
|
Live Protection |
|
|
|
|
|
Use Live Protection to check the latest threat information from SophosLabs online |
Enabled |
Enabled |
|
|
|
Use Live Protection during scheduled scans |
Enabled |
Enabled |
|
|
|
Real-time Scanning - Local Files and Network Shares |
|
|
|
|
|
Remote files |
Enabled |
Enabled |
|
|
|
Real-time Scanning - Internet |
|
|
|
|
|
Scan downloads in progress |
Enabled |
Enabled |
|
|
|
Block access to malicious websites |
Enabled |
Enabled |
|
|
|
Detect low-reputation files |
Enabled |
Enabled |
|
|
|
Remediation |
|
|
|
|
|
Automatic cleanup of malware |
Enabled |
Enabled |
|
|
|
Real-time scanning Options |
|
|
|
|
|
Automatically exclude activity by known applications |
Enabled |
Enabled |
|
|
|
Detect malicious behavior (HIPS) |
Enabled |
Enabled |
|
|
|
Update Policy (Server) |
Update Management |
Base Policy - Update Management |
|
|
|
Scheduled Updates |
Disabled |
Disabled |
|
|
|
|
|
|
|
|
|
Intercept X Server Agent Deployment |
|
|
|
|
|
Please refer to the KB article for information on how to automate the deployment using the AWS Systems Manager service. |
|
|
|
|
|
Optix Inventory>Hosts ‘Server Agent’ column shows that agent is successfully deployed to all hosts. |
|
|
https://docs.sophos.com/pcg/optix/help/en-us/pcg/optix/concepts/ServerAgentIntegration.html |
|
|
|
|
|
|
|
|
Sophos Firewall on AWS Deployment |
|
|
|
|
|
Customer has subscribed to the Sophos FW High Availability AWS Marketplace listing |
|
|
https://aws.amazon.com/marketplace/pp/prodview-r3pjzf5gpoikm?ref_=srh_res_product_title
|
|
|
Customer has followed deployment steps detailed in KB |
|
|
|
|
|
Customer has connected deployed Firewalls to Sophos Central account |
|
|
|
|
|
|
|
|
|
|
|
Sophos Firewall on AWS Configuration |
|
|
https://www.sophos.com/en-us/support/products/xg-firewall/how-to-library.aspx
|
|
|
VPC and subnet objects have been created to match what is shown in Optix Inventory section |
|
|
|
|
|
Optix inventory and network visualization tools are used to identify any servers that are allowing inbound traffic on ports 80/443 |
|
|
|
|
|
Sophos Firewall IPS policy is enabled to protect all AWS subnets shown in Optix inventory |
|
|
|
|
|
Sophos Firewall WAF policy used to protect all servers using ports 80/443 |
|
|
|
|
|
Sophos Firewall Web policy is enabled and applied to all VPC subnets shown in Optix |
|
|
|
|
|
Sophos Firewall Sandstorm is enabled to scan any suspicious file downloads in to VPCs |
|
|
|
|
|
Sophos Firewall ATP is enabled to check for CnCs on all outbound traffic (DNS,HTTP and HTTPS) from VPC subnets |
|
|
|
|
|
Sophos Firewall has been configured to forward the events (Syslog) to a SIEM and SOAR Platform |
|
|
|
|
Revamped RR
[edited by: Erick Jan at 6:17 AM (GMT -7) on 18 Apr 2024]


